
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Consider the schedule S1 consists of three transactions T1, T2, T3 as the following:
Answer the following question:
- Is the schedule S1 cascadeless and recoverable? Justify your answer.
- Draw the precedence graph of schedule S1
- Is S1 conflict-serializable? Explain briefly. If S1 is conflict-serializable, write down all equivalent serial schedules.
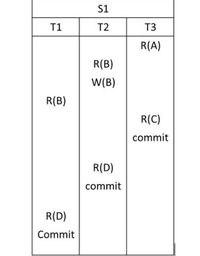
Transcribed Image Text:S1
T1
T2
T3
R(A)
R(B)
W(B)
R(B)
R(C)
commit
R(D)
commit
R(D)
Commit
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 1 images

Knowledge Booster
Similar questions
- Justify why log entries for undo-list transactions must be processed in reverse order, but redo is done in the other manner.arrow_forwardWhat is the meaning of “Atomic” with regards to atomic transactions in relational databases? a. A correctly executed transaction is not susceptible to system failures. b. Concurrent execution of transactions does not lead to incorrect results. c. Execution of a transaction does not invalidate the data. d. a) A transaction is either executed completely or not at all. How does taxation handle the issue of spider traps while computing PageRank? a. a) It allows a random surfer to teleport to a random web page with a certain probability. b. It prevents a surfer from going to any web page that is part of a spider trap. c. It repositions a random surfer to the starting web page when it visits a web page that is part of a spider trap. d. None of the abovearrow_forwardHow do "savepoints" differ from regular commit points in transaction lifecycles?arrow_forward
- 1) How many serial schedules exist for the three transactions in the following figure? What are they? What is the total number of possible schedules? Transaction T₁₂ read_item(X); write_item(X); read_item(Y); write_item(Y); Transaction T₂ read_item(Z); read_item(Y); write_item(Y); read_item(X); write_item(X); Transaction T3 read_item(Y); read_item(Z); write_item(Y); write_item(Z);arrow_forwardConsider a multi-granularity locking system, with lock modes S, X, IS, IX, and SIX as in lecture and database-level, file-level, page-level and record-level locking as shown in the following figure. Provide the sequence of lock requests required to perform the following transactions and write necessary complete Lock and Unlock operations in their correct order. T3 want to read all pages in F1 and modify about 10 pages, which can be identified only after reading F1.(MY ANSWER) Lock-SIX(DB); Lock-S(F1); Lock-X(P1); Lock-X(P1000); Unlock(P1000); Unlock(P1); Unlock(F1); Unlock(DB); is it corect? ………………………………………………………………………………………arrow_forwardMany applications need to generate sequence numbers for each transaction. a. If a sequence counter is locked in two-phase manner, it can become a concurrency bottleneck. Explain why this may be the case. b. Many database systems support built-in sequence counters that are not locked in two-phase manner; when a transaction requests a sequence number, the counter is locked, incremented and unlocked. i. Explain how such counters can improve concurrency. ii. Explain why there may be gaps in the sequence numbers belonging to the final set of committed transactions.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY