
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
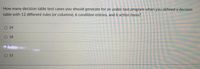
Transcribed Image Text:How many decision table test cases you should generate for an under-test program when you defined a decision
table with 12 different rules (or columns), 6 condition entries, and 6 action items?
O 24
O 18
O 12
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- I'm asking for help with different perspectives on purpose. Also, you do not have to complete the code, I’m posting the entire question in order for the question to be clear. Sorry if you see this question ask more than once. Objectives: The main objective of this assignment is to assess the student’s ability to provide a complete Black-Box testing plan for a computer program. Description: you will need to design a complete Black-Box testing plan for the following program. Instead of changing passwords every semester, students will now change passwords once a month. Unfortunately, the school has realized that many students are bad at picking their passwords. Ideally, passwords alternate between letters, numbers, and symbols. However, most students and faculty pick passwords such as “12345password”. To make matters worse, when students and faculty are forced to change their password, usually only a single character is added to the end of their previous password. Due to this…arrow_forward13. Factorial Implementation What is incorrect with the following implementation of factorial: def factorial(n): return n* factorial(n-1) Pick ONE option Nothing is wrong The return value should be n+ factorial(n-1) The return value should be factorial(n-1) * factorial(n-2) ) A base case is missing Clear Selection loxituarrow_forwardProcess Scheduling: Select all statements below that are true The waiting time is included in the turnaround time. In interactive systems, short response times are unimportant. The time taken in an interactive program from the issuance of a command to the commencement of a response to that command is known as the response time. The response time is the time required for a particular process to complete, from submission time to completion. Throughput is the number of processes executed per time unit. The concept of virtual (run)time in the Completely Fair Scheduler is used to ensure fairness in the allocation of processor capacity.arrow_forward
- Computer Science Part C: Interactive Driver Program Write an interactive driver program that creates a Course object (you can decide the name and roster/waitlist sizes). Then, use a loop to interactively allow the user to add students, drop students, or view the course. Display the result (success/failure) of each add/drop.arrow_forwardA for construct is an iterative loop that processes a list of items. As a consequence, it continues to process items as long as there are things to process. Is this a true or false statement?arrow_forwardLocal declarations are those that are stored in the computer's memory, but how are they stored? Using local declarations is unnecessary if the same goal can be accomplished without them. When reference parameters may be used in any function, why bother with value parameters? When it comes to processing programme data, how important are value parameters?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY