
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
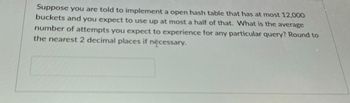
Transcribed Image Text:Suppose you are told to implement a open hash table that has at most 12,000
buckets and you expect to use up at most a half of that. What is the average
number of attempts you expect to experience for any particular query? Round to
the nearest 2 decimal places if necessary.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Suppose you want to store 2000 things with an Open Hash Table. How must you size your hash table to maintain 1.25 average number of tries?arrow_forwardWhen creating an open hash table with decent functionality, keep the following points in mind:arrow_forwardJava - Hash table valsTable is shown below. The hash function is key % 5.arrow_forward
- A hash table with non-negative integer keys has a modulo hash function of key % 15. Hash function index range: 0 to Ex: 5 Item 110 will go in bucket Ex: 26arrow_forwardSuppose the length of a hash table is 14, and the hash function is h(key)=key%11. There are only four nodes in the table: H(15)=4, H(38)=5, H(61)=6, H(84)=7, and the remaining positions are empty. If the conflict is handled by the linear detection method, what is the node address of 49? 8. 3 9. None of the abovearrow_forwardShow what the array of the HashMap would look like after all the items below have been added, assuming the HashMap class uses linear probing to resolve collisions. Assume the array is resized when the current item to be added will make the total number of items greater than or equal to the threshold value. Note that for both questions, you do not need to compute the hashcodes, since I have provided them for you. Therefore, you only need to carry out Step 2, which is translating the hashcodes to valid array indexes. Assume remainder division is used to accomplish this. The challenge of this assignment is to correctly handle all collisions that may result when translating the larger range of hascode values into the smaller range of valid array indexes. For this assignment you will not need to resize the array or re-hash items.arrow_forward
- Is it possible to "decrypt" a hash of a message in order to obtain the original message? Give an explanation for your answer.arrow_forwardRehash the hash table below (separate chaining, length 5) to a new length of 10. Draw the new hash table after rehashing, Assume that hashCode (x) = x for this question. Assume that we always traverse a chain from head to tail and always insert at the head of the chain example 0:15->30 1:6->21->11 2: 3: A 4:-14arrow_forwardyou can search a hashtable either by the keys , or by the assiocated values. True or false ?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education