
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
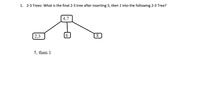
Transcribed Image Text:1. 2-3 Trees: What is the final 2-3 tree after inserting 5, then 1 into the following 2-3 Tree?
4,7
2,3
5, then 1
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps with 7 images

Knowledge Booster
Similar questions
- L[3.1] + [-2.6] + 1.9] O 2 3arrow_forwardcybersecurity course question We have found the source code to a high end IOT lock. Crack it. What programming language was this written in? What is the flag? CHECK = [124, 92, 164, 468, 124, 112, 68, 112, 468, 496, 500, 492, 492]function riddle(x) step1 = xor(x, 0x46) (step1 + 10) << 2end function main() println("I am very fancy. Can you solve my riddle") inp = readline() bytes = Int.(collect(inp)) solve = riddle.(bytes) if solve == CHECK println("Congrats") else println("Nope") endend if abspath(PROGRAM_FILE) == @__FILE__ main()endarrow_forwardPROGRAMMING EXERCISES: 4. How many double entries can aValues[MAX_A] store? 5. What is the value of aValues[2]? [Hint: the value is an address] 6. How many bytes are allocated to sentence?arrow_forward
- Process ABCDEFGHI JK Size (in KB) 4.27.2 2.5 4.5 3 2.7 1.5|2|3.62.2|1 Allocate(P) represents an allocation request by process P for the size shown in the above table Deallocate(P) is used to indicate deallocating the memory allocated to process P To represent memory, in square brackets, we use P to indicate a memory segment allocated to P and we use an integer to indicate a contiguous free part of memory. For example, after the following sequence of requests: Allocate(B), Allocate(G), Allocate(H), Deallocate(G) memory will look like this: B 8KB We represent this memory by [B,2,H,4]. free H 2KB 2KB For each of the following sequence of requests, apply the First-fit, Best-fit, and Worst-fit allocation schemes. Assume that for each algorithm, you always start at the beginning of the list and if there are multiple possible equal-size holes that can be selected by an algorithm, the first one is selected. Show the following: i. If all the requests can be satisfied, indicate the memory…arrow_forward2.3.3 Write out carefully how to compute [0, -1; 2, 1][1,-2,0;0,1,3] three ways, using: (a) Lemma 2.11arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY