
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
I need help with a clear explanation, please
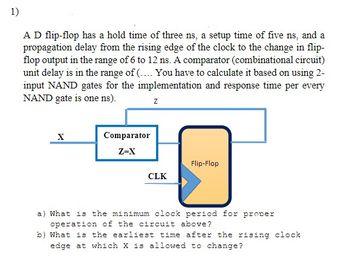
Transcribed Image Text:1)
A D flip-flop has a hold time of three ns, a setup time of five ns, and a
propagation delay from the rising edge of the clock to the change in flip-
flop output in the range of 6 to 12 ns. A comparator (combinational circuit)
unit delay is in the range of (.... You have to calculate it based on using 2-
input NAND gates for the implementation and response time per every
NAND gate is one ns).
X
Z
Comparator
Z-X
20
Flip-Flop
CLK
a) What is the minimum clock period for prover
operation of the circuit above?
b) What is the earliest time after the rising clock
edge at which X is allowed to change?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 4 steps with 3 images

Knowledge Booster
Similar questions
- Give an in-depth comparison and contrast of any two modes of communication and your reasoning for choosing one over the other. Give reasons to back up your response.arrow_forwardWhen you talk about the desired outcome of the authentication procedure, what do you mean? What are the pros and cons of using various authentication techniques?arrow_forwardIt would be quite helpful if you could elaborate on the logic behind the authentication procedure. Thank you very much for your time. Analyze the different methods of authentication and compare and contrast their positive and negative aspects.arrow_forward
- Do you think it is possible for you to explain why authentication is such a challenge in the contemporary era of information?arrow_forwardHow does secret key cryptography work in practice? Please provide a short explanation, such as how it has worked in the past, with your submission. Do you have any input on its current status?arrow_forwardHow much of the TCSEC orange book do you agree with, and how much do you disagree with?arrow_forward
- I'd be very grateful if you could elaborate on the goals of the authentication process. Think about the benefits and drawbacks of the various authentication methods now in use.arrow_forwardIt would be very appreciated if you could elaborate on the function of the authentication procedure. Discuss the pros and cons of each authentication method.arrow_forwardCan you provide any light on why authentication is a challenge in the modern era of information?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY