Question
Alert dont submit AI generated answer.
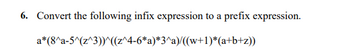
Transcribed Image Text:6. Convert the following infix expression to a prefix expression.
a*(8^a-5^(z^3))^((z^4-6*a)*3^a)/((w+1)*(a+b+z))
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- 1. How do you present feature creep? (Maximum 2 pages)arrow_forwardPlease refer to the attachment for the sceniro. Please answer the following question - paragraph on A clear description of the identity threats pertinent when using a SaaS solution.arrow_forwardAlert dont submit AI generated answer.arrow_forward
arrow_back_ios
arrow_forward_ios