
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
1. Please describe the advantage/disadvantage on each step (Step 1 to 8) and explain which steps achieve
creator’s properties.
2. From a ransomware creator’s point of view, how can the entire process be more efficient and secure ?
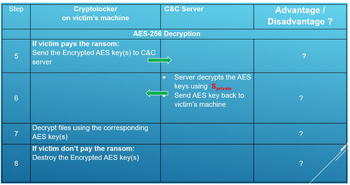
Transcribed Image Text:Step
LO
5
6
7
8
Cryptolocker
on victim's machine
AES-256 Decryption
If victim pays the ransom:
Send the Encrypted AES key(s) to C&C
server
Decrypt files using the corresponding
AES key(s)
C&C Server
If victim don't pay the ransom:
Destroy the Encrypted AES key(s)
Server decrypts the AES
keys using Sprivate
Send AES key back to
victim's machine
Advantage /
Disadvantage ?
?
?
?
?
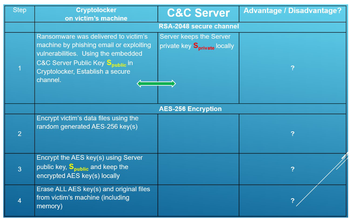
Transcribed Image Text:Step
1
2
3
4
Cryptolocker
on victim's machine
Ransomware was delivered to victim's
machine by phishing email or exploiting
vulnerabilities. Using the embedded
C&C Server Public Key Spublic in
Cryptolocker, Establish a secure
channel.
Encrypt victim's data files using the
random generated AES-256 key(s)
Encrypt the AES key(s) using Server
public key, Spublic and keep the
encrypted AES key(s) locally
Erase ALL AES key(s) and original files
from victim's machine (including
memory)
C&C Server
RSA-2048 secure channel
Server keeps the Server
private key Sprivate locally
AES-256 Encryption
Advantage / Disadvantage?
?
?
?
?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 2 images

Knowledge Booster
Similar questions
- How integral is software security to the whole software development lifecycle and stack?arrow_forwardWhy is it important to develop a culture of security to support theinclusion of security in the software development lifecycle? Giveexamples to justify your position.arrow_forwardA security policy is a document that provides employees with clear instructions about acceptable use of company confidential information, explains how the company secures data resources and what it expects of the people who work with this information. Most importantly, the policy is designed with enough flexibility to be amended when necessary. You are working in organization X, and you are supposed to develop an issue-specific security policy, you can pick one issue from Table.1 [1] (In the photos) Your Task is: To develop the different sections of your policy and adequate procedure(s), you can refer to SANS Policy Templates [2]. References: [1] Developing an Information Security Policy: A Case Study Approach, Fayez Hussain Alqahtani. 4th Information Systems International Conference 2017, ISICO 2017, 6-8 November 2017, Bali, Indonesia. [2] https://www.sans.org/information-security-policy/arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY