
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
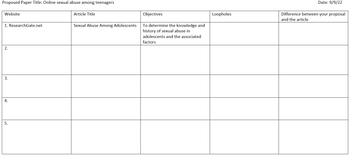
Transcribed Image Text:Proposed Paper Title: Online sexual abuse among teenagers
Website
1. ResearchGate.net
2.
3.
4.
5.
Article Title
Sexual Abuse Among Adolescents
Objectives
To determine the knowledge and
history of sexual abuse in
adolescents and the associated
factors
Loopholes
Date: 9/9/22
Difference between your proposal
and the article
Expert Solution
arrow_forward
Step 1
The question has been answered in step2
Step by stepSolved in 2 steps with 1 images

Knowledge Booster
Similar questions
- explain the 4 malwares found from your search. Use the table given below:arrow_forwardComputer forgery: forms and results Where do we go from here to put a stop to cybercrime?arrow_forwardChapter 13 – Mobile Devices in Computer Forensics Review Questions (4 points) What are the different roles of mobile devices in crime? Answer: What problems do prepaid phones pose to investigators? Answer: What is mobile phone cloning? Answer: Which kinds of evidence can be retrieved from mobile phones and PDAs? Answer: Practical Exercise (3 points) Mobile devices have been the objectives of crimes (target). They have been utilized to commit crimes (tool). Sometimes the devices simply hold evidence of crimes (incidental). Conduct an online search for a case not described in this chapter where a mobile device was involved in a criminal or civil investigation. Name and reference/link the case that you discovered. Answer: What were some of the case’s critical facts? Answer: What was the specific role(s) of the mobile device in the investigation? Answer: (Continued on next page) Critical Thinking Questions (3 points) New mobile devices are…arrow_forward
- Q2- A security threat exists when an unauthorised user is fraudulently accessed the sensitive record and modified it. Briefly describe possible ways that can mitigate this attack and how. (If you can please identify 5 possible way or as much as you canarrow_forwardDescribe why corporate internal conversations are not covered by the Electronic Conversations Privacy Act of 1986.arrow_forwardCase Analysis on Facebook 2019 data breach.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY