
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
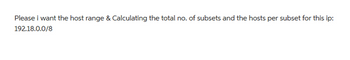
Transcribed Image Text:Please i want the host range & Calculating the total no. of subsets and the hosts per subset for this ip:
192.18.0.0/8
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps with 2 images

Knowledge Booster
Similar questions
- Which component of the IP header may be modified to make certain that a data packet will go through no more than N routers on its way to the location specified in the header?arrow_forwardWhich of the following IP addresses are used to identify a TCP socket?arrow_forwardIn the URL "http://www.u.arizona.edu/~wtn", what part of the URL defines the hosting server? Question 3 options: www http:// u.arizona.edu ~wtnarrow_forward
- Find the IP addresses of these websites. Tools: You can use the ŋsleekun or ping command in your terminal/command prompt. Fill the table below with your solutions. Website www.usp.ac.fj www.facebook.com www.youtube.com IP Address Range Nelookup Results Update the ALC template below to block the identified IP ranges for the above websites. Router(config)# access-list 10 deny Router(config)# access-list 10 permit any Router(config)# interface IDE> Router(config-if)#ip access-group 10 in Router(config-if)#exit Explanation: • • • • • -list 10: Creates a standard ACL with number 10. dany : Blocks traffic from the specified IP address. Example: =====-list 10 dany 192.168.1.0 0.0.0.255 will block the range 292.168.1.0 to 192.168.1.255. permit any: Allows all other traffic not specified in the deny rule. interface : Applies the ACL to a specific interface (e.g.. GigabitEthernet0/0). -group 10 in Applies the ACL in the inbound direction on the interface. Cybersecurity Policies/Acts in Fiji…arrow_forwardFind the first ICMP Echo Request message that was sent by your computer after you changed the Packet Size in pingplotter to be 2000. Q6) Has that message been fragmented across more than one IP datagram? If so, how many? Q7) What information in the IP header indicates that the datagram been fragmented? What information in the IP header indicates whether this is the first fragment versus a last fragment?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY