
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
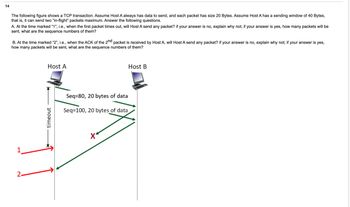
Transcribed Image Text:The following figure shows a TCP transaction. Assume Host A always has data to send, and each packet has size 20 Bytes. Assume Host A has a sending window of 40 Bytes, that is, it can send two “in-flight” packets maximum. Answer the following questions.
A. At the time marked “1”, i.e., when the first packet times out, will Host A send any packet? If your answer is no, explain why not; if your answer is yes, how many packets will be sent, what are the sequence numbers of them?
B. At the time marked “2”, i.e., when the ACK of the 2ⁿᵈ packet is received by Host A, will Host A send any packet? If your answer is no, explain why not; if your answer is yes, how many packets will be sent, what are the sequence numbers of them?
### Diagram Description
The diagram illustrates a TCP transaction between two hosts: Host A and Host B.
- Host A sends two packets to Host B:
- The first packet has the sequence number 80 and contains 20 bytes of data.
- The second packet has the sequence number 100 and also contains 20 bytes of data.
- A timeout occurs, marked as "1" in red, which means that the first packet did not receive an acknowledgment (ACK) within the expected time.
- The second packet is successfully received by Host B, and an ACK is sent back to Host A, marked as "2" in red.
- The diagram includes a red "X" indicating a lost packet or communication failure for the packet with sequence number 80.
Overall, the diagram is used to explain when Host A will decide to resend packets or send new packets based on the ACKs and timeouts it experiences during the TCP transaction.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- 6. Consider a network with some hosts. The traffic from one host to the other is provided. The question is to find the total bytes that are moving in the network from one host to the other and also for all the routes. The total bytes that are transferred for the day is as below. peter ann 1250 peter mary 910 mark mary, 1250 peter mary 450 peter andy 2924 paul peter 1218 paul helen 199 The first name is the source host, the second is the destination host and the number is the bytes that are transferred.arrow_forwardSuppose you want to deliver the gift to your friend, Jashim as a birthday gift. You packed the gift in five different packets, give them serial no and send them to your friend’s address at a time. Jashim has a PA to collect all packets and store them by their serial. If Jashim’s PA can receive all the packets serially then deliver them to Jashim. If any packet is missing, Then the PA inform you to resend the packet again.I. Which protocol you want to use to avoid over cost if resend is required.II. Describe your used protocol with an appropriate diagram using the above description.arrow_forwardNetwork & Data Communcationsarrow_forward
- A router interconnects a subnet, where all the interfaces of the subnets must have the prefix 164.132.62/24. suppose that the Subnet is required to support up to 60 interfaces, provide a network address that satisfies the above.arrow_forwardThanksarrow_forwardIn modern packet-switched networks, including the Internet, the source host segments long, application-layer messages (for example, an image or a music file) into smaller packets and sends the packets into the network. The receiver then reassembles the packets back into the original message. We refer to this process as message segmentation. Figure 1.27 illustrates the end-to-end transport of a message with and without message segmentation. Consider a message that is 8. 106 bits long that is to be sent from source to destination in Figure 1.27. Suppose each link in the figure is 2 Mbps. Ignore propagation, queuing, and processing delays. a. Consider sending the message from source to destination without message segmentation. How long does it take to move the message from the source host to the first packet switch? Keeping in mind that each switch uses store-and-forward packet switching, what is the total time to move the message from source host to destination host? b. Now suppose that…arrow_forward
- Consider one TCP connection on a path with a bottleneck link with capacity L. We have a file of size F(assume F is a very large file size). If TCP segment size is B bytes, the two-way propagation delay is tp and connection is always in congestion avoidance phase, find the following: A. Maximum window size that TCP can achieve B. Average window size and average throughput in this TCP connection C. Time it will take from connection establishment to reaching the maximum window size.arrow_forward1. Consider the following protocol for adding money to a debit card. (i) User inserts debit card into debit card machine. (ii) Debit card machine determines current value of card (in dollars), which is stored in variable x. (iii) User inserts dollars into debit card machine and the value of the inserted dollars is stored in variable y. (iv) User presses enter button on debit card machine. (v) Debit card machine writes value of x + y dollars to debit card and ejects card. Recall the discussion of race conditions. This particular protocol has a race condition. a. What is the race condition in this protocol? b. Describe a possible attack that exploits the race condition. c. How could you change the protocol to eliminate the race condition, or at least make it more difficult to exploit?arrow_forwardA connection that connects two hosts may transport many packets at the same time. Please provide a schedule that outlines all of the actions that need to be completed in order to successfully execute one shipment. Is it to be anticipated that one of the delays will take a certain amount of time, while the duration of the other delay may be adjusted in accordance with the circumstances?arrow_forward
- Consider a simple protocol for transferring files over a link. After some initial negotiation, A sends data packets of size 1 KB to B; B then replies with an acknowledgment. A always waits for each ACK before sending the next data packet; this is known as stop-and-wait. Packets that are overdue are presumed lost and are retransmitted. (a) In the absence of any packet losses or duplications, explain why it is not necessary to include any "sequence number" data in the packet headers. (b) Suppose that the link can lose occasional packets, but that packets that do arrive always arrive in the order sent. Is a 2-bit sequence number (that is, N mod 4) enough for A and B to detect and resend any lost packets? Is a 1-bit sequence number enough? (c) Now suppose that the link can deliver out of order and that sometimes a packet can be delivered as much as 1 minute after subsequent packets. How does this change the sequence number requirements?arrow_forwardA connection that connects two hosts may transport many packets at the same time. Please provide a schedule that outlines all of the actions that need to be completed in order to successfully execute one shipment. Is it to be anticipated that one of the delays will take a certain amount of time, while the duration of the other delay may be adjusted in accordance with the circumstances?arrow_forwardSuppose two TCP connections share a path through a router R. The router's queue size is six segments; each connection has a stable congestion window of three segments. No congestion control is used by these connections. A third TCP connection now is attempted, also through R. The third connection does not use congestion control either. Describe a scenario in which, for at least a while, the third connection gets none of the available bandwidth, and the first two connections proceed with 50% each. Does it matter if the third connection uses slow start? How does full congestion avoidance on the part of the first two connections help solve this?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education