
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
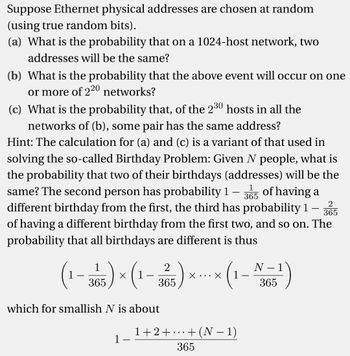
Transcribed Image Text:Suppose Ethernet physical addresses are chosen at random
(using true random bits).
(a) What is the probability that on a 1024-host network, two
addresses will be the same?
(b) What is the probability that the above event will occur on one
or more of 220 networks?
(c) What is the probability that, of the 230 hosts in all the
networks of (b), some pair has the same address?
Hint: The calculation for (a) and (c) is a variant of that used in
solving the so-called Birthday Problem: Given N people, what is
the probability that two of their birthdays (addresses) will be the
same? The second person has probability 1-3 of having a
365
different birthday from the first, the third has probability 1 365
of having a different birthday from the first two, and so on. The
probability that all birthdays are different is thus
2
(1-365)×(1-325) × × (1-N5¹)
X X
365
which for smallish N is about
1+2+
1
· + (N − 1)
365
...
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 1 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Network & Data Communcationsarrow_forwardQuestion 2 please (a,b,c,d included)arrow_forwardSkype is a well‑known VoIP system used not only for peer‑to‑peer conversations but also for audio and video conferencing involving three or more callers. Assume a video conference with a central server on Skype has N callers, and each caller generates a constant data stream at rate r bps. How many bits per second does the call initiator need to send? How many bits does each of other N‑1 callers need to send?arrow_forward
- Consider an employee using their computer to send and retrieve email at their workplace. Only Ethernet networks are used for physical connectivity, but the mail server is located on a separate network. The employee’s network and the mail server’s network are connected by a single router which also has a connection to the Internet via the workplace’s ISP. Explain how the employees email client sends and receives emails using the email server, indicating any protocols involved and where any encapsulation/decapsulation occurs as data travels between the client, local mail server, and remote mail servers.arrow_forwardWhat is the size of the multicast address space? Suppose that two multicast groups randomly choose a multicast address. What is the probability that they choose the same address? Suppose nowthat 1,000 multicast groups are ongoing at the same time and choose their multicast group addresses at random. What is the probability that they interfere with each other?arrow_forwardIn modern packet-switched networks, including the Internet, the source host segments long, application-layer messages (for example, an image or a music file) into smaller packets and sends the packets into the network. The receiver then reassembles the packets back into the original message. We refer to this process as message segmentation. Figure 1.27 illustrates the end-to-end transport of a message with and without message segmentation. Consider a message that is 8. 106 bits long that is to be sent from source to destination in Figure 1.27. Suppose each link in the figure is 2 Mbps. Ignore propagation, queuing, and processing delays. a. Consider sending the message from source to destination without message segmentation. How long does it take to move the message from the source host to the first packet switch? Keeping in mind that each switch uses store-and-forward packet switching, what is the total time to move the message from source host to destination host? b. Now suppose that…arrow_forward
- 6. Delays. A user in Madagascar, connected to the internet via a 100 Mb/s (b-bits) connection retrieves a 250 KB (B-bytes) web page from a server in Tokyo, where the page references three images of 500 KB each. Assume that the one-way propagation delay is 82 ms and that the user's access link is the bandwidth bottleneck for this connection. a. Approximately how long does it take for the page (including images) to appear on the user's screen, assuming non-persistent HTTP using a single connection at a time? (For this part, you should ignore queueing delay and transmission delays at other links in the network) How long does it take if the connection uses persistent HTTP (single connection)? b. c. Suppose that user's access router has a 4 MB buffer (B-byte) on the link from the router to the user. How much delay does this buffer add during periods when the buffer is full? d. Assume a cache rate of 45% on the information received by the user in Madagascar from the Tokyo server. How does…arrow_forwarddont dont dont post eixsting one sure sure compliant skip only answer if 100% sure else compliantarrow_forwardSuppose Alice and Bob are going to communicate using AES in CBC mode. Unfortunately Alice's message length (in bytes) is not a multiple of 16. Suppose the last block of her message is just a single zero byte. How can she pad out the last block so that she can use CBC mode? Since this needs to be a reversible operation, how does Bob recognize the padding and remove it?arrow_forward
- Computer A uses the Go-back-N ARQ protocol to send a 110 Mbytes file to computer B with a window size of 15. Given each frame carries 100K bytes data. How long does it take to send the whole file (the total time taken from A sending the first bit of the file until A receiving the last acknowledgment)? Given that the transmission rate of the link is 500 Mbps and the propagation time between A and B is 15ms. Assume no data or control frame is lost or damaged and ignore the overhead due to header and trailer.arrow_forwardIn the congestion control method of TCP we are having a connection between nodes A and node B which is called connection X. There is another TCP connection between node C and node D which is called connection Y. The initial threshold window size for connection X is 20 KB and for Y is 16 KB. Both the connections X, Y are working independently and follow the Additive increase multiplicative decrease algorithm (AIMD) for congestion control with a maximum segment size of 2 KB. The first timeout occurs at the fifth transmission in connection X and at the sixth transmission in connection Y. After every third transmission from timeout, you again encounter the timeout in both X and Y. At which transmission the connection Y reaches to the same threshold value of the connection X for the first time.arrow_forwardGive a simple heuristic for finding two paths through a network from a given source to a given destination that can survive the loss of any communication line (assuming two such paths exist). The routers are considered reliable enough, so it is not necessary to worry about the possibility of router crashes.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education