
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
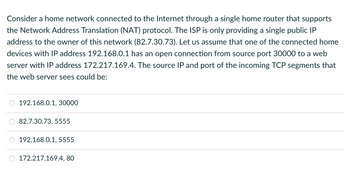
Transcribed Image Text:Consider a home network connected to the Internet through a single home router that supports
the Network Address Translation (NAT) protocol. The ISP is only providing a single public IP
address to the owner of this network (82.7.30.73). Let us assume that one of the connected home
devices with IP address 192.168.0.1 has an open connection from source port 30000 to a web
server with IP address 172.217.169.4. The source IP and port of the incoming TCP segments that
the web server sees could be:
192.168.0.1, 30000
82.7.30.73, 5555
192.168.0.1, 5555
172.217.169.4, 80
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- A router running Classless Interdomain Routing (CIDR) has the following entries in its routing table: Address/mask Next hop 135.46.56.0/22 Interface 0 135.46.60.0/22 Interface 1 192.53.40.0/23 Router 2 Default Router 3 How does a CIDR router work to route the packets it received? For each of the following IP addresses, what will the router do if a packet with that address arrives? (a) 135.46.63.10 (b) 135.46.58.16 (c) 135.46.52.2 (d) 192.53.40.7 (e) 192.53.56.7arrow_forwardThe following questions are related to HTTP protocol Q1. The first line of a HTTP request from some client to some server is basically made of where the web page file path is added. The path is shown as folders separated by slash. Q2. If an HTTP server responds to a client request and the response is a success, what is the http code and string that marks a success response? Must provide the code and the string as they appear in TCPDump or Wireshark traces. (note: use upper case for the string and also proper spacing in you answers. Keep the order of the string and the code as seen in TCPDump) Answer: code and string that marks a success response Q3. What http header field is used to identify an address of a web page (i.e. the URI) that linked to the resource currently being requested. This field indicates the last page the user/requester was on by the time they link to the requested page. Answer: The field that indicates the last page the user/requester was on is Q4. What is the http…arrow_forwardwhat valid host range is the ip address 192.168.112.173/28 a part of , Instead of using a standard dot-decimal format, the subnet mask, which is /28, of this IP is shown in CIDR representation (we'll talk about it later in class). The 28 after slash tells the first 28 bits of the given IP are network ID bits, which also implies the rest of 32-28 or 4 bits of the given IP are host ID bits. In other words, subnet mask /28 is equivalent to 255.255.255.240 in dot-decimal format. In the answer of this question, find the minimum IP of the host range, and find maximum IParrow_forward
- Make a map → from source to destination there are many routes that can be taken within the map. Connect the 5 routers → name it A (has 3 connections), B (has 2 connections), C (has 2 connections), D (has 2 connections), and E (has 1 connection). IP addressing: LAN A1 A2 A3 B1 B2 C1 C2 D1 D2 E1 Network Address 192.168.1.0 192.168.2.0 192.168.3.0 192.168.10.0 192.168.11.0 192.168.20.0 192.168.21.0 192.168.32.0 192.168.33.0 192.168.40.0 Subnet Mask /24arrow_forwardLet's say that Host C is running a Web server that listens on port 80. Suppose that this web server is able to maintain persistent connections and responds to requests from both Host A and Host B. Is Host C sending all of the requests over the same connection, or are there many sockets in use? Do each of them have port 80 even though they are broadcast over separate sockets? It's something you need to discuss and provide some clarification on.arrow_forwardCan someone please help me with this? I'll give a thumb up to thank for your time.As I'm reviewing for my upcoming exam, I really need an answer from an expert in the field. Please do not send me an answer from chatGPT. I've got enough of that, so please be helpful.arrow_forward
- An IP address can be written as a 32-bit number. For a class B network, the two most significant bits are set to 10. The 16 most significant bits are used as a network ID, and the 16 least significant bits are used as a host ID. However, the host ID cannot be all O's or all 1's. How many hosts (i.e., host IDs) can there be on a class B network? Type your answer.arrow_forwardEthernet, for example, is a connectionless protocol that specifies the path taken by a packet between its source and destination addresses. However, a protocol that is connection-oriented, such as ATM, specifies the path taken by a cell using virtual connection IDs (VPIs and VCIs). Could you please elaborate on this statement?arrow_forwardSimultaneous TCP connection initiations are rare, but simultaneous connection termination is relatively common. How do two TCP nodes negotiate the simultaneous sending of FIN packets to one another? Draw the ladder diagram, and label the states on each side. Which node goes into TIMEWAIT state?arrow_forward
- Consider the following virtual circuit network with three reserved virtual circuits: уC1: H1, А, С, Е, Н2 VC2: H3, A, F, D, H4 ус3: НЗ, А, F, D, E, H2 Host H4 Host H3 Нost H2 Host H1 Draw the routing table of router D and the routing table of router C. *you may design a table using the HTML editor or write the content of routing table record by record (record per line).arrow_forwardDownload delays for 100 objects (HTTP 1.1 with browser caching). Consider an HTTP 1.1 client and server. The RTT delay between the client and server is 2 seconds. Suppose the time a server needs to transmit an object into its outgoing link is 3 seconds, as shown below for the first of these 100 requests. initiate TCP connection RTT request file RTT file received time You can assume that any other HTTP message not containing an object sent by the client and server has a negligible (zero) transmission time. Suppose the client makes 100 requests, one after the other, waiting for a reply to a request before sending the next request. 352 secs Using HTTP 1.1, how much time elapses between the client transmitting the first request, and the receipt of the last requested object, assuming the client uses the IF- MODIFIED-SINCE header line, and 50% of the objects requested have not changed since the client downloaded them (before these 100 downloads are performed)? 350 secs 252 secs time to…arrow_forward7.1 In IEEE 802.11, open system authentication simply consists of two communications. An authentication is requested by the client, which contains the station ID (typically the MAC address). This is followed by an authentication response from the AP/router containing a success or failure message. An example of when a failure may occur is if the client's MAC address is explicitly excluded in the AP/router configuration. a. What are the benefits of this authentication scheme? b. What are the security vulnerabilities of this authentication scheme?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY