
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question

Transcribed Image Text:Your host in this example has IP address 172.16.1.1. Someone tries to send e-mail from a remote host with IP address 192.168.3.4. If successful, this will generate an SMTP
dialogue, consisting of SMTP commands and mail, between the remote user and the SMTP server on your host. Assume that a user on your host tries to send packets for this
scenario as shown:
Scenario Direction Src Addr Dest Addr Protocol Dest Port Action
1
2
In
Out
192.168.3.4 172.16.1.1
172.16.1.1 192.168.3.4
Indicate which packets are permitted or de
TCP
TCP
25
1234
?
?
and which rule is used in each case.
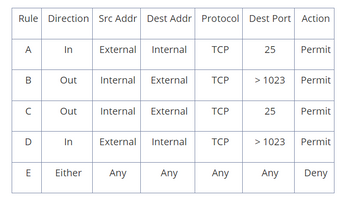
Transcribed Image Text:Rule Direction Src Addr Dest Addr Protocol Dest Port Action
A
B
с
D
E
In
Out
Out
In
Either
External
Internal
Internal
Internal
Any
External
External
External Internal
Any
TCP
TCP
TCP
TCP
Any
25
> 1023
25
> 1023
Any
Permit
Permit
Permit
Permit
Deny
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps with 1 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- The network address 172.30.0.0/16 is given. You need to design an IP plan for the network illustrated in Figure1 above using VLSM. Take note of the following: VLAN 10 (tut) has 200 users VLAN 20 (vut)has 100 users VLAN 30 (dut)has 250 users WAN1 has 2 users WAN2 has 2 users WAN3 has 2 usersarrow_forwardwhat valid host range is the ip address 192.168.112.173/28 a part of , Instead of using a standard dot-decimal format, the subnet mask, which is /28, of this IP is shown in CIDR representation (we'll talk about it later in class). The 28 after slash tells the first 28 bits of the given IP are network ID bits, which also implies the rest of 32-28 or 4 bits of the given IP are host ID bits. In other words, subnet mask /28 is equivalent to 255.255.255.240 in dot-decimal format. In the answer of this question, find the minimum IP of the host range, and find maximum IParrow_forwardYour host has IP address 172.16.1.1. Someone tries to send e-mail from a remote host with IP address 192.168.3.4. If successful, this will generate an SMTP dialogue, consisting of SMTP commands and mail, between the remote user and the SMTP server on your host. Assume that a user on your host tries to send packets for this scenario as shown: Scenario Direction Src Addr Dest Addr Protocol Dest Port Action 1 In 192.168.3.4 172.16.1.1 TCP 25 ? 2 Out 172.16.1.1 192.168.3.4 TCP 1234 ? Rule table: Rule Direction Src Addr Dest Addr Protocol Dest Port Action A In External Internal TCP 25 Permit B Out Internal External TCP > 1023 Permit C Out Internal External TCP 25 Permit D In External Internal TCP > 1023 Permit E Either Any Any Any Any Deny Indicate which packets are permitted or denied, and which rule is used in each case.arrow_forward
- Question # 3 Assume that Dominique and Pricilla agreed to use an auto key cipher with initial keyvalue k1 = 11. Now Dominique wants to send Pricilla the following message“THE CLASS IS CANCELLED”. Encrypt the message before transmitting it over the Internet Remember: i need a Mathematics solution not computer program You must show all the steps of your workarrow_forwardThere are events from different web server logs (see below). What can you tell about each row? What is happening in each row? What might be interesting in case of incident investigation? timestamp="09/Mar/2016:11:14:34 +0300" client_ip="73.9.84.166" user_agent="Debian APT-HTTP/1.3 (0.8.16~exp12ubuntu10.26)" url="/precise-security/stable/amd64/Packages.bz2"[09/Mar/2016:11:14:35 +0300] wiki-api.company-realm.ru 25.255.240.122 "GET /_api/frontend/.is_readonly?=&__uid=1120000000006167 HTTP/1.1" 200 "-" "-" "ivanovaa" "companyuid=5986251411438764783" - 717 0.022 0.022[09/Mar/2016:11:14:35 +0300] fml.company-realm.ru 202a:6b8:b010:2048:0:d0c0:5:12 "GET /rest/v2/call/collectPoolFromQueriesRatings/32b86116-e409-11e5-bdc7-0025909427cc?ticket=3201127 HTTP/1.1" 414 "-" "Apache CXF 3.0.4" "-"[09/Mar/2016:11:14:35 +0300] 127.0.0.1:443 127.0.0.1 "GET /ping HTTP/1.0" 200 "-" "KeepAliveClient" "-" "companyuid=-" - 273 0.146 0.146[09/Mar/2016:11:14:34 +0300] st.company-realm.ru 127.0.0.1 "GET…arrow_forwardPlease written by computer source Write a Snort rule to detect a connection attempt on the telnet server which has an IP address 192.168.32.129 and generate alerts for packets with content ‘Telnet!’ directed to the server.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education