
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Consider the following DFA (M) over the alphabet Σ = {a, b}. Create an initialized GNFA that is equivalent to M.
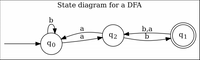
Transcribed Image Text:State diagram for a DFA
b
a
b,a
а
q2
Expert Solution
arrow_forward
Step 1
output of the DFA is
b*a(ab*a)*b(ab+bb)*
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 1 images

Knowledge Booster
Similar questions
- Finally, we will do some simple analysis – ranking of words. Write a function word_ranking(corpus, n, sort_index) which takes input parameters corpus (type list), n (type int), and sort_index (type int) and returns a list containing tuples of words and their frequencies in the top n of words. Here, corpus is a list of sentences. n is the number of ranked words to return. The resulting list should then be sorted based on the sort_index; sort_index = 0 should sort the list of tuples in ascending alphabetical order, while sort_index = 1 should sort the list of tuples by the frequencies in descending order. All other numeric values for sort_index should return an empty list (don't need to consider non-integer inputs). For example, we have: corpus = ['hi hi hi hi', 'hello hello say bye', 'bye bye']n = 3sort_index = 1 The function should return: [('hi', 4), ('bye', 3), ('hello', 2)] While sort_index = 0 should return: [('bye', 3), ('hello', 2), ('hi', 4)] You can assume n would…arrow_forwardGiven the following CFG S → OB A → 1AA|A B → OAA The following strings can be generated except i. 001 ii. 000 iii.0011 iv. 01 O A. i and iii O B. i and ii O C. iv only O D. ii onlyarrow_forwardGenerate an intermediate representation of the given expression. How can it be represented using indirect triples? (a – b) * + ((b/d) * (c-a)) note: subject: compailer concepts deptt: cs/Itarrow_forward
- please do j, k, and l thanks in advancedarrow_forwardTask Given a string str and one of its character ch, the coverage of ch is computed as the number of elements between its leftmost and rightmost appearances (inclusive). For example, if str="babaac" and ch='a' then its leftmost and rightmost appearances occur at indices 1 and 4, respectively. Thus, the coverage of ch is 4. In this example, if ch='b' then its coverage is 3 since its leftmost and rightmost appearances occur at indices 0 and 2. Also, if ch='c', its coverage is 1. Write a function named findMaxCoverage that . takes a string (str) and its size (n) as given below int findMaxCoverage (char str[], int n) . returns the maximum coverage in str. For example, . if str "babaac", then the call findMaxCoverage (str, 6) should return 4, since this is the maximum of all character coverages found in the string, i.e., coverage of 'a' is 4, coverage of 'b' is 3, coverage of 'c' is 1. • if str="abcdefg", then the call findMaxCoverage (str, 7) the function should return 1 since all…arrow_forwardQ2: Design a PDA for accepting a language {0^1m0n | m, n>=1} give the ID form as we explain in the lecture. Apply the string "00011000" on this PDA using ID transitions.arrow_forward
- C PROGRAMMING Implement dijkstras alorithm Check that the Graph graph, and starting node, id, are valid• Create the set S containing all the networks (vertices) except the source node (you might wantto use an array for this.• Create an array to represent the table D and initialise it with the weights of the edges from thesource node, or infinity if no edge exists. You should use the constant DBL_MAX to representinfinity.• Create an array to represent the table R and initialise it with the next hops if an edge existsfrom the source, or 0 otherwise.• Then repeatedly follow the remaining rules of Dijkstra’s algorithm, updating the values in D andR until S is empty.• Each of the values required to complete the above can be found by calling the variousfunctions (get_vertices(), get_edge(), edge_destination(), edge_weight(), etc.)in the supplied graph library.• Once Dijkstra’s algorithm has run, you will need to create the routing table to be returned byallocating enough memory for the…arrow_forward1. Analyze the word finder with wild card characters scenario to form the algorithm and compute the time complexity. You are given a list of characters with size n, m. You need to read character data provided as input into this list. There is also a list of p words that you need to find in the given problem. You can only search in left, right, up and down direction from a position. There are two wild characters *' and '+' ,if there is any instance of wild card characters for example '+' appears you can match whatever character in your word that you are searching at this position (only one character). Similarly, if you got wildcard *' you can skip any number of characters ( A sequence of characters not necessary same in between the characters) but the last character should be matched in the given data. This means you are not allowed to match a first and last character with *' wildeard. Input: The first line of the input will give you two integers n and m. From the next line you will get…arrow_forwardGiven the following CFG S → OB A → 1AA|A B → OAA The following strings can be generated except i. 001 ii. 000 iii.0011 iv. 01 O A. i and iii O B. i and ii O C. iv only O D. ii onlyarrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY