
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
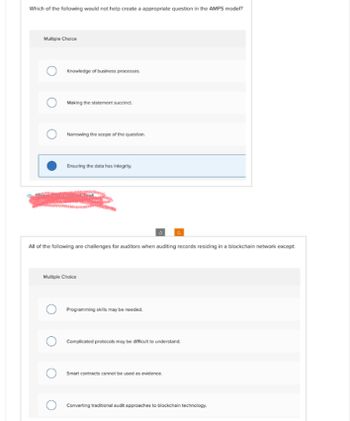
Transcribed Image Text:Which of the following would not help create a appropriate question in the AMPS model?
Multiple Choice
Knowledge of business processes.
Making the statement succinct.
Narrowing the scope of the question.
Ensuring the data has integrity.
All of the following are challenges for auditors when auditing records residing in a blockchain network except:
Multiple Choice
Programming skills may be needed.
Complicated protocols may be difficult to understand.
Smart contracts cannot be used as evidence.
O Converting traditional audit approaches to blockchain technology.
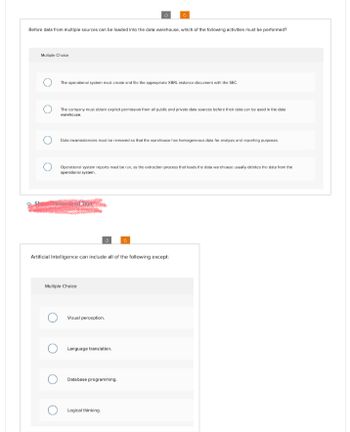
Transcribed Image Text:Before data from multiple sources can be loaded into the data warehouse, which of the following activities must be performed?
Multiple Choice
The operational system must create and file the appropriate XBRL instance document with the SEC.
The company must obtain explicit permission from all public and private data sources before their data can be used in the data
warehouse.
Data inconsistencies must be removed so that the warehouse has homogeneous data for analysis and reporting purposes.
Operational system reports must be run, as the extraction process that loads the data warehouse usually deletes the data from the
operational system.
Artificial Intelligence can include all of the following except:
Multiple Choice
Visual perception.
Language translation.
Database programming.
Logical thinking.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 6 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Explore the concept of "file carving techniques" in data recovery and digital forensics and their applications.arrow_forwardThe databases were inaccessible due to a lock. The utilization of keys serves as a means of ensuring security in both commercial and residential settings. Simultaneous transactions are not allowed. Digital security can be enhanced through the use of passwords. It is imperative to maintain consistency.arrow_forwardDiscuss the principles of secure coding practices in software development. How can developers prevent common security vulnerabilities such as SQL injection and cross-site scripting (XSS)?arrow_forward
- Numerous well-known organizations' database systems have reportedly been infiltrated, causing the loss of client data. Describe how you may be able to enhance the database's security measures.arrow_forwardIn the article, “Google search test shows no progress in cyber safety: a year after breaches exposed, UKFast director reveals that unsecure databases still likely to pose biggest cyber threat to SME security,” database security is revealed as the most fundamental part of creating a database, and it is vital to protecting a company’s information assets from unauthorized access. In fact, SQL injections have surpassed almost all other security vulnerabilities in 2013. Although security policies are often implemented to protect data, information security remains every employee’s responsibility. Data in the wrong hands can have a major negative impact on a business, and security of the data ultimately falls on the creator of the database. In this discussion board post, discuss the concept of database security as it relates to the Bible. What mandates does God give us with respect to protection of property? What real world examples support these biblical truths?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education