
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Explain your answer in detail. Thank you!!!
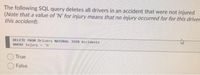
Transcribed Image Text:The following SQL query deletes all drivers in an accident that were not injured
(Note that a value of 'N' for injury means that no injury occurred for for this driver
this accident):
DELETE FROM Drivers NATURAL JOIN Accidents
WHERE injury- 'N'
True
False
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- The Internet has evolved into a crucial medium for exercising one's right to freedom of expression. Facebook and Twitter are both being used by a large number of individuals and organizations to disseminate hate speech. Should there be no limits placed on what people may say online? Where should the line be drawn when it comes to limiting hate speech on social media?arrow_forwardPrivacy is a hot-button topic in today's culture, but it's also a contentious one. What do you believe can be done to protect the privacy of Internet users? Specifically, do you think laws are adequate?arrow_forwardThe Internet has become an increasingly important medium via which individuals may exercise their right to free speech. Facebook and Twitter are being used by a lot of different people and organisations to spread anti-Semitic information. Is free expression on the internet a right or a privilege? How far should social media companies go to stop the spread of information that promotes hatred?arrow_forward
- Hence, the Internet has become an essential tool for exercising one's right to free expression. Several individuals and groups are guilty of misusing social media sites like Facebook and Twitter to propagate hate speech. Should there be any limits placed on how individuals may share their ideas online? Where should the line be set when it comes to allowing nasty remarks on social networking sites?arrow_forwardIt would be incredible if there was a piece of software that would allow a surgeon in one region of the world to do surgery on a patient located in another region of the world through the internet. Once the curtain has fallen on the last act, there is no need for anybody else to be there. How much death and devastation do they want to witness? In the event that they wanted to undermine your credibility, what do you believe the primary point of emphasis would be? Does it first need the existence of an active aggressor for there to be a possibility of damage being caused?arrow_forwardThese days, you can't have free speech without the Internet. It's no secret that many people and organizations use social media to spread hateful messages. Should there be restrictions on what may be said online? Is there a way to stop hate speech on social media?arrow_forward
- Do you feel the internet and other forms of social media have been a positive force in the development of society as a whole? What leads you to believe that response is the greatest one we could possibly get?arrow_forwardHello. Thanks for the answer. Does this answer cover 5 entitities or is it 3? Thanks.arrow_forwardAs a result, using the Internet has become a crucial tool for exercising one's right to free expression. Hate speech is widely disseminated via social media platforms such as Facebook and Twitter, which are widely abused by a large number of individuals and even organizations. Should people's ability to express themselves freely on the internet be unrestricted? Where should the line be set when it comes to allowing nasty remarks on social networking sites?arrow_forward
- Laws tell you how to keep private information safe, while ethics tell you how to do it in a way that is morally right. What do you think of privacy?arrow_forwardEven though privacy is highly valued in today's culture, there are conflicting opinions on it. Do you believe that there is still more that can be done to protect online privacy? Do you, for instance, think that laws are adequate?arrow_forwardAre people's lives enhanced or diminished by online gaming? Why do you believe this?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY