Related questions
Question
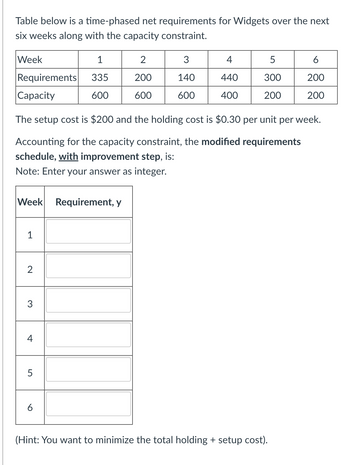
Transcribed Image Text:Table below is a time-phased net requirements for Widgets over the next
six weeks along with the capacity constraint.
Week
1
2
3
4
5
6
Requirements
335
200
140
440
300
200
Capacity
600
600
600
400
200
200
The setup cost is $200 and the holding cost is $0.30 per unit per week.
Accounting for the capacity constraint, the modified requirements
schedule, with improvement step, is:
Note: Enter your answer as integer.
Week Requirement, y
1
2
3
4
5
6
(Hint: You want to minimize the total holding + setup cost).
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps
