
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
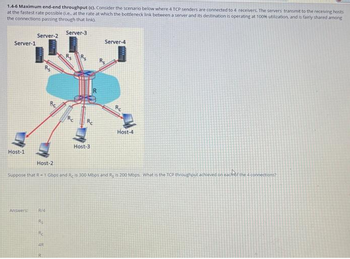
Transcribed Image Text:1.4-6 Maximum end-end throughput (c). Consider the scenario below where 4 TCP senders are connected to 4 receivers. The servers transmit to the receiving hosts
at the fastest rate possible (.e. at the rate at which the bottleneck link between a server and its destination is operating at 100% utilization, and is fairly shared among
the connections passing through that link
Server-3
Server-1
Host-1
Server-2
Answers:
R/4
Host-3
Rs
Re
4R
Server-4
Host-2
Suppose that R-1 Gbps and Reis 300 Mbps and R, is 200 Mbps. What is the TCP throughout achieved on each of the 4 connections?
Re
Host-4
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Network & Data Communcationsarrow_forwardA router interconnects a subnet, where all the interfaces of the subnets must have the prefix 164.132.62/24. suppose that the Subnet is required to support up to 60 interfaces, provide a network address that satisfies the above.arrow_forwardConsider an employee using their computer to send and retrieve email at their workplace. Only Ethernet networks are used for physical connectivity, but the mail server is located on a separate network. The employee’s network and the mail server’s network are connected by a single router which also has a connection to the Internet via the workplace’s ISP. Explain how the employees email client sends and receives emails using the email server, indicating any protocols involved and where any encapsulation/decapsulation occurs as data travels between the client, local mail server, and remote mail servers.arrow_forward
- NAT translation table LAN side addr WAN side addr 135.122.200.215 10.0.1.15 10,0.1.13 address 135.122.200.215 S: 10,0,1.27 2 D: 1 D: S: S: D: S: 10,0.1.15 D: 135.122,200,215 10.०.1.22arrow_forwardOnly typing answer Please explain step by step without table and graph thankyouarrow_forward2. The following illustration shows a transmission from Host A to Host B using Network Address Translation (NAT). Host A is located inside a Local Area Network (LAN) with an IP address of 192.168.1.2. The LAN is connected to the Wide Area Network (WAN), i.e. the Internet, through a router R1 that conducts NAT. R1 has two interfaces with an internal LAN IP address (192.168.1.1) and and external WAN IP address (127.45.10.35). Host B is located outside the LAN and is a well-known server, e.g., Google's server. Host B has an IP address of 130.160.23.45. Port numbers for the application components running at both hosts are provided in the figure. For a single message M1 being sent from Host A to Host B, please fill in the blanks in the illustration below with the source IP address and Port number at Host A and at the Router R1. Any information not provided may be assumed, however, please state your assumption clearly. Host A Local Area Network (LAN) IP: 192.168.1.2 Port: 5252 Source IP…arrow_forward
- A protocol for interleaved deliveries from two senders. Consider the figure below, which shows three nodes, A, B, and C. A and C are connected by a bi-directional channel; B and C are connected by a separate independent bi-directional channel. A and B can not communicate with each other. The goal of the protocol you will design is to transfer data from A and from B in a coordinated manner to C. The protocol between sender A and receiver C (and sender B and C) operates as follows. Senders A and B each receive data from their upper layer, via a call to rdt_send(data), which returns the data to be sent, exactly the same as the rdt protocols we studied in class and in the text. Senders A and B are to reliably send their sequence of data obtained via subsequent calls from rdt_send(data) to C. Node C should deliver to its application layer (via a call to deliver_data())a data item from A (as soon as it has correctly received that data item), followed by a data item from B (as soon as it has…arrow_forwardHelp please. I will like if it is correct . otherwise thumb's downarrow_forwardRefer to the network figure above, showing two Ethernet Subnets connected through an IP Router, answer the following question 1-5. The devices in each subnet are connected locally to each other through layer two intermediate devices such as Ethernet switch and ethernet hub. For each device in the subnets, both its Internet Protocol (IP )address and its MAC address (also called the Physical address or the Ethernet address are shown. The subnet mask used by all devices is 255.255.255.240 (which is the same as the prefix length “/28”). 1. If Client #1 wants to send a broadcast packet to all the devices on the left subnet (containing client #1, client #2, client #3) what destination IP address should be used? (Mention in both binary and decimal format.) 2. What is the first and last assignable IP address for the left subnet above (containing client #1 and #3)? (Mention in both binary and decimal format.)arrow_forward
- 39. The figure below shows the TCP Congestion Window for various transmission rounds of a TCP connection. 20 18 16 14 12 10 4 2 2 4 6 10 12 14 16 18 20 Transmission Round How many more (or less) segments will TCP Tahoe send compared to TCP Reno between the transmission rounds 12 and 16 inclusive (i.e., t12 to t16) for the same sequence of events as shown in the graph above (i.e., loss events at t11, tl4 and t16)? a. TCP Tahoe send 13 less segments compared to TCP Reno b. TCP Tahoe send 20 more segments compared to TCP Reno c. TCP Tahoe send 13 more segments compared to TCP Reno d. TCP Tahoe send 20 less segments compared to TCP Reno e. TCP Tahoe send 28 less segments compared to TCP Reno Congestion Window (MSS) 00arrow_forwardConsider a router that interconnects three subnets: Subnet 1, Subnet 2, and Subnet 3. Suppose all of the interfaces in each of these three subnets are required to have the prefix 223.10.128/24. Also suppose that Subnet 1 is required to support at least 50 interfaces, Subnet 2 is to support at least 100 interfaces, and Subnet 3 is to support at least 12 interfaces. Provide three network addresses (of the form a.b.c.d/x) that satisfy these constraints.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY