
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
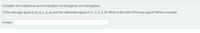
Transcribed Image Text:Consider the mathematical formalization of encryption and decryption.
If the message space is {a, b, c, d, e} and the ciphertext space is {1, 2, 3, 4, 5}. What is the size of the key space? Write a number.
Answer:
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Write a Python program that declares a string and returns key-value pairs of the letters in alphabetical order which occur in the string together with the number of times each letter occurs. Case should be ignored.arrow_forwardMany user-created passwords are simple and easy to guess. Write a program that takes a simple password and makes it stronger by replacing characters using the key below, and by appending "q*s" to the end of the input string. i becomes ! a becomes @ m becomes M B becomes 8 o becomes . Ex: If the input is: mypassword the output is: Myp@ssw.rdq*s Hint: Python strings are immutable, but support string concatenation. Store and build the stronger password in the given password variable.arrow_forwardC++ Nothing too advanced please. Learning the basicsarrow_forward
- hello im stuck on a problem and it would be great if you could create a program that prompts the user for a message to encode,as well as an offset to encrypt it with. You will then create and use the following methods:• A validation method that takes in the message (as a string) and the offset integerentered by the user. The method should return “true” if the offset is between 0and 26 inclusively and the message contains only letters and spaces. If it failseither criteria, it should return “false”.• If the validation method returns true, a second encryption method should becalled. This method also takes in the message (as a string) and the offset integerentered by the user. It should convert the message to UPPERCASE, encryptevery letter in the message, and leave the spaces as they were. It should thenreturn the encrypted message. i attached an image of the sample outputarrow_forwardSamething this is not a graded question it's all in python.arrow_forwardPasswords that are created by users are usually very simple and easy to guess. Create a Python program that takes a simpler pswrd + makes it stronger by taking characters using the rules below, and by appending "!" to the ending of the input string. i becomes 1 a becomes @ m becomes M B becomes 8 s becomes $ Example: If the input is: mypassword the output is: Myp@$$word! Hint: Python strings are immutable, but support string concatenation. Store and build the stronger password in the given password variable This is what I have so far.... word = input()password = ''arrow_forward
- On a piano, a key has a frequency, say f0. Each higher key (black or white) has a frequency of fo* r, where n is the distance (number of keys) from that key, and r is 21/12) Given an initial key frequency, output that frequency and the next 3 higher key frequencies. Output each floating-point value with two digits after the decimal point, then the units ("Hz"), then a newline, using the following statement: printf("$0.21f Hz\n", yourValue); Ex: If the input is: 440.0 (which is the A key near the middle of a piano keyboard), the output is: 440.00 Hz 466.16 Hz 493.88 Hz 523.25 Hz Note: To compute the next 3 higher key frequencies, use one statement to computer = 2(1/12) using the pow function (remember to include the math library). Then use that r in subsequent statements that use the formula f = f0 *r¹ with n being 1, 2, and finally 3. O Run v main.c 1 2 3 int main(void) { #include Reset Lab Tutorial Ⓡarrow_forwardWrite a program that reads a string (password) and a number. The maximum number of attempts (3). The program with stop asking data if the word ‘quit’ is provided in the password value. If user provide correct credential the message access granted will be displayed otherwise the message access denied with be generated.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY