
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Match the

Transcribed Image Text:12
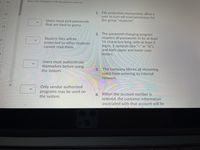
Only vendor-authorized
programs may be used on
the system.
4. When the account number is
entered, the customer information
associated with that account will be
retrieved and displayed.
15
18
Customers of the store may
use the web to check their
accounts.
5. The login mechanism checks that
the password entered corresponds
to the user account entered.
1
Employees may not stream
videos during work hours.
Only users physically
present at the system can
6. Each program will be checked to
ensure it is approved for use by the
vendor before the program is run.
use it.
7. Networks have been disconnected
from the system.
Transcribed Image Text:Match the mechanism with the policy it enforces.
12
1. File protection mechanisms allow a
user to turn off read permission for
the group "students".
15
Users must pick passwords
that are hard to guess.
18
Student files will be
protected so other students
cannot read them.
2. The password changing program
requires all passwords to be at least
16 characters long, with at least 2
digits, 2 symbols (like "+" or "@"),
and both upper and lower case
letters.
21
Users must authenticate
themselves before using
the system.
The company blocks all streaming
video from entering its internal
network.
3.
Only vendor-authorized
programs may be used on
the system.
4. When the account number is
entered, the customer information
associated with that account will be
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps with 2 images

Knowledge Booster
Similar questions
- In the context of information security, a threat is any action or occurrence that might have a negative outcome for a computer system or application that is enabled by a vulnerability.a) Specify the many ways in which computer systems may be compromised.arrow_forwardJustify why a management role, rather than the user Satoshi, should provide a permission when a manager, say Satoshi, approves it.arrow_forwardJustify why a management role, rather than the user Satoshi, should provide a permission when a manager, say Satoshi, approves it.arrow_forward
- Question 43 --- are usually enough to satisfy physical security in most situations. deterrent physical controls detective physical controls preventive physical controls none of these optionsarrow_forwardHow likely are there to be security concerns throughout the process of outlining an approach and key milestones?arrow_forwardAn anticipatory breach is: Group of answer choices The process of rescinding for breach. Retrospective in operation. A form of repudiation. When a party fails to perform on time.arrow_forward
- writing organization policy. Name of the policy (Security Awareness and Training Policy) 2. Policy Definition: 3. Purpose 4. Scope 5. Target Audience or Applicability 6. Objectives: Information security is deemed to safeguard three main objectives: • Confidentiality - data and information assets must be confined to people authorized to access and not be disclosed to others; • Integrity - keeping the data intact, complete and accurate, and IT systems operational; • Availability - an objective indicating that information or system is at disposal of authorized users when needed. 7. Standard 8. Roles and Responsibilities 9. Procedures and Guidelines 10 Compliance and Enforcement 11. Non-Compliance and Exceptions 12. Referencesarrow_forwardWhen referring to a specific circumstance, what precisely does it imply when someone says that they have "system security"?arrow_forwardGive a personal example in which a compliance strategy was successfully used. Describe the situation, name the strategy and state the principle on which the strategy is based.arrow_forward
- Book title: Cybersecurity Essentials - Charles J. BrooksChapter 1 - Infrastructure security in the Real world From the information provided in the first scenario, consider the National Institute of Standards and Technology (NIST) functions detailed in this section and observe how they relate to each category. 1. Which steps could be put in place to recover from actions intended to access, disable, degrade, or destroy the assets that has been previously identified (NIST RC.RP-1)? (Refer to screenshot for reference)arrow_forwardWhat is the primary objective of keeping audit logs?arrow_forward________ is a long-standing connection or bond with others. A) attaching B) security C) The term "reguard" D) The term "attachment"arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY