
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
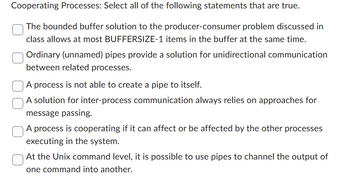
Transcribed Image Text:Cooperating Processes: Select all of the following statements that are true.
The bounded buffer solution to the producer-consumer problem discussed in
class allows at most BUFFERSIZE-1 items in the buffer at the same time.
Ordinary (unnamed) pipes provide a solution for unidirectional communication
between related processes.
A process is not able to create a pipe to itself.
A solution for inter-process communication always relies on approaches for
message passing.
A process is cooperating if it can affect or be affected by the other processes
executing in the system.
At the Unix command level, it is possible to use pipes to channel the output of
one command into another.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Consider a computer environment in which there are 4 magnetic drives, 2 printers, 3 scanners, and 1 optical drive. Three processes P1, P2, P3 are using these resources. At any point in time, the allocations and requests for these resources are as follows. Allocations: Magnetic drive Printer Scanner Optical drive P1 1 P2 2 1 P3 1 Requests: Magnetic drive 2 Printer Scanner Optical drive P1 1 P2 1 1 P3 2 1 Is there any way that the processes can complete without deadlock? If yes, explain how. If not, explain why not.arrow_forwardSchedulers: Select all of the following statements that are true. A long-term scheduler selects which process should be executed next and allocates the CPU. The main task of a medium-term scheduler is to swap out and in processes from memory. A long-term scheduler executes much more often than a short-term scheduler. The long-term scheduler controls the degree of multiprogramming. The ready queue contains the set of all processes residing in main memory, ready and waiting to execute. Device queues refer to processes waiting for an I/O device.arrow_forwardCode must be in C/C++ language using MPI Suppose comm_sz = 8 and the vector x = (0,1,2,...,15) has been distributed among the processes using a block distribution. Implement an allgather operation using a butterfly structured communication (see diagram below) and point-to-point communication functionsarrow_forward
- In a printing queue, there are a few documents that are still waiting to be printed. To get the documents running, the person in charge of printing executes a series of random activities. Which type of scheduling is best for the aforementioned circumstance, and why?arrow_forward1- True or False : Switching time should be high for faster execution. 2-What is the protocol that used to solve the priority inversion problem.arrow_forward3. I/O Management: Disk Arm Scheduling & RAIDa. It is known that a disk drive has 256 cylinders, with cylinder numbers starting from 0 and ending at 255. The position of the needle on the disk drive currently stops at 128. It is also known that the needle always “goes to the cylinder with the smaller number first”. The order of the positions visited sequentially is: 254, 64, 32, 100, 50, 70. From the 3 choices of algorithms below, which one is the best algorithm? Make each image and determine the seektime.i. SCANii. C-SCANiii. FIFOarrow_forward
- Multi-tasking can not be achieved with a single processor machine. True False 2. Async/Await is best for network bound operations while multi-threading and parallel programming is best for CPU-bound operations. True False 3. The following is a characteristic of an async method:The name of an async method, by convention, ends with an "Async" suffix. True False 4. Using asynchronous code for network bound operations can speed up the time needed to contact the server and get the data back. True False 5. Asynchronous programming has been there for a long time but has tremendously been improved by the simplified approach of async programming in C# 5 through the introduction of: The Task class True Falsearrow_forwardme remaining: 00:09:34 Computer Science Create a MPI version of the program below that uses a striped decomposition. Each process is responsible for some number of columns of the square and also maintains two columns of ghost cells to mirror the columns on the neighboring processes. The ghost cells are needed in order to update the cells along the process boundary. At each time step, a ghost cell exchange takes place, then the update takes place. #include <stdlib.h> #include <assert.h> #include "anim.h" const int n = 200; // number of discrete points including endpoints int nstep = 200000; // number of time steps int wstep = 400; // time between writes to file const double m = 100.0; // initial temperature of rod interior const int h0 = n/2 - 2, h1 = n/2 + 2; // endpoints of heat source const double k = 0.2; // diffusivity constant char * filename = "diff2d.anim"; // name of file to create double ** u, ** u_new; // two copies of the temperature function ANIM_File…arrow_forwardWireless sensor networks (WSNs) are an example of a network that may facilitate communication. Sensing nodes in WSNS communicate with one another and a central hub. The computing resources and storage space of a sensor node are limited. Think of an algorithm that can be solved by separating it into smaller chunks. To solve these subproblems at separate sensor nodes, would you prefer use divide and conquer or dynamic programming? Please be brief in your writing.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY