
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
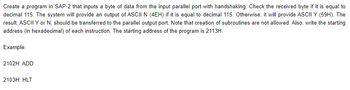
Transcribed Image Text:Create a program in SAP-2 that inputs a byte of data from the input parallel port with handshaking. Check the received byte if it is equal to
decimal 115. The system will provide an output of ASCII N (4EH) if it is equal to decimal 115. Otherwise, it will provide ASCII Y (59H). The
result, ASCII Y or N, should be transferred to the parallel output port. Note that creation of subroutines are not allowed. Also, write the starting
address (in hexadecimal) of each instruction. The starting address of the program is 2113H.
Example:
2102H: ADD
2103H: HLT
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps with 2 images

Knowledge Booster
Similar questions
- Write a program in C that can convert a bit stream of a message into a frame by using Hamming coding. The bit stream is the input parameter of the program. For example, given an input parameter as 1001000, the correct output of the frame is 00110010000. Input bit stream will have 1 to 64 bits. Some self-testing examples are:Input 1001000; output 00110010000Input 1101001100110101; output 011110110011001110101Input 1010101; output 11110100101Input 11111111; output 111011101111 Write a program in C that can convert a bit stream of a message into a frame by using CRC. The bit stream is the first input parameter of the program, which will have 8 to 128 bits. The generator function is the second input parameter of the program, which will have 4 to 16 bits. For example, if the generator function is x^4 + x + 1, the second input will be 10011. The output should be the transmitted bit stream with its CRC checksum bits; see example in Figure 3-9 in the textbook. Some self-testing examples…arrow_forwardConstruct a TM M4 which accepts the language { w2w | w in {0,1}* }. This means, any input that comprises two copies of a binary string w separated by a single 2 symbol should be accepted. Any other input should be rejected. The input alphabet is {0,1,2}. The tape alphabet contains 0, 1, 2, _ and you may use additional symbols 3, 4, 9 if you wish (M4 can be constructed comfortably with just one additional symbol 3). The tape's content after M4 halts does not matter. Submit a representation of M4 as described above. ••*/arrow_forwardi have this code .ORIG x3000SetupLEA R0, InfoPUTS ADD R6, R6, #5; Init Main Loop counter (loop 5 times) ;Print first 2 Fib values before starting;----- Your Code Here -----;LD R1, #0 JSR printNum LD R2, #1 JSR printNumJSR printNum ; Print the value in R2 JSR printCommaSpace ; Print comma and space ;----- End Your Code Here -----;;Loop and call subroutines to calculate each subsequent value in the sequence;Exit the loop once all single-digit values in the sequence have been printedMainLoop ;----- Your Code Here -----; JSR calcNextFib JSR printNum JSR printCommaSpaceADD R6, R6, #-1BRz Done BR MainLoop ;----- End Your Code Here -----; Done HALT ;-----------------------------------;Subroutines;----------------------------------- ;Uses R1 and R2 to calc next value in Fibonacci sequence;When complete, Fib2 (R2) will contain the new Fib number;and Fib1 (R1) will contain the previous value of Fib2 (R2)calcNextFib;----- Your Code Here -----;ST R1, SaveR3 ; Save R1ST R2,…arrow_forward
- In C, both long x and int *y are 8-byte values. How can we can tell which one is which in the assembly compiled from the C? (l.e., what is true of one but not the other? If several answers seem correct, pick the most precise option.) A. x is stored in a register, y in memory B. x is modified using addq, y using addl C. x may be an argument to add but y won't be D. When an argument of mov, a register storing x will never be inside parentheses E. When an argument of mov, a register storing y will always be inside parenthesesarrow_forwarda. Use an interactive Python session (shell/IDLE) to print out a line of 11 stars 7 times (so there will be 7 lines of output with each line containing 11 stars). b. Write a function that does the same thing as above, having each line printed individually. c. Write a function that uses a loop to do the same thing.arrow_forwardWrite a program that swaps 5th~11th bits in data_a with 25th~31th bits in data_bYour program must work for any data given, not just the example belowIn this question, we assume that the positions of bits count from right to left.That is, the first bit is the least significant bit.data_a DCD 0x77FFD1D1data_b DCD 0x12345678arrow_forward
- # Write a MIPS assembly program that converts upper case characters to lower case. Given an ASCII string with lower case and upper case ASCII characters a-z or A-z. no number. Change the upper case characters to lower case, modify this code, to convert all upper case characters to lower case for ASCII string.. .text main: li $v0,11 la $t1,str loop: lb $a0,0($t1) beqz $a0,done blt $a0,0x61,next bgt $a0,0x7a,next syscall next: addi $t1,$t1,1 j loop done: li $v0,10 syscall .data str: .asciiz "abH1r2C9mXd"arrow_forwardYou must complete this in Python and the programs should not take any command-line arguments. You also need to make sure your programs will compile and run in at least a Linux environment. In this problem, you need to implement operation bit encoding for Assembly instructions. Given a line of text, your program should check whether it is a valid Assembly instruction type. If it is, your program should print out the opcode and optype of that instruction type; if the line of text is not exactly a valid Assembly instruction, your program should skip it and move to the next line of input without printing anything. Input Format The input to the program will consist of some number of lines. Each line contains some text, either a valid Assembly instruction type (with no extra whitespace or other characters, e.g. READ on a line by itself) or some other text. Constraints There are no specific constraints on the length or number of lines. They will be in a reasonable limit, as demonstrated by…arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY