
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Giventhe following assignment of some program’s virtual pages to physical pages in a system with 4 KiB byte pages, what physical memory address corresponds to virtual address 20000? (All values are given in decimal.)
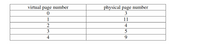
Transcribed Image Text:virtual page number
physical page number
3
1
11
4
3
4
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Write a short C program that declares and initializes (to any value you like) a double, an int, and a char. Next declare and initialize a pointer to each of the three variables. Your program should then print the address of, and value stored in, and the memory size (in bytes) of each of the six variables.arrow_forwardAssume that a memory module contains three holes of 10MB each. A sequence of 14 requests for 1MB each will be processed (See the diagram below). For each of the memory allocation methods listed below, draw a diagram representing how memory is allocated and determine the sizes of the remaining holes after all 14 requests have been satisfied. First fit Next fit C. Best fit d. a. b. Worst fit Hint - For the Next fit, the following allocation starts with the hole following the previous allocation 10 Mb 10 Mb 10 Mbarrow_forwardPlease help! Please take a look at the code I have provided as a attachment to this question. Please comment each line of code of the differences between program 1 and 2. What happens when you subtract one pointer from another? Is it subtracting the two addresses, or something else? How do you know? What happens when you increment a pointer? Compare and contrast how C-strings are laid out in memory compared to arrays of integers. What's one similarity and one difference? Show how the individual bytes of this integer array are laid out in memory. Thanks!arrow_forward
- Draw a picture illustrating the contents of memory, given the following data declarations: (You need to draw a diagram showing the memory addresses and their contents.) Assume that your data segment starts at 0x1000 in memory. Your answer should fill the table below and explain why. Addres Hexadecimal Hexadecimal S Value Value 0x1000 Ox |0x Ox Ox 0x Name: asciiz "Jones" Age: byte 48 Numbers: word 11, 20 Letter1: asciiz "Car" Letter2: .byte 25 Hexadecimal Value Hexadecimal Valuearrow_forwardThe program below uses pointer arithmetic to determine the size of a 'char'variable. By using pointer arithmetic we can find out the value of 'cp' and thevalue of 'cp+1'. Since cp is a pointer, this addition involves pointer arithmetic:adding one to a pointer makes the pointer point to the next element of the sametype.For a pointer to a char, adding 1 really just means adding 1 to the address, butthis is only because each char is 1 byte.1. Compile and run the program and see what it does.2. Write some code that does pointer arithmetic with a pointer to an int anddetermine how big an int is.3. Same idea – figure out how big a double is, by using pointer arithmetic andprinting out the value of the pointer before and after adding 1.4. What should happen if you added 2 to the pointers from exercises 1through 3, instead of 1? Use your program to verify your answer.#include <stdio.h>int main( ){ char c = 'Z'; char *cp = &c; printf("cp is %p\n", cp); printf("The character at cp is…arrow_forward1. Suppose an array with six rows and eight columns is stored in a row major order starting at address 20 (base 10). If each entry in the array requires only one memory cell, what is the address on the entry in the third row and fourth columns? What if each entry requires two memory cells?arrow_forward
- Q.2 Suppose a system has a logical address space of size 25 (m=5), a page size of 4 bytes, and a physical memory of 128 bytes. Given the following page table, find out the respective physical addresses for each of the logical address listed in Table 2. (Note: all addresses are expressed in decimal number system) Table 1: Page table 0 2 5 7 0 15 1 2 3 4 5 18 6 20 7 22 Table 2: Fill out this table with corresponding physical memory addresses Logical Address Physical Address 0 6 10 17 23arrow_forwardComplete the following sequence of three MIPS instructions: mul28: $t0, 28 mul $to ir by dragging four items from the below list into the correct spaces. Your code should implement a procedure, using the standard conventions covered in class for passing parameters and returning results, that returns the product of its argument and 28. $ra li sb $a0 $v0 Ib move lui Give a sequence of two MIPS instructions that branches to the target address represented by the name "loop" if and only if the contents of $$0 are less than or equal to the contents of $s1. Do this by dragging two items from the below list into the correct spaces. slt $at, $s1, $s0 bne $at, $zero, loop bltz $at, loop slt $at, $s0, $s1 beq $at, $zero, looparrow_forwardQuestion 9arrow_forward
- E In the following code block(Reference:Q11), you will a set of assembly instructions with corresponding line numbers (line numbers are for informational purpose only and they are not part of the source code). 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 mov edx, 5 dec ecx jmp LABEL1 mov eax, 1 LABEL1: mul edx jmp ecx mov edx, 0678h sub edx, eax jmp DWORD PTR [edx] neg ebx add ecx, ebx mov eax, 0 For each of the conditions/scenario listed below, indicate the corresponding line number (that cause or is associated with the condition/scenario). Enter 0 (Zero) if the condition is not caused by the block of code. 1) Memory indirect jump: type your answer... type your answer... type your answer... type your answer... 2) Register indirect jump: 3) Relative short jump: type your answer... 5) Two's complement type your answer... 4) Relative near jump: 6) Unreachable codearrow_forwardlist: .word 3, 0, 1, 2, 6, -2, 4, 7, 3, 7 size: .word 10 Develop a mips code with a Mars simulator that reads this sequence and counts those <0 (negative) and >=0 (zero or positive) and prints what it finds to the screen.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY