
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
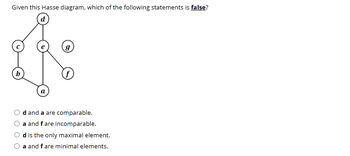
Transcribed Image Text:Given this Hasse diagram, which of the following statements is false?
d
b
g
d and a are comparable.
a and f are incomparable.
d is the only maximal element.
a and f are minimal elements.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Stuck need help! The class I'm taking is computer science discrete structures. Problem is attached. please view attachment before answering. Really struggling with this concept. Thank you so much.arrow_forwardEvery group G = {A, B, C, ... } obeys the same set of rules. We didn’t really make use of one of them—that multiplication of the elements is associative, (AB)C = A(BC)—but did discuss and use the other(s). Select it (or them) from the list below: 1. G must include the identity, E.2. The number of elements in G must be finite.3.. The product of any two elements (C = AB) must be in G.4. The inverse of every element (A−1A = AA−1= E) must be in G.arrow_forwardI want an answer for a begainer on Netbeansarrow_forward
- Discuss the repetition constructs. Give an illustrative example for each one of them.arrow_forwardUsing C++ Please add the specific explanation. Thanks. Huffman coding is used to compress data. The idea is straightforward: represent more commonlonger strings with shorter ones via a basic translation matrix. The translation matrix is easilycomputed from the data itself by counting and sorting by frequency.For example, in a well-known corpus used in Natural Language Processing called the "Brown"corpus (see nltk.org), the top-20 most frequent tokens, which are words or punctuation marksare listed below associated with frequency and code. The word "and" for example requireswriting three characters. However, if I encoded it differently, say, using the word "5" (yes, Icalled "5" a word on purpose), then I save having to write two extra characters! Note, the word"and" is so frequent, I save those two extra characters many times over!Token Frequency Codethe 62713 1, 58334 2. 49346 3of 36080 4and 27932 5to 25732 6a 21881 7in 19536 8that 10237 9is 10011 10was 9777 11for 8841 12`` 8837 13''…arrow_forwardWrite a procedure called STRUCTURE-TO-MATRIX that takes an adjacency structure as its only parameter, and returns an equivalent adjacency matrix. Assume there is a procedure MAKE-MATRIX(m, n) that returns an m × n integer matrix, where m ≥ 0 and n ≥ 0. The integers in this matrix are undefined.arrow_forward
- PLEASE help with part A,B, AND C(which is like part c and d because theres two parts to C)! Please if possible, give an explanation along with the solution so I can understand why the answer is what it is.arrow_forwardC PROGRAMMING Implement dijkstras alorithm Check that the Graph graph, and starting node, id, are valid• Create the set S containing all the networks (vertices) except the source node (you might wantto use an array for this.• Create an array to represent the table D and initialise it with the weights of the edges from thesource node, or infinity if no edge exists. You should use the constant DBL_MAX to representinfinity.• Create an array to represent the table R and initialise it with the next hops if an edge existsfrom the source, or 0 otherwise.• Then repeatedly follow the remaining rules of Dijkstra’s algorithm, updating the values in D andR until S is empty.• Each of the values required to complete the above can be found by calling the variousfunctions (get_vertices(), get_edge(), edge_destination(), edge_weight(), etc.)in the supplied graph library.• Once Dijkstra’s algorithm has run, you will need to create the routing table to be returned byallocating enough memory for the…arrow_forward(a) Give a regular expression that describes all strings accepted by the automaton. (b) Use a subset construction to construct DFA that accepts the same language. Clearly specify the transition table and the start and accepting states. (c) Explain concisely how you can use reachability in the graph to reduce the number of states as much as possible. You might need to draw the unreduced DFA first (for yourself, no need to submit) to better see what is going on. How many states do you end up with? Draw the resulting DFA (with the reduced number of states).arrow_forward
- 1) why is it a good idea to separate the first (entry) node from any looping nodes? and (2) why is it a good idea to have JUST ONE alternative direction, given an operation? [For instance if X < Y we go from node 3 to node 4 ONLY and no other node]. And, (3) Is there a better way to do all of this? A better way to represent logic flow than these types of diagrams (either the manual ones like we used in chapter 6 or the ones we saw from the Node Generator for instance)???arrow_forwardIf f:A->B and g:B->C, does there exist a function h:B->A such that f•k=g (composition)?arrow_forwardI need a reference page for this question that was answered below. What is the difference between a singly-linked list and a doubly-linked list? In what situation would you use a singly-linked list over a doubly-linked list? In what situation would you use a doubly-linked list over a singly-linked list? If a node is in a linked list with N nodes, how many nodes will be traversed during a search for the node? Explain the best- and worst-case search scenarios. Explain why a singly-linked list defines a RemoveAfter() function, while a doubly-linked list defines a Remove() function. Could a RemoveAfter() function also be defined for a doubly-linked list? Explain why or why not. Could a Remove() function also be defined for a singly-linked list? Explain why or why not.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education