
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Hello I need help with the following question, I have provided my work that I have done and an example of completed work from the class.
This is the question I need help with.
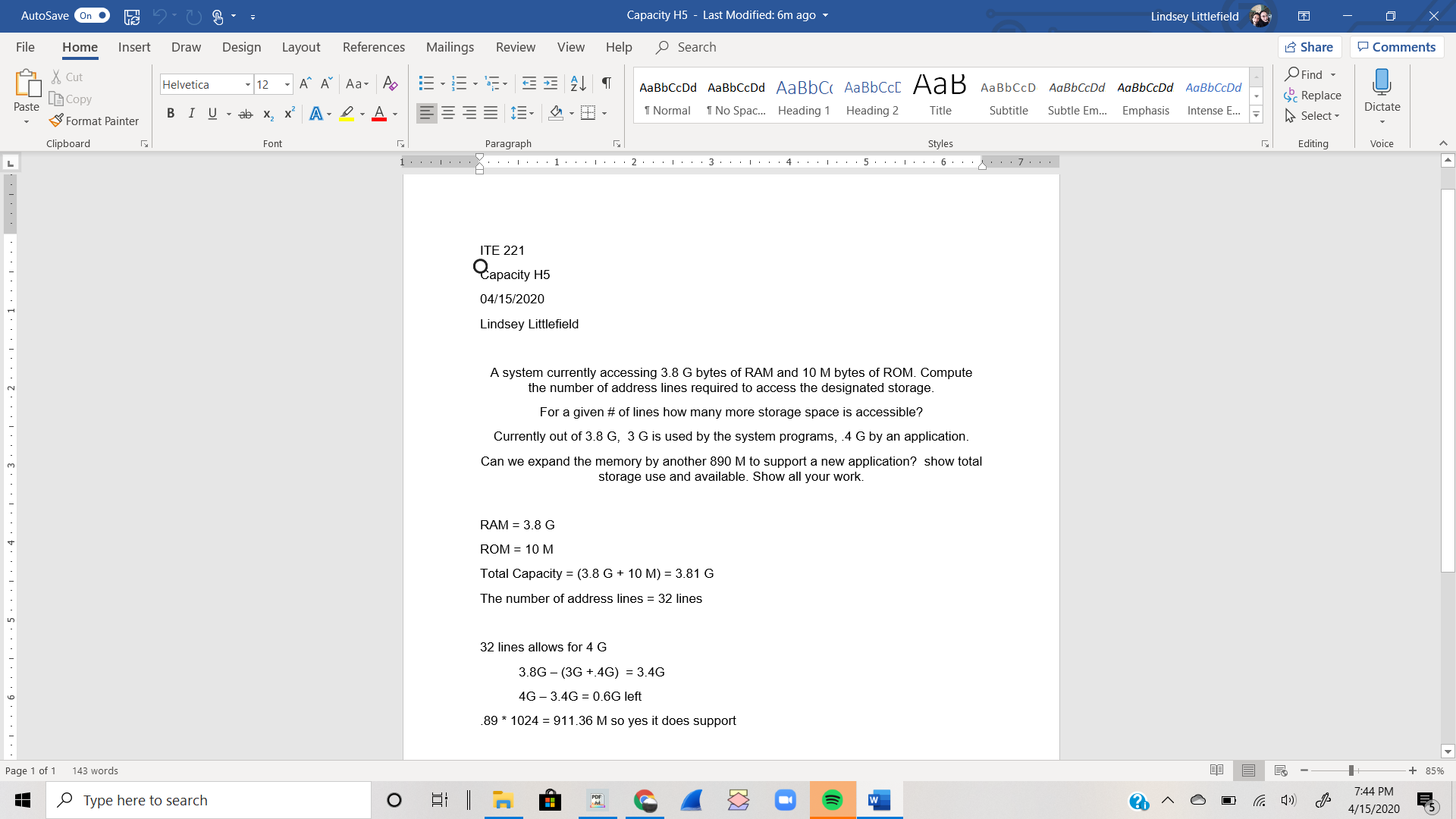
A system currently accessing 3.8 G bytes of RAM and 10 M bytes of ROM. Compute the number of address lines required to access the designated storage.
For a given # of lines how many more storage space is accessible?
Currently out of 3.8 G, 3 G is used by the system programs, .4 G by an application.
Can we expand the memory by another 890 M to support a new application? show total storage use and available. Show all your work.
Transcribed Image Text:AutoSave On
Capacity H5 - Last Modified: 6m ago -
Lindsey Littlefield
File
Home
Insert
Draw
Design
Layout
References
Mailings
Review
View
Help
O Search
A Share
P Comments
O Find -
S Replace
X Cut
- A^ A Aa- A
AаBЬСcDd AaBbСcDd AaBbC AаBЬСс[ Аа B АавьссD
Helvetica
12
AaBbCcDd AaBbCcDd AaBbCcDd
B Copy
Paste
E-
1 Normal
1 No Spac. Heading 1
Heading 2
Subtitle
Intense E...
Dictate
BIU - ab x, x A - l-A-
Title
Subtle Em...
Emphasis
A Select -
S Format Painter
Clipboard
Font
Paragraph
Styles
Editing
Voice
.. . . . . 1. . . |: . . 2.. . | · ..
ITE 221
Capacity
04/15/2020
Lindsey Littlefield
A system currently accessing 3.8 G bytes of RAM and 10 M bytes of ROM. Compute
the number of address lines required to access the designated storage.
2.
For a given # of lines how many more storage space is accessible?
Currently out of 3.8 G, 3 G is used by the system programs, .4 G by an application.
Can we expand the memory by another 890 M to support a new application? show total
storage use and available. Show all your work.
3.
RAM = 3.8 G
ROM = 10 M
Total Capacity = (3.8 G + 10 M) = 3.81 G
The number of address lines = 32 lines
32 lines allows for 4 G
3.8G – (3G +.4G) = 3.4G
4G – 3.4G = 0.6G left
.89 * 1024 = 911.36 M so yes it does support
Page 1 of 1
143 words
+ 85%
7:44 PM
O Type here to search
4/15/2020
Transcribed Image Text:O Zoom
Participants (14)
Q Find a participant
(5
LL
Lindsey Littlefield (Me)
ite221lecture - Word
File
Home
Insert
Design
Layout
References
Mailings
Review
View
O Tell me what you want to do..
Anwari, M H. 2 Share
AH Anwari, Hashem (Host)
X Cut
P Find -
Calibri
11 - A A Aa -
АавьСсDc AаBьссDс AaBbC AаBbCc[ Aав давьссС АавЬСсD AaвьссD
暗Copy
abc Replace
Paste
U - abe X, x’ A - aly , A-
1 Normal
I No Spac. Heading 1
Heading 2
Subtitle
Subtle Em. Emphasis
ws Waqas Siddiqui
Title
Format Painter
A Select-
Clipboard
Font
Paragraph
Styles
Editing
A
aziz
o Example
>>
...
Raise Hand
yes
go slower
go faster
no
more
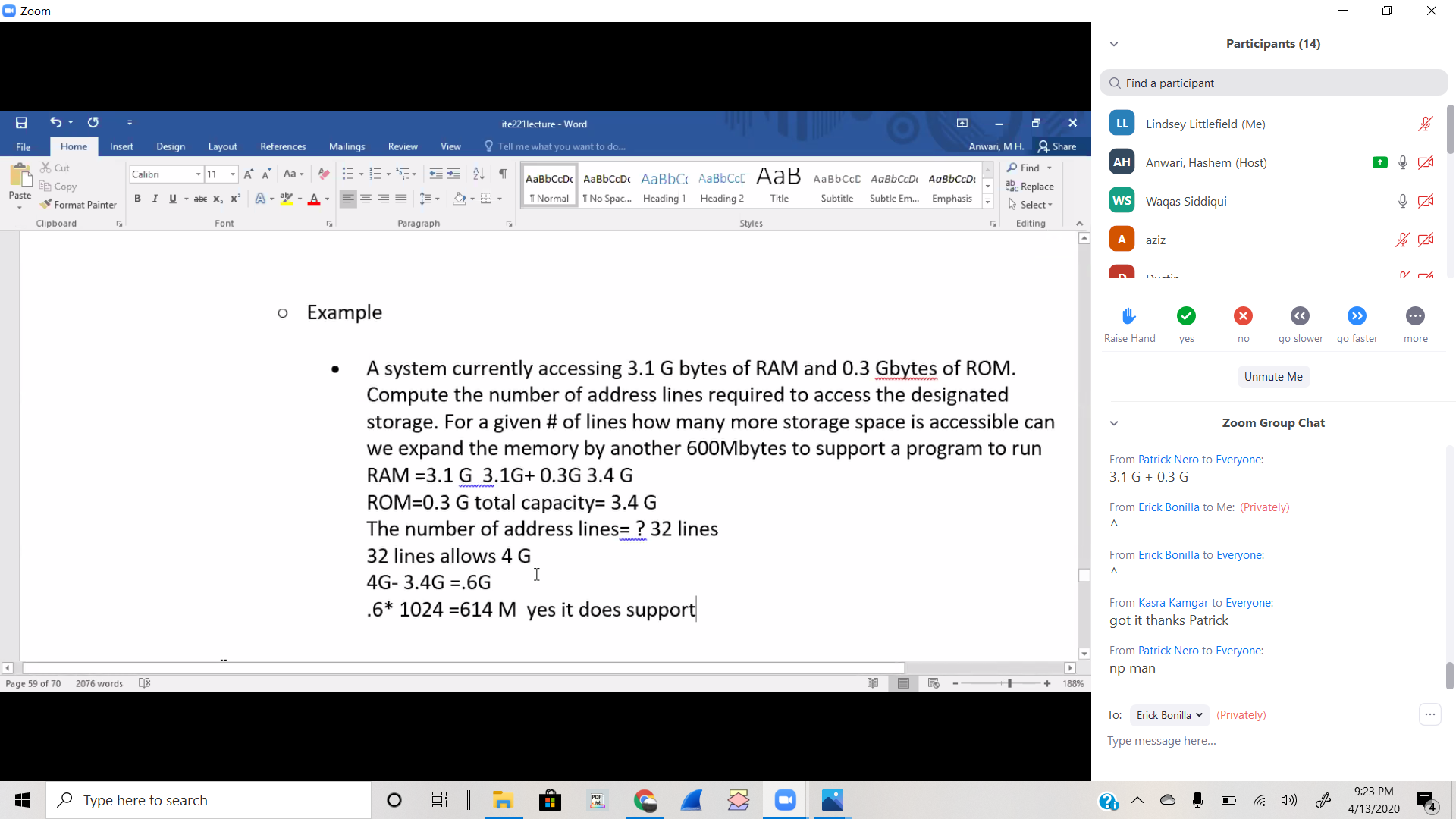
A system currently accessing 3.1 G bytes of RAM and 0.3 Gbytes of ROM.
Compute the number of address lines required to access the designated
storage. For a given # of lines how many more storage space is accessible can
we expand the memory by another 600Mbytes to support a program to run
Unmute Me
Zoom Group Chat
From Patrick Nero to Everyone:
RAM =3.1 G 3.1G+ 0.3G 3.4 G
3.1 G + 0.3 G
ROM=0.3 G total capacity= 3.4 G
From Erick Bonilla to Me: (Privately)
л
The number of address lines= ? 32 lines
32 lines allows 4 G
From Erick Bonilla to Everyone:
4G- 3.4G =.6G
.6* 1024 =614 M yes it does support
From Kasra Kamgar to Everyone:
got it thanks Patrick
From Patrick Nero to Everyone:
np man
Page 59 of 70
2076 words
188%
To:
Erick Bonilla v (Privately)
Type message here...
9:23 PM
O Type here to search
PDF
4/13/2020
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Hello. Please answer the attached MIPS computer architecture question and all its parts correctly. You do not have to give a lengthy explanation for each part. *If you answer the question and all its parts correctly, I will give you a thumbs up. Thanks.arrow_forwardRandom access memory (RAM) is a kind of computer memory that works in a variety of ways. Separate the items in your list into two lists. It's unknown what role it plays in software storage in embedded computers. Explain.arrow_forwardPlease explain on a paper Thank you for your helparrow_forward
- Assume you now have 1kB of memory, i.e. the memory address space runs from 0 to 1023. The starting address of the first word is 0, the second word is 4, the third word is 8, and so on. The last word comprising 4 bytes resides in addresses 1020, 1021, 1022, 1023. Thus, the last word starts at 1020, which is a multiple of 4. Now assume the same 1kB of memory but now, word size is 64 bits. The starting address of the first word is 0, the second, third, and last word starts at? my answer: (correct) the second is equal to = 8 the third is equal to = 16 help me find the last wordarrow_forwardAssume that a memory module contains three holes of 10MB each. A sequence of 14 requests for 1MB each will be processed (See the diagram below). For each of the memory allocation methods listed below, draw a diagram representing how memory is allocated and determine the sizes of the remaining holes after all 14 requests have been satisfied. First fit Next fit C. Best fit d. a. b. Worst fit Hint - For the Next fit, the following allocation starts with the hole following the previous allocation 10 Mb 10 Mb 10 Mbarrow_forwardSuppose a program’s 15-th logical instruction (counting starts from zeroth) is at physical address 1234ABDE16 in the RAM. (contents of any logical address fits into any physical address) What is the physical address in the RAM where the program has been loaded? What is the physical address in the RAM of the last instruction of the program if it has 37 logical instructions altogether?arrow_forward
- Please help! Please take a look at the code I have provided as a attachment to this question. Please comment each line of code of the differences between program 1 and 2. What happens when you subtract one pointer from another? Is it subtracting the two addresses, or something else? How do you know? What happens when you increment a pointer? Compare and contrast how C-strings are laid out in memory compared to arrays of integers. What's one similarity and one difference? Show how the individual bytes of this integer array are laid out in memory. Thanks!arrow_forwardDraw a picture illustrating the contents of memory, given the following data declarations: (You need to draw a diagram showing the memory addresses and their contents.) Assume that your data segment starts at 0x1100 in memory. Your answer should fill the table below and explain why. -- photo attached below Thank you for your help!arrow_forwardCase Study Assume a computer system has a main memory of 256 Bytes. The following is a memory byte-access trace history of a program run on this system. For example, as it is shown, the program first accesses memory address 0000 0000, and then it accesses memory address 0000 0001 and so on. Note the memory addresses are represented in binary: 00000000, 00000001, 00000010, 00000011, 00001000, 00010000, 00010001, 00000100, 00000101, 00000110, 00000111, 00001001, 00001010, 00001011, 00001100, 00001000, 00001001, 00001010, 00011100, 00011101. Q3. Assume the system has a 16-Byte direct mapped unified L1 cache with a block size of 2 Bytes. The following table shows how the cache looks like after the first access to the memory is finished. Please show; in the provided table, how it looks like after the 20th access is finished. You could ignore the "Data" Column. (Add or remove Rows/Columns in the provided table for your answer, as you see fit). Cache contents after the 1st access: Cache Index…arrow_forward
- Given a computer with 300 memory locations, each 18-bit assessable, how many bits of addressing are needed? Given a computer with 10-bit addressability and 5 bits for the address, what's the maximum number of memory this computer can have in bits?arrow_forwardLet's double the size of the address field from 32b to 64b. What's the largest decimal value now? How might you organize this for readability?arrow_forwardQuestion 9arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY