
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Packet Tracer - Configure NAT for IPv4
Objectives
Configure Dynamic NAT with PAT
Configure Static NAT
Background / Scenario
In this lab, you will configure a router with dynamic NAT with PAT. This will translate addresses from the three internal LANs to a single outside address. In addition, you will configure static NAT to translate an internal server address to an outside address.
Instructions
In this activity you will only configure router R2.
- Use a named ACL to permit the addresses from LAN1, LAN2, and LAN3 to be translated. Specify the LANs in this order. Use the name R2NAT. The name you use must match this name exactly.
- Create a NAT pool named R2POOL. The pool should use the first address from the 209.165.202.128/30 address space. The pool name you use must match this name exactly. All translated addresses must use this address as their outside address.
- Configure NAT with the ACL and NAT pool that you have created.
- Configure static NAT to map the local.pka server inside address to the second address from the 209.165.202.128/30 address space.
- Configure the interfaces that will participate in NAT.
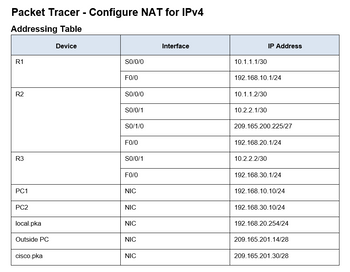
Transcribed Image Text:Packet Tracer - Configure NAT for IPv4
Addressing Table
R1
R2
R3
PC1
PC2
local.pka
Outside PC
cisco.pka
Device
SO/0/0
FO/O
S0/0/0
SO/0/1
SO/1/0
FO/O
SO/0/1
FO/0
NIC
NIC
NIC
NIC
NIC
Interface
10.1.1.1/30
192.168.10.1/24
10.1.1.2/30
10.2.2.1/30
IP Address
209.165.200.225/27
192.168.20.1/24
10.2.2.2/30
192.168.30.1/24
192.168.10.10/24
192.168.30.10/24
192.168.20.254/24
209.165.201.14/28
209.165.201.30/28
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- Remember that the TCP/IP protocol suite's transport step reassembles and reorders packets. If needed, a firewall may operate at the Internet or data layer. A stateful inspection firewall cannot learn about a traffic stream that is damaged or deleted?arrow_forwardWhat are the advantages of placing cryptographic algorithms at the network layer? 1. Applying an authentication algorithm on an IP packet in the transport mode will affect routing this packet and so a gateway is not needed to route the packet. 2. It is impossible to obtain a port number from an encrypted IP packet in the transport mode. 3. Encrypting payloads only will make it impossible to analyze traffic. 4. Application-layer applications will not be affected by encryption or authentication algorithms. 5. Encrypted IP packets in the tunnel mode are not visible to the gateways on the routing path. 6. Applying an encryption algorithm on an IP packet in the tunnel mode will make it impossible to route this packet and so a gateway is needed to route the packet.arrow_forwardTrue or False (Include valid reason) a) A backdoor is another way into a system or program bypassing the main system authentication. Hence, all backdoors have malicious intent. b) One way to mitigate ARP spoofing attack on a host is to set static IP-to-MAC assignments on its ARP cache.arrow_forward
- IP Header has a field TTL ( Time To Live). Which among the following statement best explain the use of TTL(a) It can be used to prioritize the packets(b) It can be used to reduce the delay.(c) It can be used to optimize the throughput.(d) It can be used to prevent packet looping.arrow_forwardquestion 58 please quickly thanks !arrow_forwardSelect all statements that correctly describe network packet filtering at the IP layer? (Select all that apply) a. IP packet filtering may either be applied to the perimeter of a network or to the individual hosts within a network, but it cannot be applied to both at the same time. O b. IP packet filtering determines which IP packets may flow into or out of a network or a computer. O c. Most IP packet filtering firewalls determine what packets to filter based upon a set of rules which can be configured for a particular network or host. Od. Most IP packet filtering firewalls determine what to filter based upon the IP header fields.arrow_forward
- Please explain what subnet mask 255.255.255.252 (/30) is and how it can be used to enhance network security with an example.arrow_forwardFTP doesn't have a built-in method for tracking the progress of files that have been sent to clients. File Transfer Protocol (FTP) depends on a different protocol at the TCP/IP architecture's Transport layer to guarantee a successful transfer.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY