Question
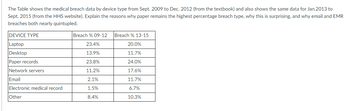
Transcribed Image Text:The Table shows the medical breach data by device type from Sept. 2009 to Dec. 2012 (from the textbook) and also shows the same data for Jan.2013 to
Sept. 2015 (from the HHS website). Explain the reasons why paper remains the highest percentage breach type, why this is surprising, and why email and EMR
breaches both nearly quintupled.
DEVICE TYPE
Laptop
Desktop
Paper records
Network servers
Email
Electronic medical record
Other
Breach % 09-12
23.4%
13.9%
23.8%
11.2%
2.1%
1.5%
8.4%
Breach % 13-15
20.0%
11.7%
24.0%
17.6%
11.7%
6.7%
10.3%
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- Which objectives does authentication seek to accomplish? Methods of verification are assessed with regard to their benefits and drawbacks.arrow_forwardExplain the distinctions between public-key and private-key encryption. Include examples of when and why each could be utilized in your response.arrow_forwardWhat is computer crime and computer related crime and its example? (Please use 2 official journal as references)arrow_forward
- How does authentication serve a particular purpose? What are the benefits and drawbacks of various authentication methods?arrow_forwardHow can MD5-signed certificates be secured?arrow_forwardData security—what's most important? Data integrity and user authentication breached, which security method?arrow_forward
- What similarities and differences exist between authentication and authorization? What, if any, connection do they have?arrow_forwardSpecify the dangers associated with each authentication method and provide a remedy.arrow_forwardWhat are some authentication goals? Examine the pros and downsides of each authentication method.arrow_forward
- What exactly does it mean when someone says they are going to assault you with a poison package, and what does it imply? Please provide two examples of this kind of violent attack.arrow_forwardWhen certificates are signed using the MD5 method, what security concerns arise, and how may they be avoided?arrow_forwardWhat are the hazards associated with signing certificates using the MD5 algorithm?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios