
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
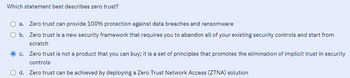
Transcribed Image Text:Which statement best describes zero trust?
a. Zero trust can provide 100% protection against data breaches and ransomware
O b.
Zero trust is a new security framework that requires you to abandon all of your existing security controls and start from
scratch
c. Zero trust is not a product that you can buy; it is a set of principles that promotes the elimination of implicit trust in security
controls
d. Zero trust can be achieved by deploying a Zero Trust Network Access (ZTNA) solution
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Regarding familiarity with operating systems, what benefits does understanding assembly language provide?arrow_forwardMultifactor authentication (MFA) is considered an important security control for what purpose? a. MFA identifies a cyberattack before it can cause damage O b. MFA distinguishes a known device from an unknown device O c. MFA provides an extra level of identity assurance (that is, validates users are who they claim to be) O d. MFA establishes internal network controlsarrow_forwardHow can organizations implement Zero Trust security effectively?arrow_forward
- The essential characteristics of the a.NET security standards are outlined. You may begin your investigation with credible sites such as the OWASP GitHub page, the Microsoft.NET security website, or any other credible site.arrow_forward1. What is the difference between a threat agent and a threat? 2. What is the difference between vulnerability and exposure? 3. How is infrastructure protection (assuring the security of utility services) related to information security? 4. What type of security was dominant in the early years of computing? 5. What are the three components of the C.I.A. triangle? What are they used for? 6. If the C.I.A. triangle is incomplete, why is it so commonly used in security? 7. Describe the critical characteristics of information. How are they used in the study of computer security? 8. Identify the six components of an information system. Which are most directly affected by the study of computer security? 9. Why is the top-down approach to information security superior to the bottom-up approach? 10. Which members of an organization are involved in the security system development life cycle? Who leads the process?arrow_forwardExplain what Primary CIS Control was violated and why the control is critical A company has deployed a next generation antivirus (NGAV) solution on all of its workstations and servers, and they still got hit with a ransomware attack. It was discovered that the NGAV software did not have all the features and capabilities that more advanced solutions possess. Does this violated control CIS Control #7 Continuous Vulnerability Management?arrow_forward
- Explore the concept of zero-trust networking and its potential benefits for security and network performance.arrow_forwardWhat are use case diagrams used for? Explain a scenario of a computerized email authorization system using a case diagram. Explain every symbol you have used to design the systemarrow_forwardSelect two non-consecutive chapters, other than Chapter 1) that specify a social engineering attack from Kevin Mitnick's book The Art of Deception and discuss why the exploit worked and what the victims should have done differently (risk mitigation or defense strategies) to mitigate the loss. Compare the different exploits used in the two chapters. Why was each exploit chosen for that specific situation? Be sure to list the chapter numbers you are using.arrow_forward
- The stakeholders of a software company have four new security requirements that they are considering including in the next release of their flagship product: Two-factor authentication (2FA), Captcha for Bot Detection (CBT), Password Expirations (PEX), and Role-base access control (RBA). Given the time constraints, they may not be able to include all, so they need to prioritize these requirements based on three criteria: Maintainability (MA), Ease of Use (EU), and Integration Support (IS). They have the following pairwise preferences of the criteria: Maintainability is three times as important as Ease of Use Ease of Use is two times as important as Integration Support Maintainability is five times as important as Integration Support Based on the above information, do the following: Make a matrix capturing all pairwise comparisons of importance of criteria.arrow_forwardOne of the most basic concepts in the field of Information Security is the CIA Triad or CIA Triangle. This was mentioned briefly in Chapter 1 of your text. CIA stands for Confidentiality, Integrity, and Availability. Denial of Service (DoS) attacks challenge the "Availability" of a system or data. This could be temporary (e.g., a SYN Flood Attack that renders a web server unavailable during the attack) or permanent (e.g., the deletion or destruction of the data). The latter of these has become increasingly common in the case of "ransomware" which is malware that encrypts all of the data on an infected system and the administrator is notified that if they don't pay a ransom by a certain date that the key to decrypt the data will be permanently deleted. (NOTE: This is conspicuously absent from the books discussion on malware but is a MAJOR issue right now.) While the temporary attacks may be less destructive, they are often done against systems that generate a lot of money (such…arrow_forwardWhich publication by the National Institute of Standards and Technology (NIST) outlines the concepts for zero trust and a roadmap to achieve it, and proposes a zero trust architecture? a. NIST CSF b. NIST 800-53 c. NIST 800-207 d. NIST SP 1900-206arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education