
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
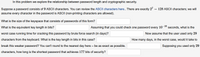
Transcribed Image Text:In this problem we explore the relationship between password length and cryptographic security.
Suppose a password consists of 9 ASCII characters. You can review the ASCII characters here.. There are exactly
27
= 128 ASCII characters; we will
assume every character in the password is ASCII (non-printing characters are allowed).
What is the size of the keyspace that consists of passwords of this form?
What is the equivalent key length in bits?
Assuming that you could check one password every 10-10 seconds, what is the
worst case running time for cracking this password by brute force search (in days)?
Now assume that the user used only 29
characters from the keyboard. What is the key length in bits in this case?
How many days, in the worst case, would it take to
break this weaker password? You can't round to the nearest day here -- be as exact as possible.
Supposing you used only 29
characters, how long is the shortest password that achieves 177 bits of security?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 4 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Solving this problem in the Java languagearrow_forwardA grid needs a system for numbering the tiles in order to allow random-access lookup.For instance, the rows and columns of a square grid provide a natural numbering for the tiles. Create plans for hexagonal and triangular grids. Create a rule for identifying the neighbourhood (i.e., nearby tiles) of a certain tile in the grid using the numbering scheme. For instance, the neighbourhood of tile I j in a four-connected square grid with indices of I for rows and j for columns may be described as neighbourhood(i, j) = I 1, j, I j 1.arrow_forward3. Implement in python. Consider the sample size of N=25 drawn from a normal distribution with mean 50, and standard deviation of 2. Repeat the process 200 tines. Draw the sampling distribution of sample mean. what is the mean of the sampling distribution of the sample mean and standard distribution of the sample mean? How do that compare with population mean and standard deviation.arrow_forward
- Plot (as a function of angular frequency), the magnitude and the phase of the impedance resulting from a resistor (1.2 kOhm) and inductor (1.5 mH) in parallel. Use a logarithmic axis for the frequency, and for the magnitude. Use the range [10, 10**10] rad/s. The impedance of an inductance L is ???Ljω. Label axes. In python and can use cmath if neededarrow_forwardImagine you have a spreadsheet with exactly one row of data—row 2—that has three cells with data in it. You want to copy that row to row 1. Describe how you would cut and paste row 2 to row 1 using only key commands (no mouse clicks or menu selections). For the arrows, up, down, left, and right are sufficient; for hotkey commands that require two keys pressed at once, use a + symbol between the keys (e.g., Shift + Z for undo). You start in cell A1.arrow_forwardWrite a program to handle a user's rolodex entries. (A rolodex is a system with tagged cards each representing a contact. It would contain a name, address, and phone number. In this day and age, it would probably have an email address as well.) Typical operations people want to do to a rolodex entry are: 1) Add entry 2) Edit entry 3) Delete entry 4) Find entry 5) Print all entries 6) Quit You can decide what the maximum number of rolodex entries is and how long each part of an entry is (name, address, etc.). When they choose to edit an entry, give them the option of selecting from the current rolodex entries or returning to the main menu — don't force them to edit someone just because they chose that option. Similarly for deleting an entry. Also don't forget that when deleting an entry, you must move all following entries down to fill in the gap. If they want to add an entry and the rolodex is full, offer them the choice to return to the main menu or select a person to overwrite. When…arrow_forward
- An early attempt to force users to use less predictable passwords involved computer supplied passwords. The passwords were eight characters long and were taken from the character set consisting of lowercase letters and digits. They were generated by a pseudo-random number generator with 2^15 possible starting values. Using the technology of the time, the time required to search through all character strings of length 8 from a 36-character alphabet was 112 years. Unfortunately, this is not a true reflection of the actual security of the system. Explain the problemarrow_forwardUSING KEIL PLEASE.. Ciphers use many bitwise operations for cryptography. Write an ARM assembly program to use ciphers. See the steps below to implement the cipher. In this program, you will implement a "Symmetric Encryption". Create three variables, Plaintext, Key, and Cipher (5 Points) For encryption, design a key value, assign the last nonzero number of your student ID (#900 number) in a variable called “Key” (5 Points) For example: if your 900 number is 90012450. Assign 5 to the variable Key and use it as the Key for encryption. Use this link for the Links to an external site.video to understand Symmetric Key Cryptography and implement that for encryption and decryption. For the variable Plaintext, assign any four-letter word. Encrypt the plaintext using the value in Key and store the encrypted text in the variable Cipher. Test the encryption by decrypting and storing the decrypted text into register R5. Provide comments to each statementarrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education