
Shared session key establishment using a Key Distribution Center (KDC). Using the following table, illustrate how Alice can initiate a secure session with Bob with the help of KDC. Here, KEKs are the long term key establishment keys used to transport the session keys across the network securely. Assume the encryption process to be as follows: Divide the key into two halves: LK and RK; Divide the plaintext into two halves: LT and RT; Then ciphertext= LC||RC where LC=LK XOR RT; and RC = RK XOR LT; where LC, RC, LT, and RT are each 4 bits; Plaintext and ciphertext are each 8 bits. For example, if plaintext=A7 (Hexa) and Key = 6D; then LC=6 ⊕ 7 = 0110 ⊕ 0111 = 0001 = 1 (Hexa); and RC = D ⊕ A = 1101 ⊕ 1010 = 0111 = 7 (Hexa); so Ciphertext = 17 (Hexa). To decryptt, it does the reverse operation: Given ciphertext of C=LC||RC, it finds plaintext T=LT||RT, by finding LT=RC ⊕ RK and RT = LC ⊕ LK. In the above example, LT = 7 ⊕D = 0111⊕1101=1010=A; RT=1 ⊕ 6 = 0001 ⊕ 0110 = 0111=7; So Plaintext=A7 (Hexa).
b. Alice and Bob now decide to use Diffie-Hellman Key Exchange (DHKE) (p. 343) with certificates. Both Alice and Bob agree on p=17 and α=4. Alice chooses a=5 and Bob chooses b=3. Answer the following.
-
- What is the public key generated by Alice?
- What is the public key generated by Bob?
- What is the computed shared key by Alice?
- What is the computed shared key by Bob?
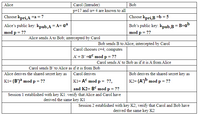
c. Man-in-the-middle attack when Alice and Bob employ Diffie-Hellman key exchange. Here, Carol is the intruder. Compute and complete the unknown entries in the exchanges shown below.

Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 5 images

- RSA cryptosystem Let p = 29 and q = 31. Then the RSA modulus n = pq = 899. We set the length of plaintext blocks to be 2 and the length of ciphertext blocks 3. Let the encryption exponent b = 29. If, for example, we want to encrypt the word live, we first divide the word into blocks of length 2, li and ve, and then find its corresponding number blocks 11 8 and 21 4. We consider these number blocks as numbers in base 26. Then we find the corresponding integers in base 10, that is 11 8 = 11 × 26 + 8 = 294 and 21 4 = 21 × 26 + 4 = 550. The integers 294 and 550 are regarded as modular numbers in Z899 and encrypted as 29429 (mod 899) = 91 and 5502⁹ (mod 899) = 492. Now write 91 and 492 in base 26 of length 3 we get 91 = 0 x 26² +3 x 26 +13 and 492 = 0 x 262 +18 × 26 +24 and the corresponding number blocks of length 3 are 0 3 13 and 0 18 24. Hen the ciphertext for live is ADNASY as 0 3 13 = ADN and 0 18 24 = ASY.arrow_forwardEncrypt with the public key you created for question 2.a, the message 14 demonstrating all your calculations. (The ciphertext will be a number too) and Provide detailed responses, ensuring thorough explanations and well-justified reasoning for each step you take.question 2a is the photoarrow_forwardIn the case of Public Key Authority It is necessary to make a request for B's public key, and the Public Key Authority must prepare a message (E(PRauth[PUB] || Request || Time1]) before sending it to A. What key A should use to decipher the message is up for debate.arrow_forward
- Public Key Authority is one such instance. The Public Key Authority must prepare a request for B's public key before delivering a message to A (E(PRauth[PUB || Request || Time 1]). It is debated if the letter A should be used to decipher the message.arrow_forwardConsider the following encryption scheme for a block cipher (using the notationfrequently used in class).y1 = ek(x1), y2 = ek(x1 ⊕ x2), y3 = ek(x1 ⊕ x2 ⊕ x3), etc.a. Describe the corresponding decryption scheme.b. Can encryption and/or decryption be run in parallel for this scheme?c. Taking into account that the operation of XOR is cheap, determinewhether or not this scheme improves on ECB mode or notarrow_forward4arrow_forward
- The hacker group Desdeia tries to break our old weak cipher which we used for the communication with the Duchess of Ligovia. It's generally known that an actual breaking of the cipher needs the reviewing a huge amount of variants which probably lasts a couple of months. Additionally we know that the reviewing of different variants needs always the same server resource. Using our intelligence sources we tried to get some information about the actual progress of breaking, but we got only some fragments: • The hacker group Desdeia uses for breaking their powerful four-core server which resources are fully dedicated to breaking process. . The actual breaking process began exactly at noon, but we don't know, on which day. . By the noon of 2nd of April, already 648,467,673 variants were successfully reviewed. Exactly at this noon, when the breaking process was already lasted for 19 days, it was attempted to double the server speed. The doubling itself was failed, but instead of it there was…arrow_forwardSuppose you generate the following RSA key pairs: •p = 37199 •q = 49031 •N = p•q = 1823904169 • (p - 1) · (q - 1) = 1823817940 •e = 65537 (for encryption) •d = 1578812933 (for decrption) Assuming a=01, b=02, ..., z=26, and we group the digits in groups of three. (ii) If you receive strings of digits from a sender: 199770170, 1288754980, 324346846, 1370682962, decrypt the message.arrow_forward
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education





