
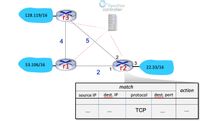
4.05-2. Generalized forwarding: specifying a flow table entry (b). Consider the three-node network below, that uses flow-based generalized forwarding (e.g., as in OpenFlow) in the network's routers. In the question below, we'll want to create match+action entries in the flow table at router r2, with three ports labelled 1,2,3 (in black). In the question, matches are constrained to be over only four fields: the IP source address, the IP destination address, the upper-layer protocol field of the IP datagram, and the destination port number of the transport-layer segment. The actions are either to drop or to forward(i), that is, to forward a matching packet on port i. The default action (unless stated otherwise) is that if a packet doesn't match a rule, it will be dropped.
![(b) Suppose we want to implement the following behavior, and that the default configuration is that all traffic from 22.33/16 should be allowed to be forwarded by r2 to the outside
network. However, we also want to implement a higher priority rule (which would be earlier in the table, for example) so that users within the 22.33/16 network are never allowed to
connect to an external web server on port 80. Specify the flow table row entries to implement this rule, by indicating the column entries below. The * is a wildcard match, which
matches everything - you should use * over more specific answers whenever possible.
[Note: You can find more examples of problems similar to this here.]
C. v In the "source IP" column, the flow table entry should be:
A. v In the "dest. IP" column, the flow table entry should be:
D. v In the "dest port" column, the flow table entry should be:
F. V In the "action" column, the flow table entry should be:
A. 128.119/16
B. forward(1)
C. 22.33/16
D. 80
E. UDP
F. drop
G. forward(2)
H. 53.106/16
I.](https://content.bartleby.com/qna-images/question/12b43c3a-c8f9-454d-b9eb-12cb57f3d976/80b68f47-dc6d-4f2f-a45c-45e6e5e5c256/ki0zum_thumbnail.jpeg)
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

- You're working on a procedure that will connect a node to a doubly connected set. The machine in which this operation will be run is prone to hardware faults on a regular basis. The list that your software must keep is extremely important. As if the computer crashes in the midst of performing the process, the software must maintain the list's accuracy. Provide the actual statements you'll need to update the list in your protocol. (There should be no more than a dozen statements on the list.) After each command, explain the impact of a system malfunction. Describe how you can change this protocol to recover the simple list's credibility in the event of a system breakdown.arrow_forward2. Recall the concept of Physically Unclonable Functions, which are an importantcomponent of hardware based security. Here is a simple scenario and simple protocol usingPUFs for authenticating a tag. In the protocol below, the Reader stores ALL possiblecombinations of Challenge-Response pairs for every tag it needs to authenticate. Duringauthentication, the Reader broadcasts the ID of the tag, and a greeting (Gn ). Every tag maysee this message, but only the one with the right ID will process the message. The right tagwith the ID in the message will then feed the greeting to its PUF and compute the responseSn. The response is then sent to the Reader. This should be clear from the Figure below. Forthe next round of authenticating the same Tag, the process repeats with a new Greeting(G n+1 ). Since the Reader has the responses, authentication is straightforward. Recall thatChallenges and Responses are typically 128 or 256 bit strings for RFIDs.From the protocol, and class, it should be…arrow_forwardCan anyone help me with basic client-server interaction using TCP sockets in network programming in c code that includes csapp.c and csapp.h. and a text file of the student record that include first name, last name, age, major, and graducation year. The ideas is have 4 choice: Add record, Search Age Range, Search graducation year, and Terminate. In opition 1, it should collect all the data to the text file, in opition 2, it should search for age range from the text file. in opition 3, it should search the graducation year from the text file and if the year is not there it should print record not found. And opition 4, the client should close the connection and terminate. studentRecord.txt: John,Doe,24,Computer Science,2023Jane,Doe,22,Mechanical Engineering,2020Charles,Babbage,21,Math,2022George,Bool,25,Math,2023Marie,Curie,26,Chemistry,2023 I know this isn't enough but I want to understand about the client-server interaction using socket interface. So please try to make it simple…arrow_forward
- Make a map → from source to destination there are many routes that can be taken within the map. Connect the 5 routers → name it A (has 3 connections), B (has 2 connections), C (has 2 connections), D (has 2 connections), and E (has 1 connection). IP addressing: LAN A1 A2 A3 B1 B2 C1 C2 D1 D2 E1 Network Address 192.168.1.0 192.168.2.0 192.168.3.0 192.168.10.0 192.168.11.0 192.168.20.0 192.168.21.0 192.168.32.0 192.168.33.0 192.168.40.0 Subnet Mask /24arrow_forwardC PROGRAMMING you are to write a TCP/IP server that can build up a graph of a network ofnetworks (using the supplied graph library and implementation of Dijkstra’s algorithm) and thenquery that graph to find out which link between two networks should be used as the next hop tosend a packet of data from one network to another within the network of networks (using thesupplied implementation of Dijkstra’s algorithm). using the following program as a start point: /* * NetworkServer.c * ProgrammingPortfolio Skeleton * */ /* You will need to include these header files to be able to implement the TCP/IP functions */#include <stdio.h>#include <stdlib.h>#include <string.h>#include <sys/types.h>#include <netinet/in.h>#include <netdb.h>#include <fcntl.h>#include <unistd.h>#include <errno.h>#include <sys/socket.h> /* You will also need to add #include for your graph library header files */ int main(int argc, const char * argv[]){ int…arrow_forwardCan someone please help me with this? I'll give a thumb up to thank for your time.As I'm reviewing for my upcoming exam, I really need an answer from an expert in the field. Please do not send me an answer from chatGPT. I've got enough of that, so please be helpful.arrow_forward
- I am trying to execute the backward pass for a convolution network with layers (2 layer conv, relu, max pooling and linear, then softmax loss calculation). I have a hard time to retrieve x, y and probs at backward pass, the code does not recognize them as attributes. Please fix my code and show codes and output. Thank you from .softmax_ce import SoftmaxCrossEntropyfrom .relu import ReLUfrom .max_pool import MaxPoolingfrom .convolution import Conv2Dfrom .linear import Linear class ConvNet: """ Max Pooling of input """ def __init__(self, modules, criterion): self.modules = [] for m in modules: if m['type'] == 'Conv2D': self.modules.append( Conv2D(m['in_channels'], m['out_channels'], m['kernel_size'], m['stride'], m['padding']) ) elif m['type'] == 'ReLU': self.modules.append(…arrow_forwardDemonstrate that two red nodes in a route cannot be contiguous (e.g., parent and child). As a result, no more than half of the nodes in a path may be red.arrow_forwardAfter how many time ticks, will L's distance vector (i.e., its DV that it exchanges with its neighbor) reflect this change in topology?arrow_forward
- Consider a network with a maximum flow and an arriving arc-free node other than the source node. Is it feasible to delete this node without affecting the maximum flow value in any way? Is it also feasible to delete a node that is not the sink node without generating an arc?arrow_forwardAttached is image of the problem. Make sure to answer all parts of the problem correctly.arrow_forwardRecall the concept of Physically Unclonable Functions, which are an importantcomponent of hardware based security. Here is a simple scenario and simple protocol usingPUFs for authenticating a tag. In the protocol below, the Reader stores ALL possiblecombinations of Challenge-Response pairs for every tag it needs to authenticate. Duringauthentication, the Reader broadcasts the ID of the tag, and a greeting (Gn ). Every tag maysee this message, but only the one with the right ID will process the message. The right tagwith the ID in the message will then feed the greeting to its PUF and compute the responseSn. The response is then sent to the Reader. This should be clear from the Figure below. Forthe next round of authenticating the same Tag, the process repeats with a new Greeting(G n+1 ). Since the Reader has the responses, authentication is straightforward. Recall thatChallenges and Responses are typically 128 or 256 bit strings for RFIDs.From the protocol, and class, it should be…arrow_forward
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY





