
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
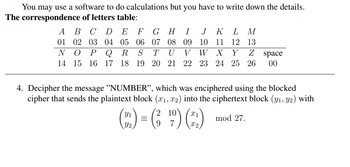
Transcribed Image Text:You may use a software to do calculations but you have to write down the details.
The correspondence of letters table:
A
01
B C D E F GH I J K L M
02 03 04 05 06 07 08 09 10 11 12 13
TU V W X Y
N O P Q R
14 15 16 17 18
Z space
S
19 20 21 22 23 24 25 26 00
4. Decipher the message "NUMBER", which was enciphered using the blocked
cipher that sends the plaintext block (x₁, x2) into the ciphertext block (y₁, y2) with
2
(22) = (₂¹9) (2)
mod 27.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Write a Python Program to take days from the user and covert it • week & day. into years,arrow_forwardSolving this problem in the Java languagearrow_forwardImplementing a very basic encryption scheme known as a caesar cipher. The caesar cipher involves shifting every letter in the given string by a given number in the alphabet. Please help me write a NASM assembly language program that: Asks the user for a number between -25 - 25 (-25 <= num <= 25) You have to do error correctionarrow_forward
- Write a python script that reads the file studentNames.txt which contains the names of students. Print out "Writing the names of the students." Then print the names in the file. For testing write any 5 names in your file and attach your code, file, and output in the document.arrow_forwardQ2 Consider x and y to represent data points (xi,yi), where i = 1, 2, 3, … n. What is the length of pafter running the following command? p = polyval(x,y) Select one: a. n b. n - 1 c. n + 1 d. Empty variable e. 1 Q1 The periodic function sin(2x) has multiple roots between x values of -5π and 5π. If xL = -15 and xU = 15, which of the following statements is true using a bracketed method? Select one: a. All roots will be returned b. The middle root will be returned c. The chosen bracket is invalid for bracketed methods d. A single root will be returned e. The algorithm will be stuck in an infinite looparrow_forwardwrite R script (commands) where it takes three numbers from the user and prints the greatest numberarrow_forward
- Create a python program that will decrypt messages encrypted using the Caesar Cipher program. The decryption program must be able to decrypt encrypted messages written in uppercase letters. ******Comment every code*****For beginners ***arrow_forwardWrite a program that checks for the correct pin of the account. • You set the pin (e.g. 12345). • When a user types in the correct pin, then display "Correct, welcome back." • When a user types in incorrect pin, then display "Incorrect, try again." • When a user ran out of tries, then display "Sorry, you have been locked out." Each user has the maximum of 3 tries. Example 1: Enter code:12 Incorrect, try again. Enter code:12345 Correct, welcome back. Example 2: Enter code:07812 Incorrect, try again. Enter code:31345 Incorrect, try again. Enter code:19867 Sorry, you have been locked out. Think about your logic. Drawa flowchart and/or write a pseudocode and test with sample data. After testing, write your code in Python. Please attach your Jupyter notebook solution and submit.arrow_forwardIn this problem, you will implement a transposition cipher that, instead of dividing the original text into odd and even characters, separates it into three sets of characters. As an example, we will use this 1977 quote by Digital Equipment Corp. president Ken Olson -- "There is no reason anyone would want a computer in their home." (Spaces are represented with the square u-like character.) There is no reason anyone would want a computer in their home. Rail 1: T r S d i t i h a C. e Rail 2: e a u a u in h Rail 3: a W n. m m Example three-rail transposition. The resulting encrypted text is produced by reading the text horizontally, i.e., adding the three rails: Rail 1 + Rail 2 + Rail 3 = **“Trinrs yeoda cpeitihehesoeoao u naournhro.e annnwlwt mt e m" (without the quotes). Requirements: Implement the three-rail transposition cipher above, placing your code in the file p4_2.py (template I provided, replace comment at the beginning of the file with your own code). Feel free to develop your…arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education