
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
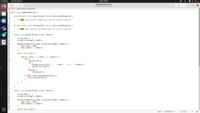
Consider the BadReaderWriter.java program attached with this homework. The program has three threads, namely, one reader thread and two writer threads, and they all access the same list of numbers. The reader thread reads the list and prints it to the terminal. The writer threads append numbers to the list. At any point in time, if either of the writer threads finds that the list contains n elements, then it appends the number n + 1 to the list.
Run this program, examine the output, and identify the problems.
Fix these problems by implementing the acquireLock() and releaseLock() methods in the code.
![Activities
2 Text Editor
Dec 6 09:28
BadReaderWriter.java
-/Downloads/Telegram Desktop
Open
Save
41
42
43
44
45
stattc class WriterThread extends Thread {
46
47
String name = "":
ArrayList<Integer> numbers;
48
49
50
51
52
53
WriterThread(String name, ArrayList<Integer> numbers) {
this.name = name;
this.numbers numbers;
15
54
55
public votd run() {
56
57
for (int count = 0; count < 10; count++) {
58
try {
acqutrelock();
try {
Integer entry = numbers.stze() + 1;
numbers.add(entry);
Systen.out.printin(">>
59
60
61
62
63
+ name +" added: " +
+ entry);
64
Systen.out.flush();
65
66
67
68
finally {
releaselock();
69
70
} catch (InterruptedException e) {
e.printstackTrace();
71
72
73
74
75
76
77
78
79
80
public static void main(String[] args) (
81
82
ArrayList<Integer> listofNumbers = new Arraylist<Integer>();
83
84
ReaderThread t1 = new Reader Thread("reader1", ltstofNumbers);
85
86
WriterThread t2 = new Writer Thread("writer1", listofNumbers);
87
88
89
writerThread t3 = new WriterThread( "writer2", ltstofNumbers);
t1.start();
t2.start();
t3.start();
90
91
92
93
94
95 }
Java Tab Width: 8
Ln 1, Col 1
INS](https://content.bartleby.com/qna-images/question/eadd2534-1307-4273-82e3-a888d564b7e7/0f900966-5b35-4a77-8c2d-d0cfb05dcc1a/1hrpnu_thumbnail.jpeg)
Transcribed Image Text:Activities
2 Text Editor
Dec 6 09:28
BadReaderWriter.java
-/Downloads/Telegram Desktop
Open
Save
41
42
43
44
45
stattc class WriterThread extends Thread {
46
47
String name = "":
ArrayList<Integer> numbers;
48
49
50
51
52
53
WriterThread(String name, ArrayList<Integer> numbers) {
this.name = name;
this.numbers numbers;
15
54
55
public votd run() {
56
57
for (int count = 0; count < 10; count++) {
58
try {
acqutrelock();
try {
Integer entry = numbers.stze() + 1;
numbers.add(entry);
Systen.out.printin(">>
59
60
61
62
63
+ name +" added: " +
+ entry);
64
Systen.out.flush();
65
66
67
68
finally {
releaselock();
69
70
} catch (InterruptedException e) {
e.printstackTrace();
71
72
73
74
75
76
77
78
79
80
public static void main(String[] args) (
81
82
ArrayList<Integer> listofNumbers = new Arraylist<Integer>();
83
84
ReaderThread t1 = new Reader Thread("reader1", ltstofNumbers);
85
86
WriterThread t2 = new Writer Thread("writer1", listofNumbers);
87
88
89
writerThread t3 = new WriterThread( "writer2", ltstofNumbers);
t1.start();
t2.start();
t3.start();
90
91
92
93
94
95 }
Java Tab Width: 8
Ln 1, Col 1
INS
Transcribed Image Text:Activities
2 Text Editor
Dec 6 09:28
BadReaderWriter.java
-/Downloads/Telegram Desktop
Оpen
Save
1 import java.util.ArrayList;
2
3 public class BadReaderwriter {
private static void acquirelLock() throws InterruptedException {
6.
7
// TODO: Add code for acquiring lock for critical section
8
private static void releaselLock() throws InterruptedException {
10
11
12
// TODO: Add code for releasing lock for critical section
13
15 14
15
stattc class ReaderThread extends Thread {
16
String name = "";
ArrayList<Integer> numbers%3;
17
18
19
Reader Thread (string name, ArrayList<Integer> numbers) {
this.name = name;
this.numbers = numbers;
20
21
22
23
24
25
26
27
28
29
30
public votd run() {
for (int count = 0; count < 20; count++) {
try {
acquirelock();
try {
Systen.out.println(">>>
Systen.out.flush();
read: "
+ numbers);
31
+ name +
32
33
34
35
36
37
finally {
releaselock();
} catch (InterruptedException e) {
e.printstackTrace();
38
39
40
41
42
43
44
45
46
47
48
49
stattc class WriterThread extends Thread {
String name = "";
ArrayList<Integer> numbers;
50
51
writerThread(String name, ArrayList<Integer> numbers) {
this.name = name;
this.numbers numbers;
}
52
53
54
55
public votd run() (
Java Tab Width: 8
Ln 1, Col 1
INS
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 4 steps with 5 images

Knowledge Booster
Similar questions
- Given that an ArrayList of Strings named friendList has already been created and names have already been inserted, write the statement necessary to change the name "Tyler", stored at index 8, to "Bud". This is needed in Javaarrow_forwardConsider the BadReaderWriter.java program attached with this. The program has three threads, namely, one reader thread and two writer threads, and they all access the same list of numbers. The reader thread reads the list and prints it to the terminal. The writer threads append numbers to the list. At any point in time, if either of the writer threads finds that the list contains n elements, then it appends the number n + 1 to the list. Run this program, examine the output, and identify the problems.Fix these problems by implementing the acquireLock() and releaseLock() methods in the code.arrow_forwardWrite a Java program that will allow the user to play a hangman game repeatedly until theychoose to stop. The game should randomly choose a secret word from a pre-set list of wordsfor the user to guess. Store the list of words available for play in an array so you can randomlychoose them by index during game play.During a turn, the user will guess one letter at a time. Each letter in the secret word shoulddisplay as an asterisk until the letter is guessed by the user. When a correct letter is guessed,the letter should be displayed in the correct position in place of the asterisk. The user hangshimself with the 8th wrong guess and loses the game.Make a character array to hold the characters and asterisks representing the word beingguessed. You can change the contents of this array as the letters are guessed and revealed. Inother words, this array can be used to display the current state of the secret word each round.Here is the list of words the game should choose from for the secret…arrow_forward
- Java Programming This week's project involves a text file with that holds all of the novel Don Quixote*, by Miguel Cervantes. The text file has been heavily processed. It contains only lowercase letters, spaces, and new lines. That is a good format for counting words. Write code that reads through the text file one word at a time using a Scanner, and the next() method. Put the words into a HashMap, where the words are used as keys, and the values are Integers used to keep track of how many times the words occur in the text. If the text was "one fish two fish red fish blue fish one two three" then the HashMap would look like this: key value "one".... 2 "fish"... 4 "two".... 2 "red".... 1 "blue"... 1 "three".. 1 Once you have created such a HashMap for the whole of the text you can write logic that prints out the answers to these questions: How many times does each of…arrow_forwardin java please Create a method for the client perspective to determine if a ListInterface has the same numbers in the same order. method header: public static boolean equivalentLists(ListInterface<Integer> numberListInterface, List<Integer> numberList)arrow_forwardWrite a Console Java program that inserts 25 random integers in the range of 0 to 100 into a Linked List. (Use SecureRandom class from java.security package.SecureRandom rand = new SecureRandom(); - creates the random number objectrand.nextInt(100) - generates random integers in the 0 to 100 range)Using a ListItreator output the contents of the LinkedList in the original order. Using a ListItreator output the contents of the LinkedList in the reverse order.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY