
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Q1
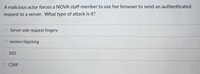
Transcribed Image Text:A malicious actor forces a NOVA staff member to use her browser to send an authenticated
request to a server. What type of attack is it?
Server side request forgery
O session hijacking
O XSS
O CSRF
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Perform the following conversions. You must show how you computed your answer.arrow_forward5. How many 6-character license plates are possible if the first character must be a letter that is not equal to O, and the last character must be a digit that is not equal to 0?arrow_forwardHow many integers in the range 11 through 100100 (inclusive) are multiples of 22 or 55?arrow_forward
- Question 5: Fill up the below tables with relevant converted numbers between decimal, binary, and hexa- decimal numbers. Binary Numbers Hexa-decimal Numbers Decimal Numbers 110102 1E16 9910arrow_forward11. Solve: 100101011 -1000101 01arrow_forwardHow should we compare floating point numbers for equality? Why?arrow_forward
- I'm not sure how to make a table showing hexadecimal numbers between 0X00 and 0X20 and their binary equivalants. Thanks for your help.arrow_forwardWhich answer for this code segment?arrow_forwardGiven the following maxheap, show the 3rd number in the list after the 2nd pop: 49, 43, 41, 23, 33, 19, 36, 7, 22, 17, 21, 13, 12, 31, 32arrow_forward
- What is the coefficient of the term x³y in the binomial expansion (x + y)¹4 ? Enter your answer in the box below. Answer =arrow_forwardcmpare between a=101001 and b=100110 to determine if they are equal or notarrow_forwardPlease provide the solution of the question in js and with OPPs concepts and with explanationarrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY