
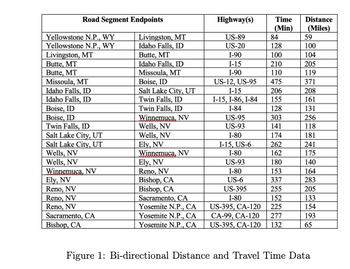
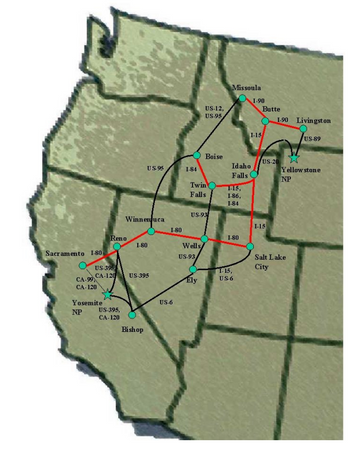
In this problem, we will consider problems of finding minimum cost paths in directed networks. You are performing logistics analysis for a company that distributes products from several distribution centers located around the US. You are considering adding a new distribution center to serve key cities in the Great Basin area. Currently, you operate single distribution center in Sacramento and serve all of the Great Basin cities from there. You are considering opening a new DC in Salt Lake City to improve service and reduce outbound transportation costs from the DC. See the map at the end of this assignment. Currently, your customers are located in all of the major and mid-sized cities represented by blue circles on the map. You have compiled data on the major highway routes that your truck fleet will use when traveling between your key customer areas and your distribution centers. Figure 1 summarizes the data. You have decided to collect both travel time and travel distance data. Travel distance will influence the costs of your truck transportation while travel time will allow you to understand you quickly you can deliver customer orders.
Question:
We would like to compare the travel distances from the current DC in Sacramento with those from the new potential DC in Salt Lake City to each other. For this problem, please use the Bellman-Ford-Moore DP
After thinking about it for a bit, you realize that you can use a single execution of the BFM algorithm to determine which cities are closer by distance (and the routes to get there) from Sacramento and which are closer to Salt Lake City. To do so, consider the following modification of the algorithm. Instead of just initializing a single start node s with a cost label v = 0 and pred = −1, you can simply give all start nodes those values.
For example:
v(SAC) = 0
v(SLC) = 0
Similarly, you should include all start nodes in the initial label update list L: L = [SAC, SLC].
Complete the execution of the BFM algorithm given this modified initialization. You can execute the iterations by hand or modify code to solve this part; if you choose to modify code, please also write down the first 5 iterations by hand where an iteration is defined by removing a node from L and updating its neighbor labels (and predecessors) as needed.
Draw your final result by showing which cities are closer to Sacramento and which are closer to Salt Lake City, labeling your network with the distances to the closer distribution center.
Step by stepSolved in 2 steps

- PET ID PET NAME PET TYPE PET AGE OWNER VISIT DATE PROCEDURE 246 ROVER DOG 12 SAM COOK JAN 13/2002MAR 27/2002APR 02/2002 01 - RABIES VACCINATION10 - EXAMINE and TREAT WOUND05 - HEART WORM TEST 298 SPOT DOG 2 TERRY KIM JAN 21/2002MAR 10/2002 08 - TETANUS VACCINATION05 - HEART WORM TEST 341 MORRIS CAT 4 SAM COOK JAN 23/2001JAN 13/2002 01 - RABIES VACCINATION01 - RABIES VACCINATION 519 TWEEDY BIRD 2 TERRY KIM APR 30/2002APR 30/2002 20 - ANNUALCHECK UP12 - EYE WASH The functional dependencies that I note are as follows: Pet ID --> Pet Name, Pet Type, Pet Age, Owner Pet ID, Visit Date --> {Visit Procedure} (the set of visit procedures), note the use of procedure codes that repeat, but are listed in their own column So, Is there are other functional dependencies? If so, what are they? If not, why not? Do you believe it would help to create additional attributes during normalization? If so, what are they? If not, justify why it's not needed. Please help me understand this.arrow_forwardCOURSE Geographical Information System Only correct answer will be upvoted. Else downvoted. DO NOT HANDWRITINGarrow_forwardHelp please for 1 abcarrow_forward
- "Decrypting an encrypted document" An employee of your company has left the organization on poor terms. Before they left they encrypted all of their important documents. This employee did not leave a decryption key and has not responded to be contacted. You have been asked by your manager to try and retrieve the data by using all means possible. Using what was learned this week how would you go about trying to retrieve the data?arrow_forwardPlease help me with this question.Thank you.arrow_forwardExplain briefly how the KIS may be used.arrow_forward
- Video-Rental LTD case study Video-Rental LTD is a small video rental store. The store lends videos to customers for a fee and purchases its videos from a local supplier. A customer wishing to borrow a video provides the empty box of the video they desire, their membership card, and payment – payment is always with the credit card used to open the customer account. The customer then returns the video to the store after watching it. If a loaned video is overdue by a day the customer's credit card is charged, and a reminder letter is sent to them. Each day after that a further card is made, and each week a reminder letter is sent. This continues until either the customer returns the video, or the charges are equal to the cost of replacing the video. New customers fill out a form with their personal details and credit card details, and the counter staff gives the new customer a membership card. Each new customer form is added to the customer file. The…arrow_forwardChurch Information System XYZ Church is a fast-growing church in Grand Rapids area. Over the past three years, since the popular Reverend Timothy Becker has taken over leadership of the congregation, the church has more than doubled in size. It now has approximately 400 registered households. Reverend John Howard has also recently been added as a second minister. Since the Church was rather small in the past, most of its records have been kept on paper forms. However, the Church’s Business Manager, Margie Roberts, has suggested to Reverend Becker that a computerized system might help the Church better meet its information needs and manage its activities. In addition to Ms. Roberts, the Church employs a part-time administrative assistant, Mabel McGregory. Mabel performs clerical duties such as filing, record keeping, answering phone calls, and typing the weekly church bulletin using WordPerfect for Windows on the Church’s only personal computer. A retiree, Leroy Stricty, is employed…arrow_forwardExplain the role of integers in modular arithmetic and its applications in computer science, particularly in cryptography and hashing algorithms.arrow_forward
 Enhanced Discovering Computers 2017 (Shelly Cashm...Computer ScienceISBN:9781305657458Author:Misty E. Vermaat, Susan L. Sebok, Steven M. Freund, Mark Frydenberg, Jennifer T. CampbellPublisher:Cengage LearningCOMPREHENSIVE MICROSOFT OFFICE 365 EXCEComputer ScienceISBN:9780357392676Author:FREUND, StevenPublisher:CENGAGE L
Enhanced Discovering Computers 2017 (Shelly Cashm...Computer ScienceISBN:9781305657458Author:Misty E. Vermaat, Susan L. Sebok, Steven M. Freund, Mark Frydenberg, Jennifer T. CampbellPublisher:Cengage LearningCOMPREHENSIVE MICROSOFT OFFICE 365 EXCEComputer ScienceISBN:9780357392676Author:FREUND, StevenPublisher:CENGAGE L Operations Research : Applications and AlgorithmsComputer ScienceISBN:9780534380588Author:Wayne L. WinstonPublisher:Brooks Cole
Operations Research : Applications and AlgorithmsComputer ScienceISBN:9780534380588Author:Wayne L. WinstonPublisher:Brooks Cole


