
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
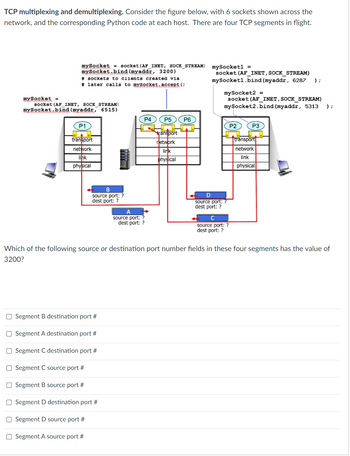
Transcribed Image Text:### TCP Multiplexing and Demultiplexing
#### Concept Overview
Consider the following figure, which demonstrates the concepts of TCP multiplexing and demultiplexing. The figure shows 6 sockets distributed across a network, each represented by layers (transport, network, link, and physical) and corresponding Python code for socket binding at each host. Four TCP segments are currently in flight between these sockets, identified as A, B, C, and D.
#### Diagram Explanation
The figure below illustrates:
1. **Host 1** with a Python code snippet:
```python
mySocket = socket(AF_INET, SOCK_STREAM)
mySocket.bind(myaddr, 3200)
# sockets to clients created via later calls to mySocket.accept()
```
- This host binds to address `myaddr` on port `3200`.
2. **Host 2** with Python code snippets:
```python
mySocket1 = socket(AF_INET, SOCK_STREAM)
mySocket1.bind(myaddr, 6287)
mySocket2 = socket(AF_INET, SOCK_STREAM)
mySocket2.bind(myaddr, 5313)
```
- This host binds to address `myaddr` on ports `6287` and `5313`.
3. **Host 3** with Python code:
```python
mySocket = socket(AF_INET, SOCK_STREAM)
mySocket.bind(myaddr, 6515)
```
- This host binds to address `myaddr` on port `6515`.
The network consists of multiple routers and a transport layer handling communication via these sockets. There are four TCP segments A, B, C, and D with unknown source and destination ports.
#### Network Layout
- **Hosts P1, P2, and P3** show transport layers communicating over physical, link, and network layers.
- **Routers P4, P5, and P6** facilitate communication by routing packets at the network layer.
#### TCP Segments in Flight
Segments A, B, C, and D are shown originating and terminating between different sockets, and their port numbers are to be inferred.
### Question
- **Question:** Which of the following source or destination port number fields in these four segments has the value of 3200?
**Answer Choices:**
1. Segment B destination port #
2. Segment A destination port #
3. Segment C destination port #
4. Segment
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 2 images

Knowledge Booster
Similar questions
- Match left-column statements to right-column architectures. Always-on server. Processes may provide or receive service. Any communication has a client and server. It's HTTP. User-controlled hosts may be up or down. Self-scalable. A. Peer-to-peer. B. Not client-server or peer-to-peer. C. Client-server/peer-to-peer. D. Client-server. E. TCP/IP.arrow_forwardWrite a Java program to create a TCP Socket program to receive an input message from client socket, reverse the input message and send it back to the client. Note that the program should have the comments embedded in it to explicitly explain why that code is being used. Explain in detail the client process and the server process with reference to the code given by you for this task.arrow_forwardWrite a Python program that assists you in managing a network of devices for your company. You need to keep track of the IP addresses, MAC addresses, and device types in your network. List: Create a list named device_ip containing IP addresses as strings. Your network consists of one router and at least one of each of the following devices: switch, server, workstation, printer, and mobile device. Each device should have a unique IP address. The router's IP address should be '192.168.1.1'. Print each IP address on a new line. Tuple: Since MAC addresses of devices are unique and not changing, you decide to store them in a tuple named device_mac. Create this tuple with MAC addresses corresponding to each IP address. A MAC address looks like '00:14:22:01:23:45'. Print each MAC address on a new line. Set: You also want to keep track of the different types of devices in your network. As the device types are distinct and do not have duplicates, create a set named device_type that contains…arrow_forward
- Port 80 is open on Host C, and a Web server is accessible via it. Suppose A and B are in charge of managing the website's server infrastructure. Is the same Host C socket used for all requests? All sockets with port 807 use the server's persistent connections and the requests are routed via two different sockets. Talk about and defend your position.arrow_forwardPlease just give a brief explanation about these cybersecurity questions.( Not more than three sentences).arrow_forwardExplain what this rule does: alert tcp any any -> 192.168.1.0/24 80 (content:”|A1 CC 35 87|”; msg:”accessing port 80 on local”).arrow_forward
- Three-way handshake is used by a TCP client and a TCP server to establish a connection, as illustrated below: 1st: client:port1 -> server:port2, SYN 2nd: server:port2 -> client:port1, SYNACK 3rd: client:port1 -> server:port2, ACK When this client is performing scanning attacks, it will generated a large number of failed connections. In each failed connection, the three-way handshake fails to complete. People commonly use SYN together with the absence of its corresponding SYNACK in this same TCP session to identify whether this connection is failed. By investigating the failed connections, an engineer finds that in legitimate/benign cases, if the server does not return SYNACK to the client, the client will not send the ACK packet after SYNACK (e.g., the 3rd packet above). Therefore, this engineer suggests that we can count the failed connections based on the following rules without considering SYNACK: If a client:port1 sends…arrow_forwardTrue or False 1. After fast retransmit is invoked, fast recovery cuts the slow start period in half 2. A host sends a segment with a sequence number 35 and a payload of 5 Bytes. The ACK number in that segment is 40 3. TCP segments can only be lost when router queues overflow. Please explain if possible, Thank you!arrow_forwardI made a TCP server using socket python,basically my server can: - Upload (“put”) request: The client should, at the very least, open (in binary mode) the local file defined on the command line, read its data, send it to the server through the socket, and finally close the connection. - Download (“get”) request: The client should, at the very least, create the local file defined on the command line (in exclusive binary mode), read the data sent by the server, store it in the file, and finally close the connection. To avoid accidents, the client should deny overwriting existing files. - Listing (“list”) request: the client should, at the very least, send an appropriate request message, receive the listing from the server, print it on the screen one file per line, and finally close the connection. I want you to draw an ER diagram that can show the process above please.arrow_forward
- Match left-column statements to right-column architectures. Always-on server. Processes may provide or receive service. Any communication has a client and server. It's HTTP. User-controlled hosts may be up or down. Self-scalable. A. Peer-to-peer. B. Not client-server or peer-to-peer. C. Client-server/peer-to-peer. D. Client-server. E. TCP/IP.arrow_forwardC Programming: Write a program that optionally accepts an address and a port from the command line. If there is no address and port on the command line, it should create a TCP socket and print the address (i.e. server mode). You can choose any port number for your server (>1024). If there is an address and port, it should connect to it (i.e., client mode). Once the connections are set up, each side should enter a loop of receive, print what it received, then send a message. The ping from the client should be sent before entering that loop to start the process. Otherwise both sides will sit and listen without getting anything. The message should be ping from the client and a pong from the server. In order to test this on one machine, you will need to run the same program twice (in two separate terminals). Run first in server mode, then run in client mode using the information printed from the server as your command line arguments. This is the output it must print out: Running…arrow_forwardimport socket def authenticate_user(tcp_socket): while True: response = tcp_socket.recv(1024).decode() print(response) username = input() tcp_socket.sendall(username.encode()) response = tcp_socket.recv(1024).decode() print(response) password = input() tcp_socket.sendall(password.encode()) auth_response = tcp_socket.recv(1024).decode() if "successful" in auth_response: print(auth_response) return True else: print(auth_response) def receive_items(tcp_socket): while True: response = tcp_socket.recv(1024).decode() if "Item List:" in response: print(response) while True: item = tcp_socket.recv(1024).decode() if not item.strip(): break print(item) break def select_items(tcp_socket): selected_items = [] while True: item_id = input("Select item by entering…arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY