
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question

Transcribed Image Text:Consider a cryptosystem in which the key space contains exactly 3
keys and the keys are chosen with equal probability. Find H(K).
O In3
O In3/In2
O In2
O In2/In3
O In6/In2
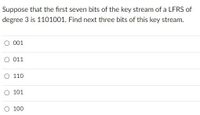
Transcribed Image Text:Suppose that the first seven bits of the key stream of a LFRS of
degree 3 is 1101001. Find next three bits of this key stream.
O 001
O 011
O 110
O 101
O 100
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps with 2 images

Knowledge Booster
Similar questions
- For the given scenario where Alice is trying to send encrypted data to Bob, and Bob is trying to decrypt it, using Elgamal encryption scheme, fill the values in the tablearrow_forwardConsider a knapsack cryptosystem with a =[2, 6, 12, 45, 70, 151). If the knapsackSum = 208, find the values for x.arrow_forward4) Consider a simple RSA example. To generate, say, Bob's keypair, we select two "large" primes, p=17 and q=3. Calculate all the things needed, choosing as the encryption exponent e=3. Which one of the following is Bob's public key? A (11,32) B (11,51) C (17,32) D (3, 32) E (17,51) F (3, 51)arrow_forward
- For affine cipher, the key is a pair (a,b) for a,b<26. The encryption algorithm is E(x)=(ax+b) mod 26. And the decryption algorithm is D(y)=a¹(y-b) mod 26. Note that we map A, B, C, D, ... to numbers 0, 1, 2, 3, ... respectively. Assume that K=(7,3), then E(x)=(7x+3) mod 26, and 7-1-15. Thus D(y)=15(y-3) mod 26. 1. For the key K=(7,3), computer the cipher text for "GOLUNCH" is (please use all capital letters) 2. For the key K=(7,3), try to decrypt the cipher text "YHQQFPGHJF" is (please use all capital letters)arrow_forwardRecall that the sponge construction describes how to turn a public random permutation into a cryptographic hash function. Once the data to be hashed has been padded, the next step is to absorb the data r bits at a time. blk = <0>while not done: xor the next r bits of data into the first r bits of blk blk = p(blk) As a convenient (but not secure because it's too small) public random permutation, lets use the AES S-box for p. What is blk after absorbing each of the following when r=4 bits. Give your answer as exactly either 2 hexadecimal digits or 8 binary digits with no spaces (eg, 0A or 00001010). Note that the data is already padded and you should restart at blk=<0> each for each computation Data: 1001 Resulting blk:____ Data 10011001 Resulting blk:_____ Data 100110011001 Resulting blk:____arrow_forwardConsider the following Cryptarithmetic problems. Write out all of the variables, domains, and constraints of the problem. DON'T SOLVE THE PROBLEM.a. SATURN+ URANUS= PLANETS b. YESSENDME+ MORE= MONEYarrow_forward
- Cryptographic Data ObjectsB has just received the following message, which represents a cryptographic data object:{({(KPbB)KPrS mod KPbS}K1,{|(NB, NA, {{({K2}KPbB, NS)}(G1)KPrA mod NA}K1, {|{({G3}(KPbA)KPrS mod KPbS, G2)}K1|}KPrB)|}KPrA)}KBSThe following explains various terms in this object and some of the abbreviations used:• {M}K represents the encryption of some message/data M using the key K• {|M|}K represents the digital signing of some message/data M using the key K• NX represents a nonce (i.e. a fresh and possibly random number used once only) generatedby X• KpbX represents the public part of the key pair presumably owned by X• KprX represents the private part of the key pair presumably owned by X• KAB represents a symmetric key shared between A and B• K (or K1, K2, K3 etc.) represents some arbitrary key with no assumptions about its scope• M represents some alphanumeric/textual message with no assumptions• G1, G2, G3 etc. are prime numbersWhich of the following sets of keys,…arrow_forwardWhy can't Bob use the pair (6; n) as an RSA public key, where n = pq, for two large primes, p and q?arrow_forwardMany forms of cryptography are based on the following discrete log problem. Choose a cyclic group G (produced by one generator g) with finitely many elements. Alice and Bob want to set up a secret communication and need a secret key for that, which becomes a group element from G. They set up the following exchange (the so-called Diffie-Hellman protocol): 1. Alice chooses a secret group element a and sends unsecured g^a to Bob 2.Bob chooses a secret group element b and sends unsecured g^b to Alice 3. Alice calculates (g^b )^a and keeps this group element secret 4.Bob calculates (g^a )^b and keeps this group element secret Since a cyclic group is abelian, Alice and Bob now share the secret key (g^b )^a=(g^a )^b. The blue group elements are publicly known, the red elements are secret. The discrete log problem presented to an eavesdropper is computing say a from the publicly known data G,g,g^a. The naming of the problem comes from the solution a= glog(ga ) which is generally difficult to…arrow_forward
- Question 4. A sealed-bid auction is a process where a number of partiescalled bidders submit sealed bids for buying some item. Once all sealed bidshave been submitted, the bids are revealed and the highest bidder is the onethat buys the item.Suppose that the following cryptographic primitives are available:• A fully secure public-key encryption scheme (e.g., RSA-OAEP) thatconsists of the key-generation algorithm PKE.Gen, the encryption algorithm Enc, and the decryption algorithm Dec.• An existentially unforgeable digital signature scheme (e.g., RSA-FDH)that consists of the key-generation algorithm DS.Gen, the signing algorithm Sign, and the verification algorithm Vrfy.• A trusted certificate authority (CA) that can be used to issue publickey certificates for any party.Using the cryptographic primitives above, design and analyse an electronic sealed-bid auction protocol according to the following guidelines:• The parties involved in the auction are: (i) an auction administrator(AA) and…arrow_forwardQuestion 4. A sealed-bid auction is a process where a number of partiescalled bidders submit sealed bids for buying some item. Once all sealed bidshave been submitted, the bids are revealed and the highest bidder is the onethat buys the item.Suppose that the following cryptographic primitives are available:• A fully secure public-key encryption scheme (e.g., RSA-OAEP) thatconsists of the key-generation algorithm PKE.Gen, the encryption algorithm Enc, and the decryption algorithm Dec. • An existentially unforgeable digital signature scheme (e.g., RSA-FDH)that consists of the key-generation algorithm DS.Gen, the signing algorithm Sign, and the verification algorithm Vrfy. • A trusted certificate authority (CA) that can be used to issue publickey certificates for any party.Using the cryptographic primitives above, design and analyse an electronic sealed-bid auction protocol according to the following guidelines: • The parties involved in the auction are: (i) an auction administrator(AA)…arrow_forward2. Machine learning techniques can be built for trading algorithms of cryptocurrencies. true falsearrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY