
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
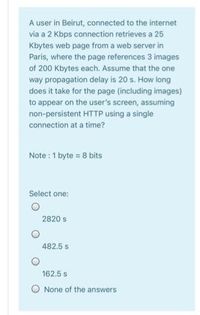
Transcribed Image Text:A user in Beirut, connected to the internet
via a 2 Kbps connection retrieves a 25
Kbytes web page from a web server in
Paris, where the page references 3 images
of 200 Kbytes each. Assume that the one
way propagation delay is 20 s. How long
does it take for the page (including images)
to appear on the user's screen, assuming
non-persistent HTTP using a single
connection at a time?
Note :1 byte = 8 bits
Select one:
2820 s
482.5 s
162.5 s
None of the answers
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- A frame containing http request is sent from Computer (A) [in whichever subnet it is now, make sure to show it in your figure], to the access point it is associated with. Draw the address fields (1, 2, and 3) of the frame travelling from Computer A to AP and the source and destination addresses of the frame travelling from AP to R1. The MAC addresses of AP1, AP2, and AP3 are M1, M2, and M3 respectively, and the Router R1’s MAC address connected to this Switch/AP is MRA. IP address values are already given, and the port addresses could also be used as given. The Router’s MAC address facing WAN side is MRW.arrow_forward42. Though there are practical reasons why we don't complicate our lives this way in the real world, from a theoretical perspective we could borrow non-consecutive bits for subnetting. So, when borrowing the first host bit, the second host bit and the last two host bits (counting from the left of the host bit field) from 172.1.0.0 can you determine the following: d. number of remaining host bits and then the number of useable hosts on a subnet?e. First useable host on the 2nd useable subnet?f. broadcast address for 2nd useable subnet?arrow_forwardnetwork. ii. Consider an application that transmits datalat a steady rate.(for example, the sender generates an N-bit unit of data every k time units, where k is small and fixed). Also, when such an application starts, it will continue running for a relatively long period of time. Answer the following questions, briefly justifying your answer: Would a packet-switched network or a circuit-switched network be more appropriate for this application? Provide reason for your answer. iii. Discuss the difference between best effort delivery and guaranteed delivery. Give two examples for each delivery.arrow_forward
- A telephone modem is used to connect a personal computer to a host computer. The speed of the modem is 56 kbps, the one-way propagation delay is 100 ms, the packet size is 256 bytes, and the probability of an error in a packet is 10^-4. Find the efficiency of stop-and-wait ARQ. What window size N is needed to keep the channel busy when there are no transmission errors. For this window size finds the efficiency of the go-back-N and selective repeat protocols. Note: Correct and detailed answer will be Upvoted else downvotedarrow_forwardIn modern packet-switched networks, including the Internet, the source host segments long, application-layer messages (for example, an image or a music file) into smaller packets and sends the packets into the network. The receiver then reassembles the packets back into the original message. We refer to this process as message segmentation. Figure 1.27 illustrates the end-to-end transport of a message with and without message segmentation. Consider a message that is 8. 106 bits long that is to be sent from source to destination in Figure 1.27. Suppose each link in the figure is 2 Mbps. Ignore propagation, queuing, and processing delays. a. Consider sending the message from source to destination without message segmentation. How long does it take to move the message from the source host to the first packet switch? Keeping in mind that each switch uses store-and-forward packet switching, what is the total time to move the message from source host to destination host? b. Now suppose that…arrow_forwardQarrow_forward
- internet Checksum. Consider the two sixteen bit numbers: 10110100 01000110 00001000 01101110 Compute the Internet Checksum of these two values Enter the 2 bytes each as an 8-bit number with only O's and 1's, and make a single blank space between the two 8-bit numbers (e.g., 01010101 00101000).arrow_forwardThe token bucket algorithm is a popular method for traffic shaping. A computer uses a token bucket with acapacity of 400 megabytes (MB) and a rate of 10 MB/sec. The computer continuously generates20 MB/sec for transmission from time 0. Assume the bucket’s water level is 200 MB at time 0.1a. How long will it take to send 1000 MB? Show the steps.1b. Draw a figure showing how the bucket’s water level evolvesarrow_forwardGiven that the main memory size is 32KB, the page size is 64B, the word size is 1B, and n-level paging is applied. What is the value of n?arrow_forward
- Consider 7-bit messages that we encode into 11-bit codewords using 4 parity bits. Thus our codewords look like: ⟨a, b, c, d, e, f, g, p1, p2, p3, p4⟩ where a, b, c, d, e, f, g are the original 7-bits of the message, and p1, p2, p3, p4 are 4 parity bits. Recall the two properties from Tutorial 2: (0) each bit of the original message appears in at least two parity bits, and(1) no two bits of the original message appear in exactly the same set of parity bits. For the following proposed parity bits, select whether they satisfy property (0), property (1), both, or neither. p1 = a ⊕ d ⊕ ep2 = a ⊕ b ⊕ e ⊕ fp3 = b ⊕ c ⊕ f ⊕ gp4 = c ⊕ d ⊕ g Question 1 options: a neither property b both properties c only property (0) d only property (1)arrow_forwardSuppose Alice and Bob are going to communicate using AES in CBC mode. Unfortunately Alice's message length (in bytes) is not a multiple of 16. Suppose the last block of her message is just a single zero byte. How can she pad out the last block so that she can use CBC mode? Since this needs to be a reversible operation, how does Bob recognize the padding and remove it?arrow_forwardInternet Checksum. Consider the six sixteen bit numbers: 10110101 01000110 01001001 01101011 10110100 01000110 01001001 01101101 10110101 01010110 01011010 01101111 Compute the Internet Checksum field value of these six words (each word has sixteen bits) Enter the 2 bytes each as an 8-bit number with only O's and 1's, and make a single blank space between the two 8-bit numbers (e.g., 01010101 00101000). [Note: you must use bitwise XOR logic function and don't use 2's or 1's complement] Not quite. This answer is incorrect.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education