
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
Transcribed Image Text:Question Completion Status:
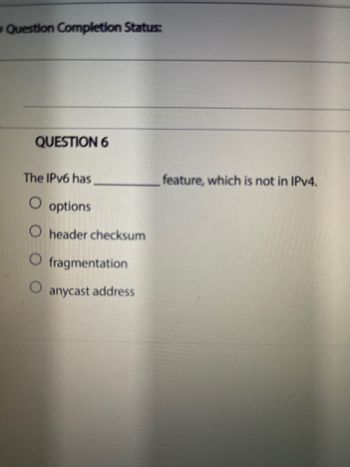
QUESTION 6
The IPv6 has
O options
O header checksum
O fragmentation
anycast address
feature, which is not in IPv4.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps with 1 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- QUESTION 16 Which of the following scenarios best describe a situation in which a user with an IP address of 169.254.11.123 cannot access the network? The DHCP server was unable to provide a leased address. The computer cannot connect because it is only configured for IPV6. There is a rogue DHCP server on the network. The address is a local host address and cannot be used to communicate with other devices. QUESTION 17 Which of these is not included in a UDP packet? Sequence number Destination address Checksum Source port QUESTION 18 is an insecure network service that runs via port 23. RDP TFTP SSH Telnetarrow_forwardYour network has an external filtering router whose IP address is 10.10.10.1. What do the following firewall rules do? Protocol TCP TCP a) None of these Source Addr 10.10.10.1 ANY b) Prevent internal communication directly with the firewall a) c) Prevent external communication directly with the firewall d) Prevent all communication directly with the firewall b) Protocol ICMP Protocol ICMP c) None of these d) Question 6 The most common ICMP command is ping, which stands for Packet Internet Groper (yes, that's what it stands for). It determines if a host is unreachable on the network. To prevent attackers from using ping to identify some of your resources, you need to establish specific firewall rules regarding ICMP packets. The tables below are specific to ICMP. Which of the following blocks ping packets from locating internal hosts? Note that the columns are different for ICMP than what you've seen for TCP. Protocol ICMP Source Port ANY ANY Source Addr ANY Source Addr ANY Source Addr…arrow_forwardCn4arrow_forward
- Computer Science Using a for loop, create a ping sweep that records all the IPv4 addresses on your home subnet. You may not use nmap in your code. This is supposed to be a bash script btw.arrow_forwardwrite the following iptables on the server to block the following traffic types originated from the attacker to the server: HTTP connection request from the attacker to the server. SSH connection request from the attacker to the server. FTP and Telnet requests ( Use single rule to block these multiple ports).arrow_forwardListen ➤ fd00::/8 is a IPv6 unique-local prefix multicast prefix broadcast prefix loopback prefix Question 66 Listen ::ffff:147.126.65.141 is a IPv6 subnet mask IPv4 address embedded in IPv6 Native IPv6 address IPv6 address embedded in IPv4arrow_forward
- 3. Complete the following Private IP Addressing information page: Private IP Addressing Information Table Subnet IP Assignable Hosts Default IP Max Class Address(es) Mask Addresses Range Barrow_forwardWrite aprogram to find the ip dotted decimal notation conversion from decimal to binary,octal and hexadecimal and vice versa also find the result of NOT and AND operation of ipv4 adresses. a. 114.34.2.8 Find the result of each operation: a. NOT (22.14.70.34) Find the result of each operation: a. (22.14.70.34) AND (255.255.0.0) ALso develop a program to find classes of ip adress and first and last address,subnet mask also. Develop in javaarrow_forwardList the classes of IPv4 addresses and their default subnet masks. In the final column list the number of host addresses per IP address and network addresses. IPv4 CLASS & ADDRESSES Default Subnet Mask Total Number of Network Addresses Possible (one number) Total Number of Host/Node Addresses Per Network Address (one number)arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education