Question
Alert dont submit AI generated answer.
Transcribed Image Text:lestions about cryptography
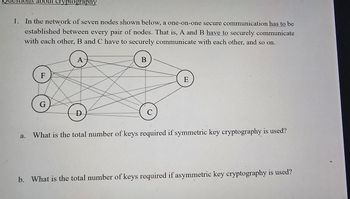
1. In the network of seven nodes shown below, a one-on-one secure communication has to be
established between every pair of nodes. That is, A and B have to securely communicate
with each other, B and C have to securely communicate with each other, and so on.
F
G
A
D
B
C
E
a. What is the total number of keys required if symmetric key cryptography is used?
b. What is the total number of keys required if asymmetric key cryptography is used?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 4 steps

Knowledge Booster
Similar questions
- Match the Security Controls to the following (see attached photo) Unsupervised Lab Office Data Center Employee Latop You can only use the security controls once.arrow_forwardDescribe each stage of the hacking procedure.arrow_forwardWhat is the best way to track the information requests?arrow_forward
- 1. How do you present feature creep? (Maximum 2 pages)arrow_forwardPlease refer to the attachment for the sceniro. Please answer the following question - paragraph on A clear description of the identity threats pertinent when using a SaaS solution.arrow_forwardWhen using lot products, companies must manage risks related to the 5Vs of big data. Choose the best definition of Volume from the list below. High speed of accumulation of data Different formats of data from various sources O Huge amounts of data Extract useful dataarrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios