
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
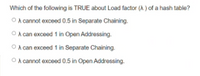
Transcribed Image Text:Which of the following is TRUE about Load factor (A ) of a hash table?
O A cannot exceed 0.5 in Separate Chaining.
O A can exceed 1 in Open Addressing.
O A can exceed 1 in Separate Chaining.
O A cannot exceed 0.5 in Open Addressing.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- explain each code line. all the details.arrow_forwardI am having a hard time finding the right approach for the question. I need a justified answer. Could you please help me through?arrow_forwardTask - 1: Write a java program to implement the following algorithms for Open Addressing techniques for Hash Table data structure. (Use a simple array of integers to store integer key values only). HASH-SEARCH(T, k) HASH-INSERT (T, k) i = 0 repeat j = h (k, i) if T[j] == NIL T[j] = k return j else i = i + 1 ● i = 0 repeat until i == m error “hash table overflow" For both algorithms, to compute the index j, write the following methods: getLinear ProbIndex (key, i) getQuadraticProbIndex ● get DoubleHash (key, i) (key, i) j = h (k, i) if T[j] == k return j i = i + 1 until T[j] == NIL or i = m return NIL Linear Probing index is computed using following hash function: h(k, i) = (h₁(k) + i) mod m h₁(k)= k mod m Quadratic probing index is computed using following hash function: h(k, i) = (h₁(k) + i²) mod m h₁(k)= k mod m Double hashing index is computed using following hash function: h(k, i) = (h₁(k) + i h₂(k)) mod m h₁(k)= k mod m h₂(k) = 1 + (k mod m - 1)arrow_forward
- This quesiton are for another page I will linked them.arrow_forwardAllocation Мах Available АВCD АВСD АВСD То T1 T2 T3 0012 0012 1520 1000 1750 1354 2356 0632 0014 0652 0656 Answer the following questions using the banker's algorithm: a. What is the content of the matrix Need? b. Is the system in a safe state? c. If a request from thread T1 arrives for (0,4,2,0), can the request be granted immediately? 2)arrow_forwardI am using a proof of work protocol with a 8-bit hash function. In other words, the digest is always 8-bits. The difficulty I have set for this proof of work protocol is 6. In binary, which of the following hash digests would satisfy this proof of work protocol? In other words, as you are searching for a response string, what would be an example of a hash output that would make you stop? 11111010 01000101 11000000 00000011 11111100 01111111 10101001arrow_forward
- Question 15arrow_forward6. 10 11 12 13 14 15 16 17 18 19 20 21 22 23| 24 | 25 26 27 28 || 29 || 30 31 32 33 34 35 36 37 Maving to the next question prevents changes to this answer. Quèstion 9 A hash table of length 10 uses open addressing with hash function h(k)-k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below 2. 42 23 4 34 52 9. 46 7. 33 8. 6. Which one of the following choices gives a possible order in which the key values could have been inserted in the table? OA 46, 42, 34, 52, 23, 33 OB. 34, 42, 23, 52, 33, 46 OC 46, 34, 42, 23, 52, 33 OD.42, 46, 33, 23, 34, 52 1947117.htm Failed - Forbiddenarrow_forwardConsider the following scenario: M A table is sorted on indexed column and has 20,000,000 rows. C . Each row is 300 bytes. Table and index blocks are 4 kilobytes. Assume 1 kilobyte is approximately 1,000 bytes. Assuming the index is sparse, how many entries are in the index? 000,000,000 entries 1 Check hp 2 Try again 4 5arrow_forward
- Consider a hash table of capacity 5 that uses open addressing with linear probing. This hash table uses a hash function that takes the remainder when the hash code of a string is divided by the capacity of the hash table. (For example, "air" hashes 0.) The hashCode method has been overridden for strings, which simply returns 0 if a string begins with 'a', 1 if it begins with 'b', etc. /** Returns 0 if a String begins with 'a', 1 if it begins with 'b', etc. */ public int hashCode() { return this.charAt(0) - 'a'; } Assume that "apple", and "butter" have been inserted in this order into the hash table. "fig" is to be inserted into the hash table. (a) Which array slot/index should "fig" be placed? Answer: (b) What is the load factor after "fig" is inserted into the hash table? Answer:arrow_forwardWhat is the total number of linked lists included in an interleaving routing table of dimension T? Which kind of primitive data structure is used in the Separate Recursive hash table?arrow_forwardHow many collisions would you expect to find in the following cases? a. Your hash function generates a 12-bit output and you hash 1024 randomly selected messages. b. Your hash function generates an n-bit output and you hash m randomly selected messages.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education