
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
The language is in Racket. Please answer the question in the screenshot.
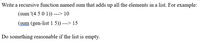
Transcribed Image Text:Write a recursive function named sum that adds up all the elements in a list. For example:
(sum '(4 5 0 1)) ---> 10
(sum (gen-list1 5)) ---> 15
Do something reasonable if the list is empty.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps with 2 images

Knowledge Booster
Similar questions
- How relevant are rules about who can and cannot enter a certain area, anyway, in the modern world? In your response, please give at least two instances where access was restricted.A28arrow_forwardMake the distinction between spamming and flaming.Make the distinction between spamming and flaming.arrow_forwardI can't seem to get my hands on the book's access code. Please walk me through the steps of finding it on my Yuzu account.arrow_forward
- Snort rules are broken into two logical sections or two groups of fields (answer should be in lower case). What are the names given to each one of these groups of snort fileds Answer. First group of fields: Answer. First group of fields:arrow_forwardHow relevant are rules about who can and cannot enter a certain area, anyway, in the modern world? In your response, please give at least two instances where access was restricted.arrow_forwardWhich of the following information can be classified as a sensitive personal information? * Your name. Your being a fan of BTS. Your Age. Your weight.arrow_forward
- How do I check the script is functional?arrow_forwardWhich of the following is the difference between impersonation and elicitation? Question options: a. Elicitation is the process of acting like an IT employee to gain access to a server room. b. Impersonation is the process of gathering information from employees. c. Elicitation is the process of collecting or acquiring data from human beings. d. Impersonation is the sending of surveys to collect data from a group of employees.arrow_forwardcreate a search statement on: The effect of the COVID-19 pandemic on higher education. Using Boolean operatorsarrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY