
C++ Programming: From Problem Analysis to Program Design
8th Edition
ISBN: 9781337102087
Author: D. S. Malik
Publisher: Cengage Learning
expand_more
expand_more
format_list_bulleted
Question
help with this assembly computer science question
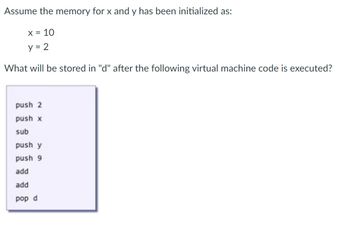
Transcribed Image Text:Assume the memory for x and y has been initialized as:
x = 10
y = 2
What will be stored in "d" after the following virtual machine code is executed?
push 2
push x
sub
push y
push 9
add
add
pop d
SAVE
AI-Generated Solution
info
AI-generated content may present inaccurate or offensive content that does not represent bartleby’s views.
Unlock instant AI solutions
Tap the button
to generate a solution
to generate a solution
Click the button to generate
a solution
a solution
Knowledge Booster
Similar questions
- (Practice) Although the total number of bytes varies from computer to computer, memory sizes of millions and billions of bytes are common. In computer language, the letter M representsthe number 1,048,576, which is 2 raised to the 20th power, and G represents 1,073,741,824, which is 2 raised to the 30th power. Therefore, a memory size of 4 MB is really 4 times 1,048,576 (4,194,304 bytes), and a memory size of 2 GB is really 2 times 1,073,741,824 (2,147,483,648 bytes). Using this information, calculate the actual number of bytes in the following: a. A memory containing 512 MB b. A memory consisting of 512 MB words, where each word consists of 2 bytes c. A memory consisting of 512 MB words, where each word consists of 4 bytes d. A thumb drive that specifies 2 GB e. A disk that specifies 4 GB f. A disk that specifies 8 GBarrow_forwardIn the ________, memory addresses consist of a single integer.arrow_forward_____ is a CPU design technique in which instruction execution is divided into multiple stages and different instructions can execute in different stages simultaneously.arrow_forward
- How is an array stored in main memory? How is a linked list stored in main memory? What are their comparative advantages and disadvantages? Give examples of data that would be best stored as an array and as a linked list.arrow_forwardDevelop a program consisting of primitive CPU instructions to implement the following procedure: integer i,a; i = 0; while (i 10) do a = i2; i = i + 1; endwhilearrow_forwardIf a microprocessor has a cycle time of 0.5 nanoseconds, what’s the processor clock rate? If the fetch cycle is 40% of the processor cycle time, what memory access speed is required to implement load operations with zero wait states and load operations with two wait states?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning
C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT
EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning,
Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning, Systems ArchitectureComputer ScienceISBN:9781305080195Author:Stephen D. BurdPublisher:Cengage Learning
Systems ArchitectureComputer ScienceISBN:9781305080195Author:Stephen D. BurdPublisher:Cengage Learning C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr
C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr CompTIA Linux+ Guide to Linux Certification (Mind...Computer ScienceISBN:9781305107168Author:Jason EckertPublisher:Cengage Learning
CompTIA Linux+ Guide to Linux Certification (Mind...Computer ScienceISBN:9781305107168Author:Jason EckertPublisher:Cengage Learning

C++ Programming: From Problem Analysis to Program...
Computer Science
ISBN:9781337102087
Author:D. S. Malik
Publisher:Cengage Learning

EBK JAVA PROGRAMMING
Computer Science
ISBN:9781337671385
Author:FARRELL
Publisher:CENGAGE LEARNING - CONSIGNMENT

Microsoft Visual C#
Computer Science
ISBN:9781337102100
Author:Joyce, Farrell.
Publisher:Cengage Learning,

Systems Architecture
Computer Science
ISBN:9781305080195
Author:Stephen D. Burd
Publisher:Cengage Learning

C++ for Engineers and Scientists
Computer Science
ISBN:9781133187844
Author:Bronson, Gary J.
Publisher:Course Technology Ptr

CompTIA Linux+ Guide to Linux Certification (Mind...
Computer Science
ISBN:9781305107168
Author:Jason Eckert
Publisher:Cengage Learning