
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
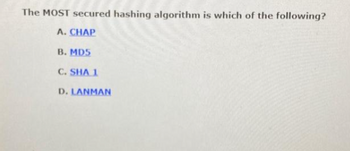
Transcribed Image Text:The MOST secured hashing algorithm is which of the following?
A. CHAP
B. MD5
C. SHA 1
D. LANMAN
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- The collision resolution technique that allows for dynamic growth of the hash table is: O a. buckets O b. double hashing O c. linear probing O d. chainingarrow_forwardUse the following values to answer the questions bellow 66 47 87 900 126 140 145 500 177 285 393 395 467 566 620 735Store the values into a hash table with ten buckets, each containing three slots. If a bucket is full, use the next (sequential) bucket that contains a free slot.arrow_forwardSuppose you have a hash table of size N = 64, and you are using quadratic probing. The keys in your hash are 4-digit integers (0000 through 9999) and your hash function is h(k) = (the sum of the digits in k). Assuming keys are uniformly random over the range 0000 to 9999, is this a good hash function? (Answer true for yes, false for no). True Falsearrow_forward
- The Java hash function for Strings computes a hash code based on a fixed maximum number of characters of the string. Given that Strings have no meaningful upper bound in length, describe how an effective, constant-time hashing algorithm can be constructed. (Hint: If you were to pick, say, eight characters to represent a string of length l, which would you choose?)arrow_forwardWhich of the following is not a collision resolution technique in a Hash Table? Group of answer choices Chaining Linear Probing Quadratic Probing Hashingarrow_forward). This problem is about the chaining method we discussed in the class. Problem 3 (, Consider a hash table of size N = 11. Suppose that you insert the following sequence of keys to an initially empty hash table. Show, step by step, the content of the hash table. Sequence of keys to be inserted:arrow_forward
- - In class HashTable implement a hash table and consider the following:(i) Keys are integers (therefore also negative!) and should be stored in the tableint[] data.(ii) As a hash function take h(x) = (x · 701) mod 2000. The size of the table istherefore 2000. Be careful when computing the index of a negative key. Forexample, the index of the key x = −10 ish(−10) = (−7010) mod 2000 = (2000(−4) + 990) mod 2000 = 990.Hence, indices should be non-negative integers between 0 and 1999!(iii) Implement insert, which takes an integer and inserts it into a table. Themethod returns true, if the insertion is successful. If an element is already inthe table, the function insert should return false.(iv) Implement search, which takes an integer and finds it in the table. The methodreturns true, if the search is successful and false otherwise.(v) Implement delete, which takes an integer and deletes it form the table. Themethod returns true, if the deletion is successful and false otherwise.(vi)…arrow_forwardIn this task, two hash tables should should be implemented. You can follow the followinginstructions:- In class HashTable implement a hash table and consider the following:(i) Keys are integers (therefore also negative!) and should be stored in the tableint[] data.(ii) As a hash function take h(x) = (x · 701) mod 2000. The size of the table istherefore 2000. Be careful when computing the index of a negative key. Forexample, the index of the key x = −10 ish(−10) = (−7010) mod 2000 = (2000(−4) + 990) mod 2000 = 990.Hence, indices should be non-negative integers between 0 and 1999!(iii) Implement insert, which takes an integer and inserts it into a table. Themethod returns true, if the insertion is successful. If an element is already inthe table, the function insert should return false.(iv) Implement search, which takes an integer and finds it in the table. The methodreturns true, if the search is successful and false otherwise.(v) Implement delete, which takes an integer and deletes it…arrow_forwardPlease help questions below: How good is the provided hash function--are we really getting constant time operations with our hashmap? Explain. What is one other way you could implement the hash function? Anything creative is acceptable in this answer, but justify how your hashing function works. If I have to resize the hashmap to add more buckets, what is th Big-O complexity when you resize? (Explain why) What is 'open addressing' in regards to hash maps and hash tables?arrow_forward
- The best technique of hashing when memory space is not a problem is O Linear probing O Quadratic probing O Double hashing O Separate chainingarrow_forwardYour computer-scie... Your computer-scien... ΤΣ1 tudents | University x A Quiz: Final Exam is://uispringfield.instructure.com/courses/6194/quizzes/33188/take lents | University x /uispringfield.instruc Consider the following cuckoo hashing with 2 tables. Both tables have a size of 11. The hashing function of the first table is: h1 (k) = k mod 11 Consider the f The hashing function of the second table is: 'e a size of 11. h2 (k) = L mod 11 (Note: mod is the modulo operation. It returns the remainder of a division. The hashing fu For example, "3 mod 11 = 3" and "20 mod 11 = 9".) The following sequence of insert operations are performed: h1 (k) = • Insert 50 The hashing fu • Insert 53 • Insert 75 h2(k) Which of the following is TRUE after the above operations? 囲arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education