
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
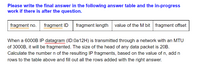
Transcribed Image Text:**Exercise: IP Fragmentation Calculation**
Please write the final answer in the following answer table and the in-progress work if there is after the question.
| **fragment no.** | **fragment ID** | **fragment length** | **value of the M bit** | **fragment offset** |
|------------------|-----------------|---------------------|------------------------|---------------------|
---
When a 6000B IP datagram (ID: 0a12H) is transmitted through a network with an MTU of 3000B, it will be fragmented. The size of the head of any data packet is 20B. Calculate the number \( n \) of the resulting IP fragments, based on the value of \( n \), add \( n \) rows to the table above and fill out all the rows added with the right answer.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 1 images

Knowledge Booster
Similar questions
- We can send output of a command to append a text file (keeping the old data in the file) with the command: > filename.txt Group of answer choices True Falsearrow_forwardUDP and TCP use 1s complement for their checksums. Suppose the receive received two 3-bits payload messages: 010, 001. The checksum received is 100. Find all possible original messages. How many errors were made during the transmission?arrow_forwardGiven what we know about transmission delay and the following: A web client and a web server separated by one intermediary router. • Each link carries data at 1Mbps with an MTU of 8192 bytes • Each link is 1000 km long with a propagation speed of 250000 km/s • Zero processing and queueing delays • Connection management packets (packets used for opening a connection, confirming a connection and acknowledging receipt of information) contain no data and all packets have 125 bytes of overhead on top of any data they may contain. • The web client makes an HTTP request to the server that is 250 bytes long. • The requested data is 4 kilobytes in size with 500 bytes of overhead for the HTTP status and headers What is the RTT to open the connection? а. b. How long would it take for a web client to complete the request? You can ignore any time needed to close the connection.arrow_forward
- Show your work for the following conversion. a) Convert the following block of IP addresses into CIDRized addresses: 11000110 10110111 10100000 00000000 to 11000110 10110111 10111111 11111111arrow_forwardالسؤال 2 Consider sending a 3500 byte datagram into a link that has an MTU of 1400 bytes. Suppose the original datagram is stamped with the identification number 333.a) How many fragments are generated? b) What are the values of the various fields, related to fragmentation, in each generated IP fragment?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY