
( C
1. Red String
by CodeChum Admin
For the Japanese, who know so much and intuit more, human relations are predestined by a red string that the gods tie to the pinky fingers of those who find each other in life. Legend has it that the two people connected by this thread will have an important story, regardless of the time, place or circumstances. The red string might get tangled, contracted or stretched, as surely often happens, but it can never break.
A red string is basically like a connection. And in programming, a connection from one variable to another can be simulated by a pointer. Let's do that!
Instructions:
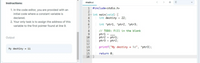
In the code editor, you are provided with an initial code where a constant variable is declared.
Your only task is to assign the address of this variable to the first pointer found at line 9.
Output
My·destiny·=·11
Step by stepSolved in 2 steps with 2 images

- Explain what you've learned about the GOTO tale and spaghetti code from the Structured Programming Theorem in an essay that meets the requirements for length and level of information.arrow_forwardIn no more than 250 words, describe the idea of polymorphism and how it relates to software.arrow_forward(d) true / false Prolog first creates the search space, and then searches it.arrow_forward
- OZ PROGRAMMING LANGUAGE Exercise 1. (Efficient Recurrence Relations Calculation) At slide 54 of Lecture 10, we have seen aconcurrent implementation of classical Fibonacci recurrence. This is: fun {Fib X} if X==0 then 0 elseif X==1 then 1 else thread {Fib X-1} end + {Fib X-2} end end By calling Fib for actual parameter value 6, we get the following execution containing several calls ofthe same actual parameters.For example, F3, that stands for {Fib 3}, is calculated independently three times (although it providesthe same value every time). Write an efficient Oz implementation that is doing a function call for a givenactual parameter only once.Consider a more general recurrence relation, e.g.:F0, F1, ..., Fm-1 are known as initial values.Fn = g(Fn-1, ..., Fn-m), for any n ≥ m.For example, Fibonacci recurrence has m=2, g(x, y) = x+y, F0=F1=1arrow_forwarddocs. قسم علوم الحاسوب- المرحلة الأولى -امتحان مادة ال مطلوب Let U={a,b,c,d,e,f,g), A={a,b.c,d,e}, B={a,b,c,f} C={a,e,f,d,g): find ill Jgull *? complement of (B-A) * ?A*(B NC) 3 3 ae Google c - L TIkrit Universityarrow_forwardIn no more than 250 words, describe the idea of polymorphism and how it relates to software.arrow_forward
- See belowarrow_forwardA pistol-wielding robber approached a Quaker on a rural road. "Your money or your life!" shouted the thief. "Exchange is allowed, and I will offer thee my purse for the weapon," my buddy said. The thief accepted the handbag, then the quaker held the pistol to his head and said, "Now friend, give me back my pocketbook or the weapon may go off fire," according to the robber.arrow_forwardIn no more than 250 words, describe the idea of polymorphism and how it relates to software.arrow_forward
- Just what does it mean to talk about "separable programming," and how does it work?arrow_forwardPostfix interpreter def postfix_evaluate(items): When arithmetic expressions are given in the familiar infix notation 2 + 3 * 4, we need to use parentheses to force a different evaluation order than the usual PEMDAS order determined by precedence and associativity. Writing arithmetic expressions in postfix notation (also known as Reverse Polish Notation) may look strange to us humans accustomed to the conventional infix notation, but is computationally far easier to handle, since postfix notation allows any evaluation order to be expressed unambiguously without using any parentheses at all! A postfix expression is given as a list of items that can be either individual integers or one of the strings '+','- and '/' for the four possible arithmetic operators. To evaluate a postfix expression using a simple linear loop, use a list as a stack that is initially empty. Loop through the items one by one, in order from left to right. Whenever the current item is an integer, just append it to…arrow_forwardIt would be great to have an example of the notion of coding rules in order to better grasp it.arrow_forward
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY





