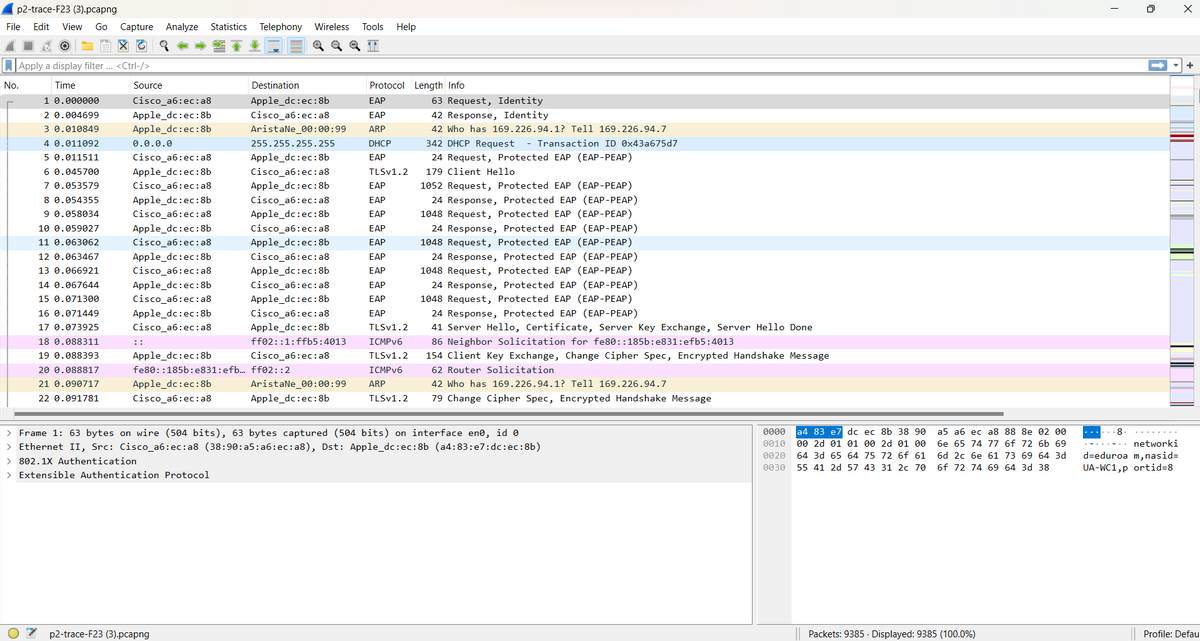
The goal of this assignment is to explore the network packets associated with several typical online activities. You will have the chance to analyze bit-by-bit the flows associated with these services and evaluate different application and protocol parameters across the entire TCP/IP stack including Data Link Layer/Medium Access Control (L2), Network Layer (a.k.a. IP or L3), Transport Layer and Application Layer. To carry out this analysis, you will use Wireshark. Part of finishing this assignment will be learning how to use Wireshark effectively. While Wireshark allows you to capture packets on a network interface it can also be used to read previously collected packet traces. Make sure to show the full steps and screenshots of capturing network packets on Wireshark. Attached is the image of the Wireshark trace that needs to be analyzed.
WireShark:
The goal of this assignment is to explore the network packets associated with several typical online activities. You will have the chance to analyze bit-by-bit the flows associated with these services and evaluate different application and protocol parameters across the entire TCP/IP stack including Data Link Layer/Medium Access Control (L2), Network Layer (a.k.a. IP or L3), Transport Layer and Application Layer. To carry out this analysis, you will use Wireshark. Part of finishing this assignment will be learning how to use Wireshark effectively. While Wireshark allows you to capture packets on a network interface it can also be used to read previously collected packet traces. Make sure to show the full steps and screenshots of capturing network packets on Wireshark.
Attached is the image of the Wireshark trace that needs to be analyzed.
Trending now
This is a popular solution!
Step by step
Solved in 3 steps

Where are the screenshots of how to capture and analyze packets on WireShark? Make sure to show screenshots of each step on WireShark.








