
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Given the Nondeterministic Finite Automaton (NFA). Need help proving, by induction on n, that for all positive integers n, the string (aba)n is accepted by this NFA. (This string is obtained by n repetitions of aba.) Thank you :)
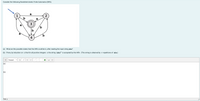
Transcribed Image Text:Consider the following Nondeterministic Finite Automaton (NFA).
a
1
a
a
4
(a) What are the possible states that this NFA could be in, after reading the input string aba?
(b) Prove, by induction on n, that for all positive integers n, the string (aba)" is accepted by this NFA. (This string is obtained by n repetitions of aba.)
Paragraph
B
(a)
|(b)
Path: p
3.
Expert Solution
arrow_forward
Step 1
(a) There are two possible states after string (aba)^n, that is
1. 1 -> a -> 2 -> b -> 4 -> a -> 1, which is non final state
2. Final state, 1 -> a -> 4 -> b -> 2 -> a -> 3
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- This is Discreet math please answer questions with proper formatting for proofsarrow_forwardLet ƒ : Z → Z be some function over the integers. Select an appro- priate proof technique (direct, contradiction, induction, invariant or pigeonhole), and prove that if you have: a, f(a), ƒ(f(a)), ƒ(f(f(a))) and f(f(f(f(@)))), then at least 2 of those numbers are equivalent modulo 4.arrow_forwardMake a truth table for the following expression [8]:(a) ¬[(¬p −→ q) ∨ (¬p ∧ ¬q)] (b) Based on your truth table, classify the above expressionarrow_forward
- 2arrow_forwardBig-Oh. For each function f in the left column of the following table,choose one expression O(g) from the following list:O(1/n),O(1),O(log2 n),O(n),O(n log2 n),O(n2),O(n10),O(2n),O(10n),O(nn)such that f ∈ O(g). Use each expression only once.arrow_forwardProve that the sum of the first n odd positive integers is n2. In other words, show that 1 + 3 + 5 + .... + (2n + 1) = (n + 1)2 for all n ∈ N.arrow_forward
- Use strong induction to prove the following:arrow_forwardProve by Induction that for all integers n ≥ 1, n < n2 + 1 .Yes this problem is silly, but still do it by induction! Prove by Induction that for all integers n ≥ 3, 2n < n2 .arrow_forwardProve the following by induction, substitution, or by definition that 13n+ 10 = O(n²). Definition of Big O f(n) = O(g(n)) means there are positive constants c and no, such that ≤ f(n) ≤ cg(n) for all n ≥ no.arrow_forward
- Exhibit an enumeration to show that the set of all tuples (of any finite length) of nonnegative integers is countable. Please don't copy from other questions.arrow_forwardProve by induction that fib(0)+fib(1)+…+fib(n) = fib(n+2)-1, fib(0)=0 fib(1)=1arrow_forwardExpand the following recurrence to help you find a closed-form solution, and then use induction to prove your answer is correct. T(n) = √nT(√n) + n, for n>2; T(2) = 1.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY