
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
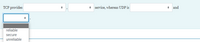
Transcribed Image Text:TCP provides
service, whereas UDP is
and
reliable
secure
unreliable
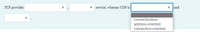
Transcribed Image Text:TCP provides
service, whereas UDP is
* Jand
connectionless
address-oriented
connection-oriented
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- TCP provides service, whereas UDP is and secure reliable unreliablearrow_forwardASAParrow_forwardTCP expects complete transparency from all parties, which includes almost all endpoint operating systems. Is TCP vulnerable to cheating, and if so, how may one endpoint benefit in relation to others?arrow_forward
- UDP implementation of dependability and other TCP features is required in order for the QUIC protocol to provide HTTP True False 00.arrow_forwardTCP is a connection-oriented protocol, but IP does not need a connection to function properly. How can these two protocols best coexist in the same protocol stack? What is the most effective way to do this?arrow_forwardTCP is a reliable and full duplex transport layer protocol when it comes to providing services. Full-duplex, connection-oriented, and reliable delivery all imply the same thing?arrow_forward
- TCP demands complete openness from all parties involved, which includes almost every endpoint operating system. Is it feasible to manipulate the Transmission Control Protocol (TCP), and if so, how may one instance gain an edge over other endpoints?arrow_forwardDNS employs UDP over TCP. No automatic recovery if a DNS packet is missed. Is this a problem, and if so, how?arrow_forwardThe UDP protocol is a messaging protocol. Token-based protocols like TCP are known as byte-oriented protocols. Which protocol, UDP or TCP, should an application employ to safeguard the message's boundaries?arrow_forward
- Reliability and other TCP features must be ported to UDP in order for the QUIC protocol to provide HTTP True False 00.arrow_forwardTCP demands all parties, including endpoint operating systems, to be transparent. How can one endpoint trick the Transmission Control Protocol (TCP)?arrow_forwardWhat is the purpose of UDP? If user programs were allowed to send only raw IP packets, would it not have sufficed to leave it at that?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY