
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
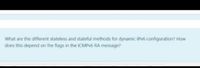
Transcribed Image Text:What are the different stateless and stateful methods for dynamic IPV6 configuration? How
does this depend on the flags in the ICMPV6 RA message?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- In order to implement a DNS amplification attack, the attacker must trigger the creation of a sufficiently large volume of DNS response packets from the intermediary to exceed the capacity of the link to the target organization. Consider an attack where the DNS response packets are 500 bytes in size (ignoring framing overhead). a. How many of these packets per second must the attacker trigger to flood a target organization using a 30-Mbps link? A 100-Mbps link? Or a 1-Gbps link? b. If the DNS request packet to the intermediary is 60 bytes in size, how much bandwidth does the attacker consume to send the necessary rate of DNS request packets for each of these three cases?arrow_forwardThe following protocol: 1. A – B: {|{K}K,6B|}KprA 2. В - А: {M}K provides perfect forward secrecy with respect to which of the following secret keys: 1- Kpre 2- Kpra 3- Kora and Kore 4- K 5- None Select one: о 1. Крв O 2. Kara O 3. Kara and KprB О 4. К O 5. Nonearrow_forwardIn the event that a web client needs access to protected web server resources, you should demonstrate how to implement native authentication and authorization services. Which two factors enable the implementation of layered protocols a viable option? It would be helpful if you provided concrete examples to back up your statements.arrow_forward
- Three-way handshake is used by a TCP client and a TCP server to establish a connection, as illustrated below: 1st: client:port1 -> server:port2, SYN 2nd: server:port2 -> client:port1, SYNACK 3rd: client:port1 -> server:port2, ACK When this client is performing scanning attacks, it will generated a large number of failed connections. In each failed connection, the three-way handshake fails to complete. People commonly use SYN together with the absence of its corresponding SYNACK in this same TCP session to identify whether this connection is failed. By investigating the failed connections, an engineer finds that in legitimate/benign cases, if the server does not return SYNACK to the client, the client will not send the ACK packet after SYNACK (e.g., the 3rd packet above). Therefore, this engineer suggests that we can count the failed connections based on the following rules without considering SYNACK:arrow_forwardQuestion P .Full explain this question and text typing work only We should answer our question within 2 hours takes more time then we will reduce Rating Dont ignore this linearrow_forwardIn HTTP version 1.0, a server marked the end of a transfer by closing the connection. Explain why, in terms of the TCP layer, this was a problem for servers. Find out how HTTP version 1.1 avoids this. How might a general-purpose request/reply protocol address this?arrow_forward
- I was wondering if you could highlight the key differences between TCP session hijacking and UPD session hijacking.arrow_forwardPlease just give a brief explanation about these cybersecurity questions.( Not more than three sentences).arrow_forwardThree-way handshake is used by a TCP client and a TCP server to establish a connection, as illustrated below: 1st: client:port1 -> server:port2, SYN 2nd: server:port2 -> client:port1, SYNACK 3rd: client:port1 -> server:port2, ACK When this client is performing scanning attacks, it will generated a large number of failed connections. In each failed connection, the three-way handshake fails to complete. People commonly use SYN together with the absence of its corresponding SYNACK in this same TCP session to identify whether this connection is failed. By investigating the failed connections, an engineer finds that in legitimate/benign cases, if the server does not return SYNACK to the client, the client will not send the ACK packet after SYNACK (e.g., the 3rd packet above). Therefore, this engineer suggests that we can count the failed connections based on the following rules without considering SYNACK: If a client:port1 sends…arrow_forward
- Why is the 'Host' property included in the communication that is outlined by the HTTP1.1 protocol standard if it doesn't serve any purpose? Why is it that this cannot be determined from the L3 IP address in its present state?arrow_forwardWhen a web client requests access to a web server's protected resources, show how native authentication and authorization services are used. To solve this problem, it is easiest to look at the following two justifications for layered protocols: Please provide concrete examples to support your arguments.arrow_forwardWe explore whether either UDP or TCP offers any level of end-point authentication in this problem. a. Consider a server that accepts a request via UDP and responds via UDP (for example, as done by a DNS server). Where would the server give its answer if a client with IP address X spoofs it with address Y? b. Assume a server receives a SYN with IP source address Y and responds with SYNACK. The server then receives an ACK with IP source address Y and the right acknowledgmentamount. Assuming the server selects a random initial sequence number and there is no "man-in-the-middle," how can the server be confident that the recipient is really at Y (and not at any other address X that spoofs Y)?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education